- Essentials
- Getting Started
- Datadog
- Datadog Site
- DevSecOps
- Serverless for AWS Lambda
- Agent
- Integrations
- Containers
- Dashboards
- Monitors
- Logs
- APM Tracing
- Profiler
- Tags
- API
- Service Catalog
- Session Replay
- Continuous Testing
- Synthetic Monitoring
- Incident Management
- Database Monitoring
- Cloud Security Management
- Cloud SIEM
- Application Security Management
- Workflow Automation
- CI Visibility
- Test Visibility
- Test Impact Analysis
- Code Analysis
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- OpenTelemetry
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Recommended Monitor
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- Service Checks
- IDE Plugins
- Community
- Guides
- Administrator's Guide
- API
- Datadog Mobile App
- CoScreen
- Cloudcraft
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Sheets
- Monitors and Alerting
- Infrastructure
- Metrics
- Watchdog
- Bits AI
- Service Catalog
- API Catalog
- Error Tracking
- Service Management
- Infrastructure
- Application Performance
- APM
- Continuous Profiler
- Database Monitoring
- Data Streams Monitoring
- Data Jobs Monitoring
- Digital Experience
- Real User Monitoring
- Product Analytics
- Synthetic Testing and Monitoring
- Continuous Testing
- Software Delivery
- CI Visibility
- CD Visibility
- Test Optimization
- Code Analysis
- Quality Gates
- DORA Metrics
- Security
- Security Overview
- Cloud SIEM
- Cloud Security Management
- Application Security Management
- AI Observability
- Log Management
- Observability Pipelines
- Log Management
- Administration
Logs RBAC Permissions
Overview
Once you’ve created RBAC roles for logs, assign or remove permissions to the role.
Assign or remove permission to a role directly by updating the role on the Datadog site.
Assign or remove permission to a role directly through the Datadog Permission API.
More details about individual permissions below.
Log configuration access
logs_generate_metrics
Grants a role the ability to use the Generate Metrics feature.
This permission is global and enables both the creation of new metrics, and the edition or deletion of existing ones.
logs_write_facets
Grants a role the ability to use the Create, Edit, and Delete facets.
This permission is global and enables both the creation of new facets, and the edition or deletion of existing ones.
logs_modify_indexes
Grants a role the ability to create and modify log indexes. This includes:
- Setting indexes filters for which logs should be routed into an index.
- Setting log retention for an index.
- Granting another role the Logs Read Index Data and Logs Write Exclusion Filters permissions, scoped for a specific index.
This permission is global and enables both the creation of new indexes, and the edition of existing ones.
logs_write_exclusion_filters
Grants a role the ability to create or modify exclusion filters within an index.
This permission can be assigned either globally or restricted to a subset of indexes.
Subset of indexes:
- Remove the global permission on the role.
- Grant this permission to the role in the Index page on the Datadog site by editing an index and adding a role to the “Grant editing Exclusion Filters of this index to” field.
This configuration is only supported through the UI.
logs_write_pipelines
Grants a role the ability to create and modify log processing pipelines. This includes:
- Setting the name of the pipeline
- Setting pipelines filters for what logs should enter the processing pipeline
- Reorder pipelines
- Granting another role the Logs Write Processors permission, scoped for that pipeline
- Managing standard attributes or aliasing facets
logs_write_processors
Grants a role the ability to create, edit, or delete processors and nested pipelines.
This permission can be assigned either globally or restricted to a subset of pipelines.
Assign the role(s) in the Edit modal of a specific pipeline.
- Get the Roles ID of the role you want to assign to specific pipelines.
- Get the Permission ID for the
logs_write_processorspermission API for your region. - Grant permission to that role with the following call:
curl -X POST \
https://app.datadoghq.com/api/v2/roles/<ROLE_UUID>/permissions \
-H "Content-Type: application/json" \
-H "DD-API-KEY: <YOUR_DATADOG_API_KEY>" \
-H "DD-APPLICATION-KEY: <YOUR_DATADOG_APPLICATION_KEY>" \
-d '{
"id": "<PERMISSION_UUID>",
"type": "permissions"
}'
logs_write_archives
Grants the ability to create, edit, or delete Log Archives. This includes:
- Setting archives filters for what logs should be routed to the archive
- Setting the name of the archive
- Reordering archives
- Restricting the Logs Read Archives permission to a subset of roles.
This permission is global and enables creating new archives, and editing and deleting existing ones.
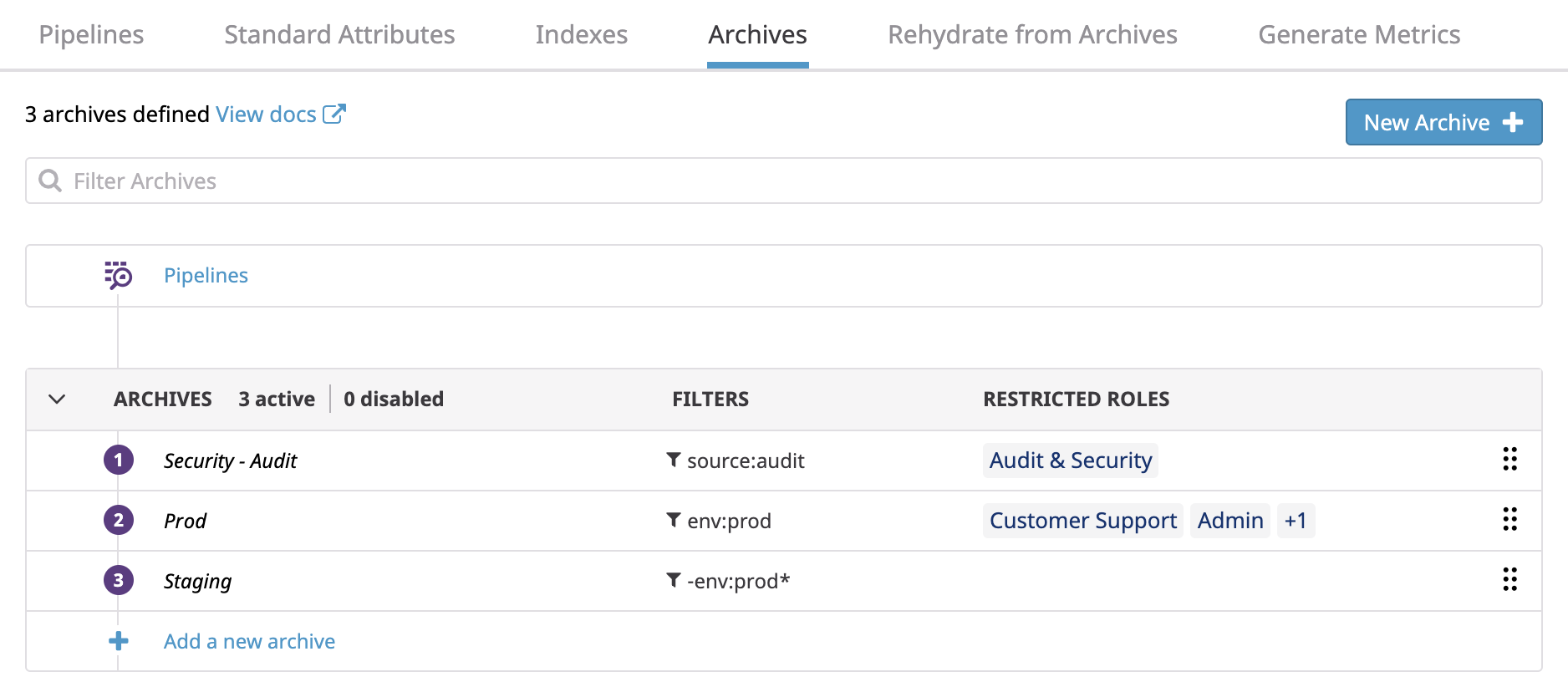
logs_read_archives
Grants the ability to access the details of the archive configuration. In conjunction with Logs Write Historical Views, this permission also grants the ability to trigger a Rehydration from Archives.
This permission can be scoped to a subset of archives. An archive with no restrictions is accessible to anyone who belongs to a role with the logs_read_archives permission. An archive with restrictions is only accessible to the users who belong to one of the registered roles, provided theses roles have the logs_read_archives permission.
In the following example, assuming all roles but Guest have the logs_read_archive permission:
- Staging is accessible to all users, except users that only belong to the
Guestrole. - Prod is accessible to all users belonging to
Customer Support. - Security-Audit is not accessible to users who belong to
Customer Support, unless they also belong toAudit & Security.
logs_write_historical_views
Grants the ability to write historical views, meaning to trigger a Log Rehydration*.
This permission is global. It enables users to trigger a rehydration for archives on which they have Logs Read Archive permission.
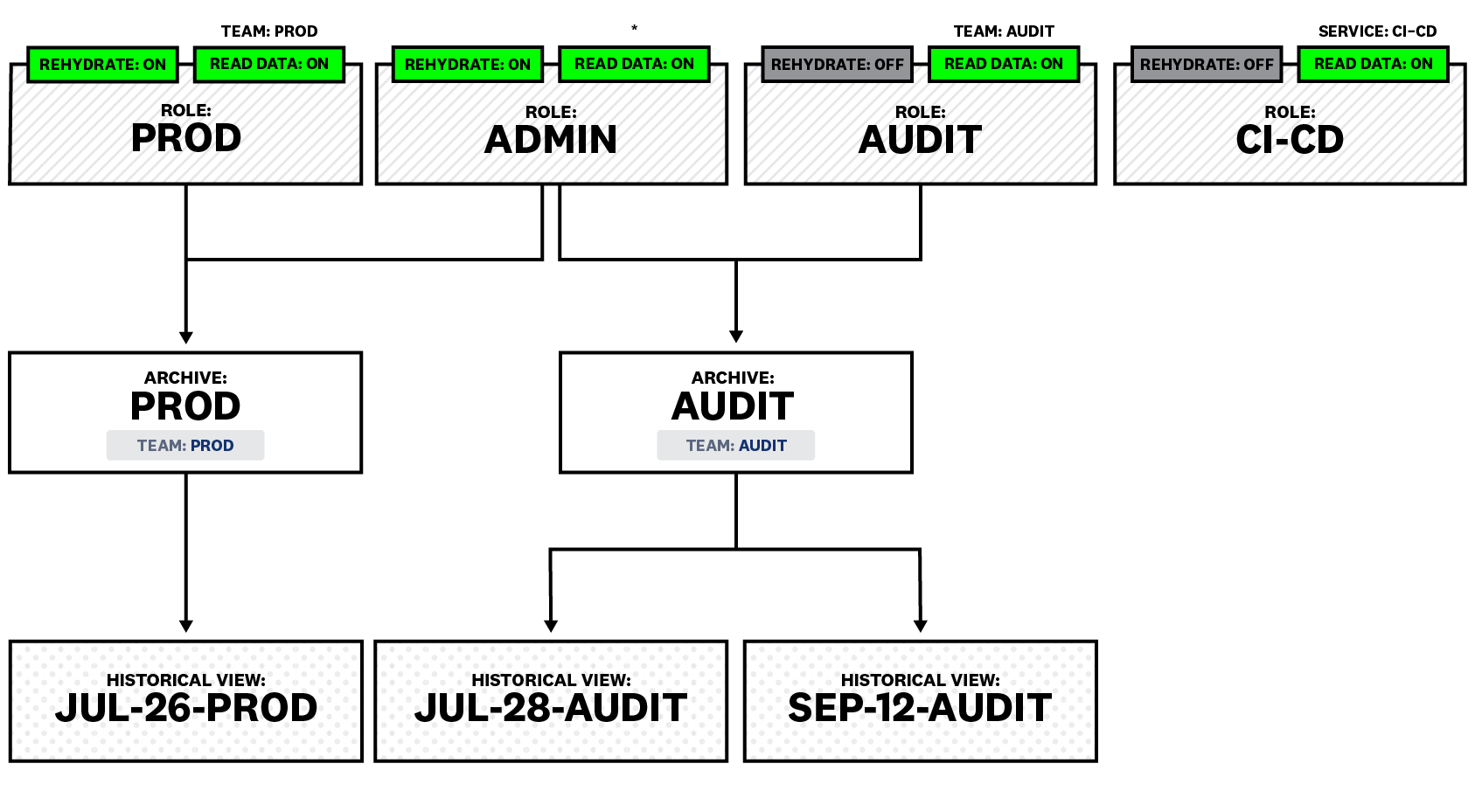
In the example above:
ADMINRole members can rehydrate from theAudit Archive, as they have the Write Historical View (Rehydrate) permission, as well as the Read Archive permission on that archive.AUDITRole members cannot rehydrate from theAudit Archive, as they do not have the Write Historical View (Rehydrate) permission.PRODRole members cannot rehydrate from theAudit Archive, as they do not have the Read Archive permission.
When assigning team:audit tags on all logs rehydrated from the Audit Archive, make sure that Audit role members who are restricted to read team:auditlogs can only access rehydrated content. For more details on how to add tags and rehydration, see the Log Archive Setup section.
For service:ci-cd logs that are rehydrated from the Prod Archive, note the following:
- If you do not use the Log Read Index Data legacy permission, these logs are accessible for
CI-CDrole members. - If you do use the Log Read Index Data legacy permission, these logs are not accessible for
CI-CDrole members, as the resulting historical view is restricted toPRODandADMINrole members.
Removed: logs_public_config_api
Datadog has removed the logs_public_config_api permission.
Five separate permissions control the ability to view, create, or modify log configuration through the Datadog API:
Log data access
Grant the following permissions to manage read access on subsets of log data:
- Logs Read Data (Recommended) offers finer grained access control by restricting a role’s access to logs matching a log restriction queries.
- Logs Read Index Data is the legacy approach to restrict data access to indexed log data on a per-index basis (it is still required to have this permission enabled to access indexed data).
logs_read_data
Read access to log data. If granted, other restrictions then apply such as logs_read_index_data or with restriction query.
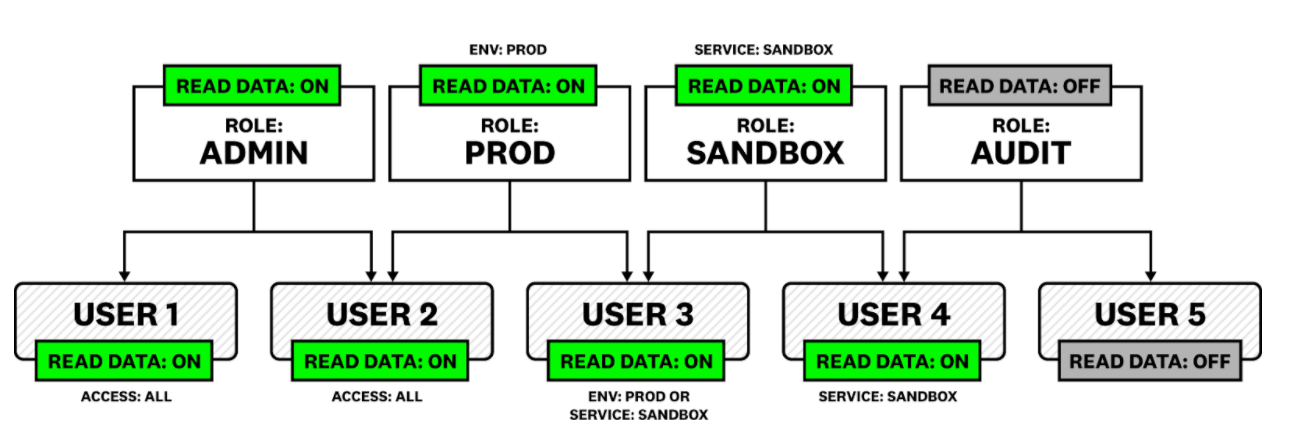
Roles are additive. If a user belongs to multiple roles, the data they have access to is the union of all the permissions from each of the roles.
Example:
- If a user belongs to a role with log read data and also belongs to a role without log read data, then they have the permission to read data.
- If a user is restricted to
service:sandboxthrough one role, and is restricted toenv:prodthrough another role, then the user can access allenv:prodandservice:sandboxlogs.
To restrict users so they see no more than logs matching a restriction query, use the Data Access page:
- Create a restriction query.
- Assign one or multiple roles to that restriction query.
- Check what roles and users are assigned to which restriction queries.
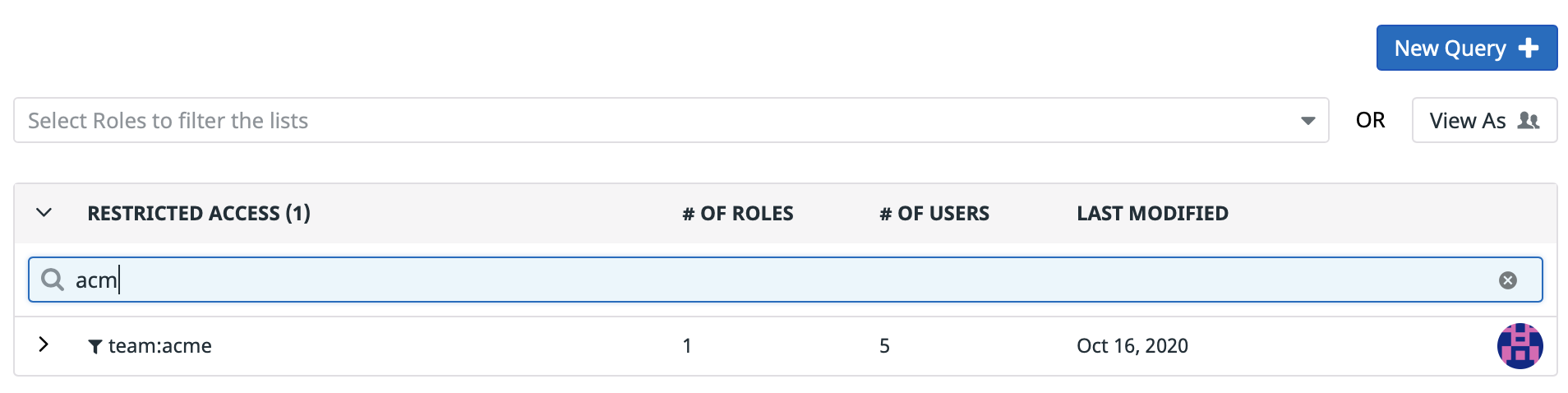
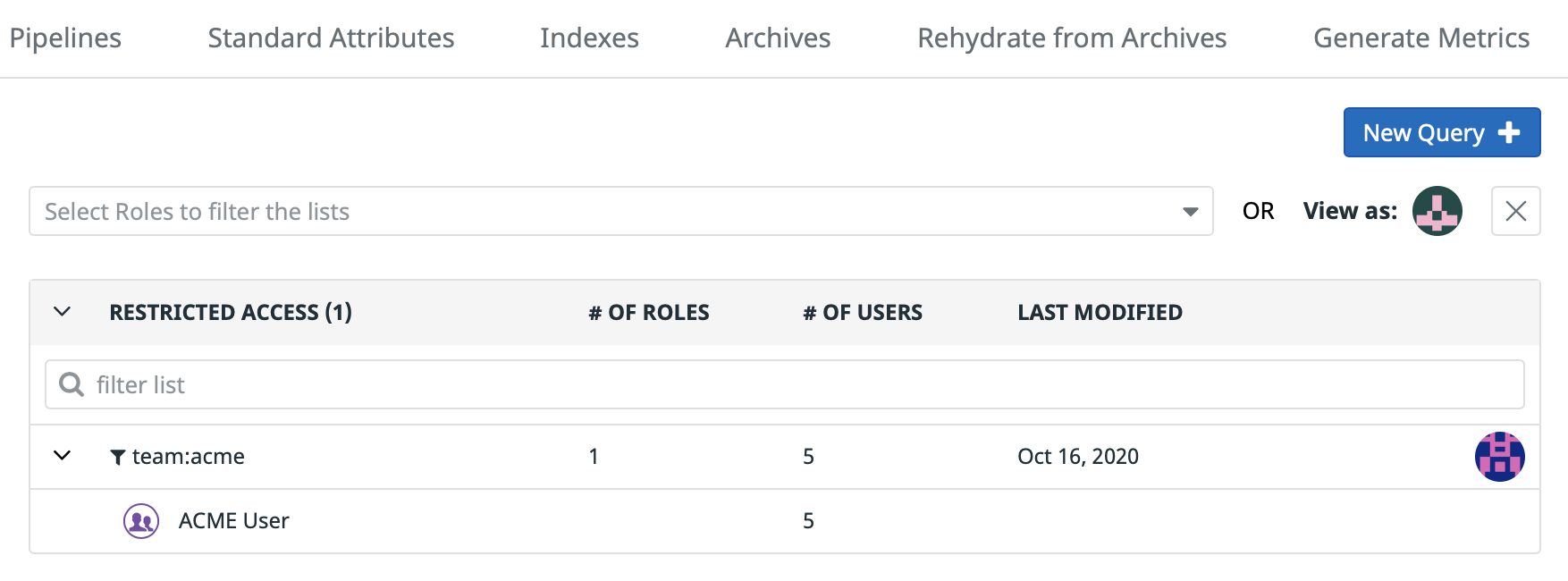
This view lists:
Restricted Accesssection: all the restriction queries, and what role(s) are attached to them,Unrestricted Accesssection: all roles that havelog_read_datapermission with no further restrictions,No Accesssection: all roles that does not have thelog_read_datapermission.
Create a restriction query
Create a new restriction query defining its query filter. The new query appears in the list of restrictions with no role attached to it.
Assign a role to a restriction query
Pick the role wherever it stands, and assign it to the intended restriction query.
Note: Keep in mind that a role can be assigned no more than one restriction query. Meaning, when you assign a role to a restriction query, it loses connection to the restriction query it was already attached to.
Likewise, use the same “Move” interaction to grant Unrestricted Access to a Role, or conversely to turn it into a No Access role.
Check restriction queries
The Data Access page displays a maximum of 50 restriction queries, and 50 roles per section. If you have more roles and restriction queries than the page can display, use the filters to scope this view down:
with the restriction query filter:
with the role filter:
with the user filter, which is a convenient way to see what a specific user belonging to multiple roles actually has access to:
Revoke or grant this permission from a role with the Roles API. Use Restriction Queries to scope the permission to a subset of Log Data.
Legacy permissions
These permissions are globally enabled by default for all users.
Logs Read Data permission comes on top of these legacy permissions. For instance, say a user is restricted to the query service:api.
- If this user has scoped Read Index Data permission on
auditanderrorsindexes, this user only seesservice:apilogs within these indexes. - If this user has livetail permission, this user only sees
service:apilogs in the livetail.
logs_read_index_data
Grants a role read access on some number of log indexes. Can be set either globally or limited to a subset of log indexes.
To scope this permission to a subset of indexes, first remove the logs_read_index_data and logs_modify_indexes permissions on the role. Then:
Grant this role access to the index in Configuration page.
- Get the Roles ID of the role you want to assign to specific pipelines.
- Get the Permission ID for the
logs_write_processorspermission API for your region. - Grant permission to that role with the following call:
curl -X POST \
https://app.datadoghq.com/api/v2/roles/<ROLE_UUID>/permissions \
-H "Content-Type: application/json" \
-H "DD-API-KEY: <YOUR_DATADOG_API_KEY>" \
-H "DD-APPLICATION-KEY: <YOUR_DATADOG_APPLICATION_KEY>" \
-d '{
"id": "<PERMISSION_UUID>",
"type": "permissions"
}'
logs_live_tail
Grants a role the ability to use the Live Tail feature.
This permission is global, and grants access to the livetail regardless of Log Read Index Data permission.
Further reading
Additional helpful documentation, links, and articles:
*Log Rehydration is a trademark of Datadog, Inc.