- Essentials
- Getting Started
- Datadog
- Datadog Site
- DevSecOps
- Serverless for AWS Lambda
- Agent
- Integrations
- Containers
- Dashboards
- Monitors
- Logs
- APM Tracing
- Profiler
- Tags
- API
- Software Catalog
- Session Replay
- Synthetic Monitoring and Testing
- Incident Management
- Database Monitoring
- Cloud Security Management
- Cloud SIEM
- Application Security Management
- Workflow Automation
- Software Delivery
- Code Security
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- OpenTelemetry
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Monitor Template
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- Service Checks
- IDE Plugins
- Community
- Guides
- Administrator's Guide
- API
- Datadog Mobile App
- CoScreen
- CoTerm
- Cloudcraft
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Reference Tables
- Sheets
- Monitors and Alerting
- Infrastructure
- Metrics
- Watchdog
- Bits AI
- Software Catalog
- Error Tracking
- Change Tracking
- Service Management
- Actions & Remediations
- Infrastructure
- Universal Service Monitoring
- Containers
- Serverless
- Network Monitoring
- Cloud Cost
- Application Performance
- APM
- Continuous Profiler
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Setting Up Postgres
- Setting Up MySQL
- Setting Up SQL Server
- Setting Up Oracle
- Setting Up Amazon DocumentDB
- Setting Up MongoDB
- Connecting DBM and Traces
- Data Collected
- Exploring Database Hosts
- Exploring Query Metrics
- Exploring Query Samples
- Exploring Recommendations
- Troubleshooting
- Guides
- Data Streams Monitoring
- Data Jobs Monitoring
- Digital Experience
- Real User Monitoring
- Product Analytics
- Synthetic Testing and Monitoring
- Continuous Testing
- Software Delivery
- CI Visibility
- CD Visibility
- Test Optimization
- Quality Gates
- DORA Metrics
- Security
- Security Overview
- Cloud SIEM
- Cloud Security Management
- Application Security Management
- Code Security
- AI Observability
- Log Management
- Observability Pipelines
- Log Management
- Administration
GitHub Pull Requests
Overview
Code Security integrates with GitHub pull requests in two ways:
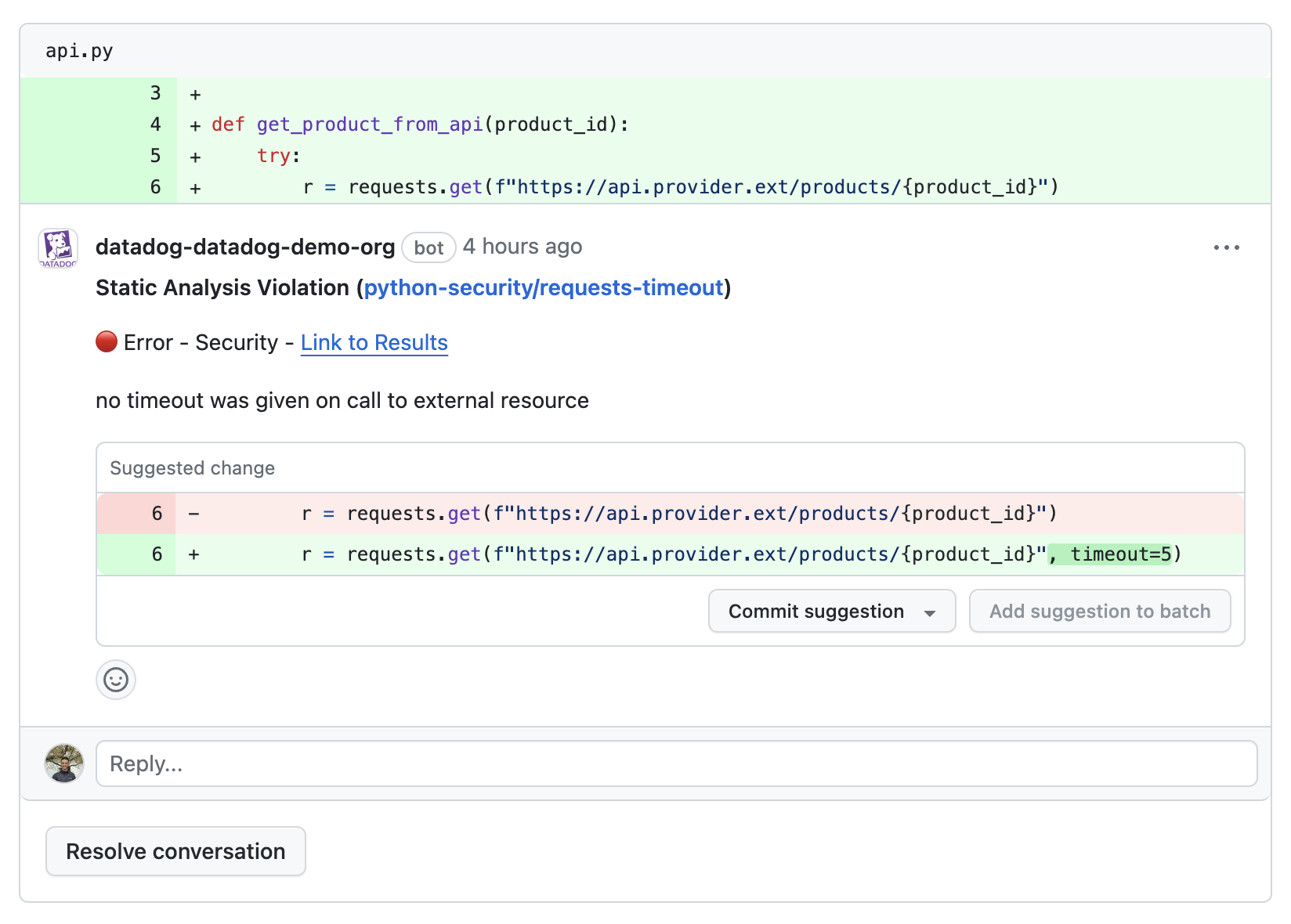
- Pull request comments to flag violations
- Open a pull request to fix an issue directly from Datadog: You can create a pull request from the UI to fix a security vulnerability or code quality issue based on Datadog’s suggested code fix. This is only available for Static Code Analysis (SAST).
To enable these features, ensure you have the required GitHub permissions (Read & Write) for your repository.
Set up Code Security for GitHub pull requests
Enable Datadog Code Security
To enable Code Security in-app, navigate to the Code Security page.
Configure a GitHub App
To use Code Security on GitHub, you can do one of the following:
- Create a GitHub App in Datadog.
- Update an existing GitHub App, if you have already created one in Datadog.
The permissions you grant to the GitHub App determine which GitHub integration features are available for setup.
Create and install a GitHub App
- In Datadog, navigate to Integrations > GitHub Applications > Add New GitHub Application.
- Fill out any required details, such as the GitHub organization name.
- Under Select Features, check the Code Security: Pull Request Review Comments box.
- Under Edit Permissions, verify that the Pull Requests permission is set to Read & Write.
- Click Create App in GitHub.
- Enter a name for your app, and submit it.
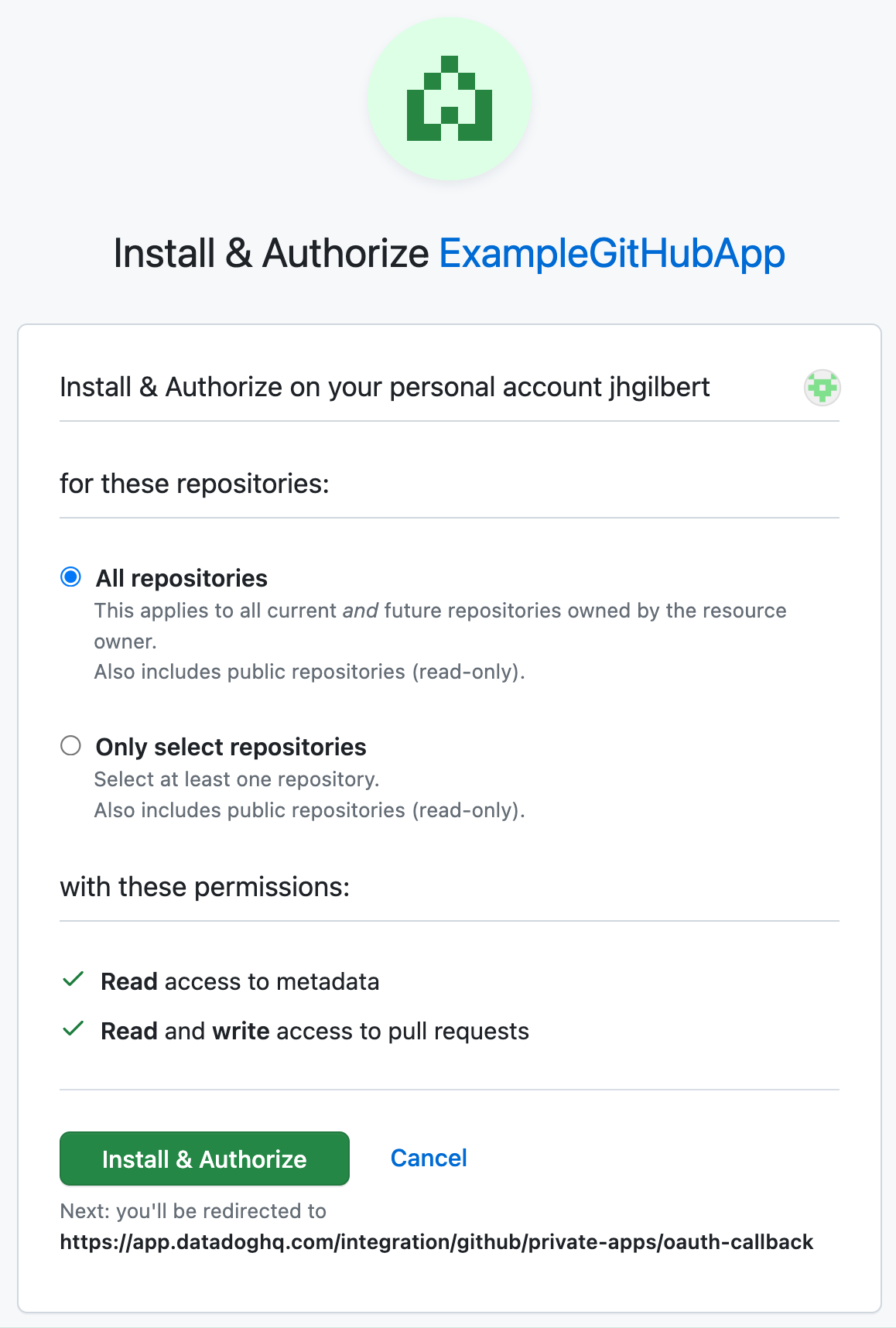
- Click Install GitHub App.
- Choose which repositories the app should be installed into, then click Install & Authorize.
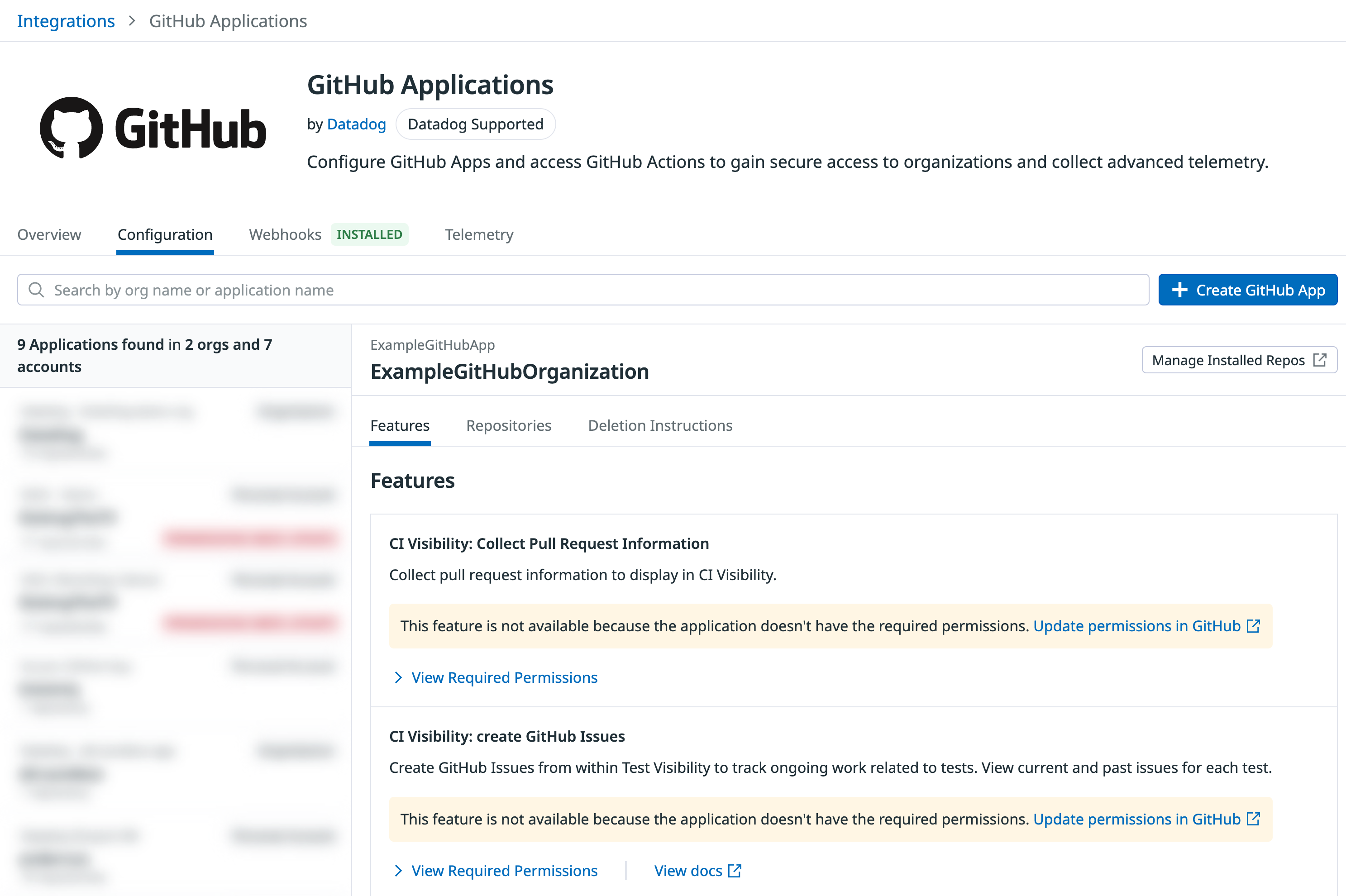
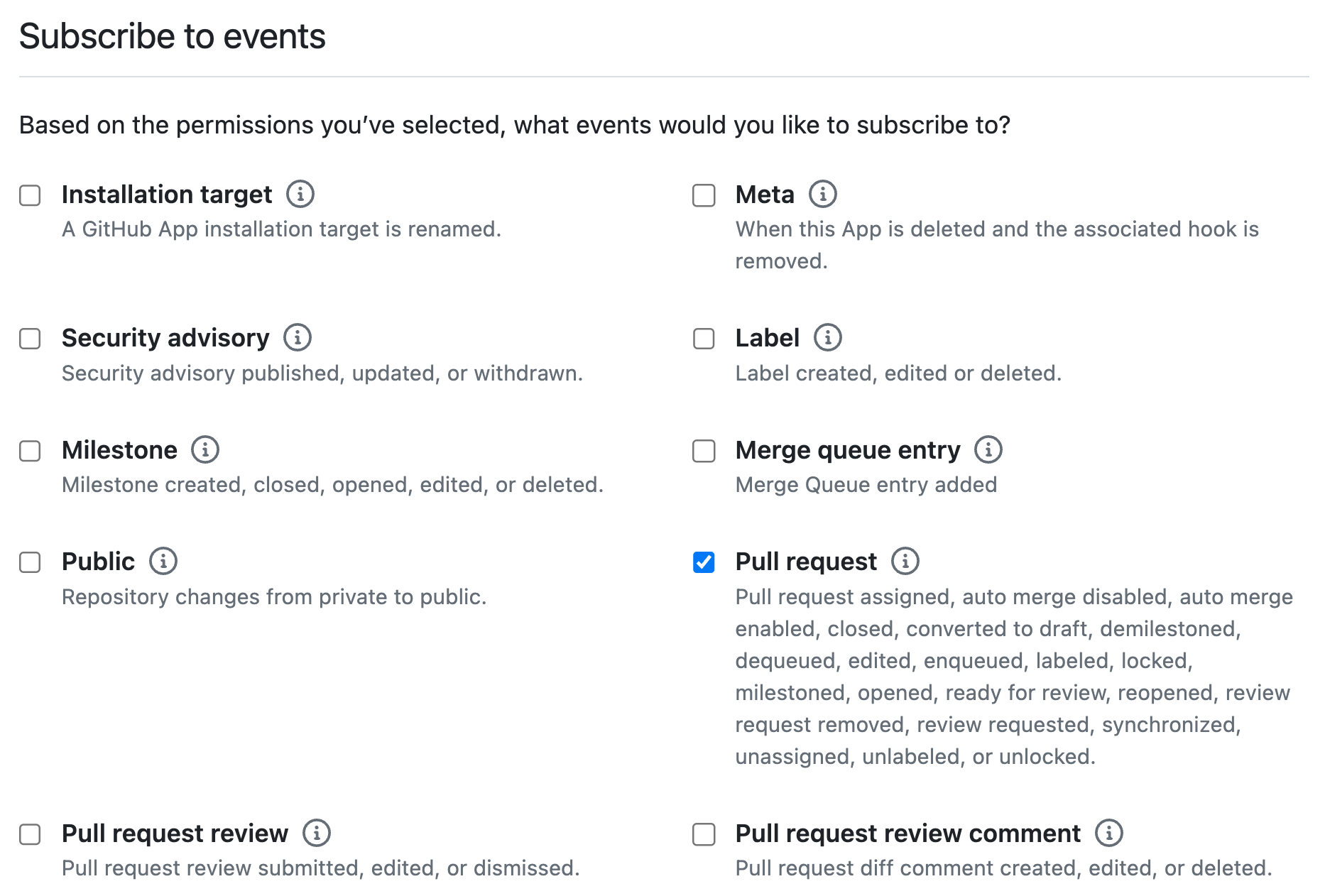
Update an existing GitHub App
- In Datadog, navigate to Integrations > GitHub Applications, and search for the GitHub App you want to use for Code Security.
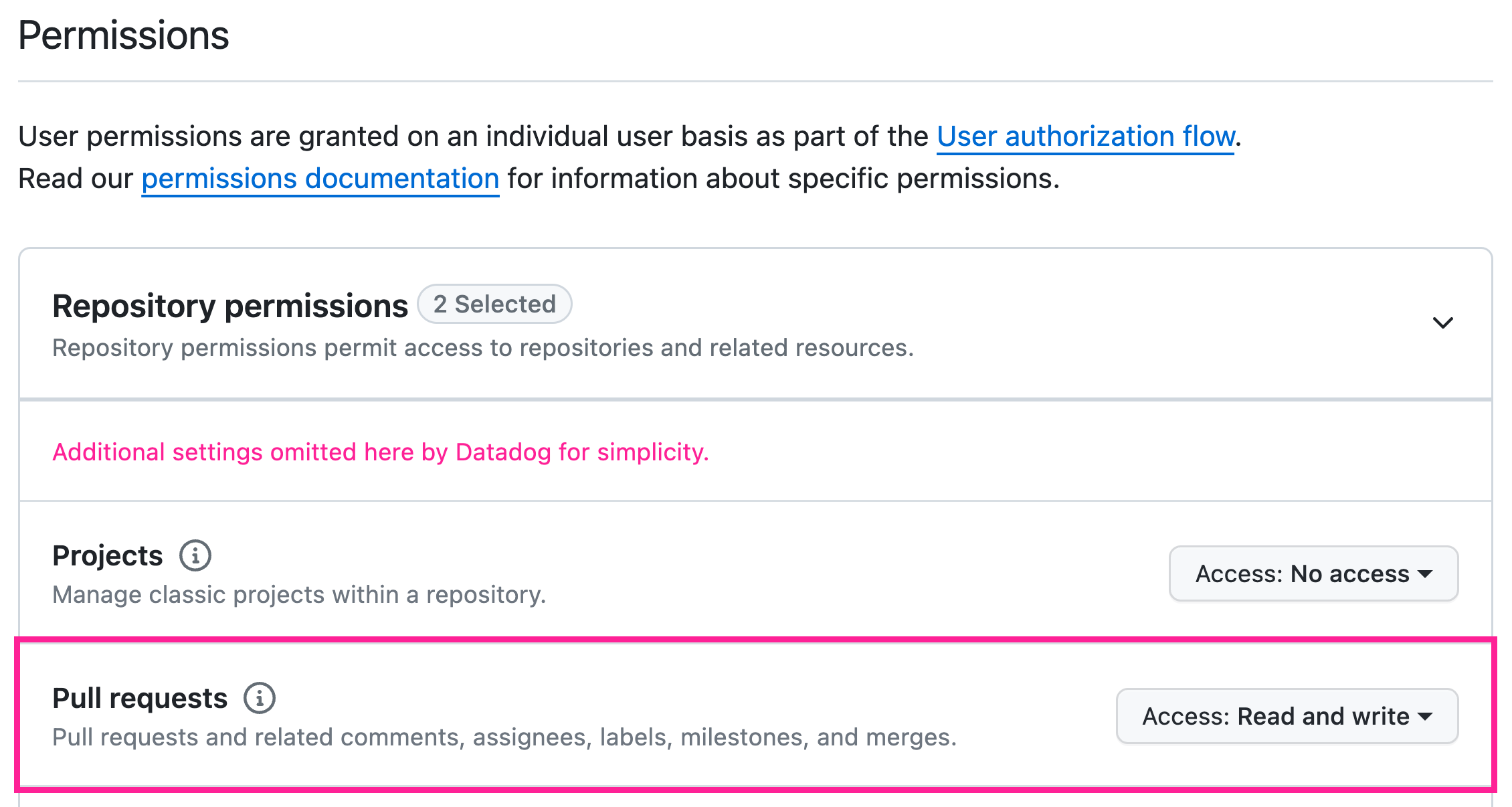
- On the Features tab, look at the Code Security: Pull Request Comments section to determine whether your GitHub App needs additional permissions. If so, click Update permissions in GitHub to edit the app settings.
- Under Repository permissions, set the Pull Requests access to Read and write.
- Under the Subscribe to events heading, check the Pull request box.
Enable Code Security PR comments for your repositories
- In Datadog, navigate to Security > Code Security > Setup.
- In Enable scanning for your repositories, select Edit next to a given repository.
- Toggle Enable Static Analyis to on.
Note: If you are using GitHub Actions to run your scans, trigger the action on push in order for comments to appear.
Configure PR comment settings for your repositories
Configure PR comment settings globally for all repositories or tailor them individually for a single repository. You can enable comments for different scan types and set minimum severity thresholds to control when PR comments appear, enabling you to exclude comments from appearing on lower-severity issues.
To configure PR comments for all repositories:
- In Datadog, navigate to Security > Code Security > Settings.
- In Repository Settings, click Global PR Comment Configuration.
- Configure the settings:
- Enable PR comments for all scan types and severities: Enable this to apply PR comments across all types and severities.
- Enable for Static Analysis (SAST): Toggle this option to enable PR comments for SAST. If enabled, specify a minimum severity threshold. Additionally, select Exclude PR comments if violations are detected in test files to prevent comments on issues found in test files.
- Enable for Infrastructure-as-Code (IaC): Toggle this option to enable PR comments for IaC. If enabled, specify a minimum severity threshold.
- Click Save.
To configure PR comments for a single repository:
- In Datadog, navigate to Security > Code Security > Settings.
- In Repository Settings, select a repository from the list.
- Configure the settings:
- Enable PR comments for all scan types and severities: Enable this to apply PR comments across all types and severities.
- Enable for Static Analysis (SAST): Toggle this option to enable PR comments for SAST. If enabled, specify a minimum severity threshold. Additionally, select Exclude PR comments if violations are detected in test files to prevent comments on issues found in test files.
- Enable for Infrastructure-as-Code (IaC): Toggle this option to enable PR comments for IaC. If enabled, specify a minimum severity threshold.
- Block all comments in this repository: Enable this to disable all comments for this repository, overriding global settings.
- Click Save Configuration.
Fix a vulnerability directly from Datadog
If your GitHub app’s Pull Requests permission is set to Read & Write, one-click remediation is enabled for all Static Code Analysis findings with an available suggested fix.
Follow these steps to fix a vulnerability and open a pull request:
- Go to Code Security > Repositories.
- Click a repository.
- On the repository’s page, click the Code Vulnerabilities or Code Quality tabs.
- Click on a violation.
- If a suggested fix is available for that violation, one-click remediation is available in the side panel in the Remediation tab.