- Essentials
- Getting Started
- Agent
- API
- APM Tracing
- Containers
- Dashboards
- Database Monitoring
- Datadog
- Datadog Site
- DevSecOps
- Incident Management
- Integrations
- Logs
- Monitors
- OpenTelemetry
- Profiler
- Session Replay
- Security
- Serverless for AWS Lambda
- Software Catalog
- Software Delivery
- Synthetic Monitoring and Testing
- Tags
- Workflow Automation
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Monitor Template
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- Service Checks
- IDE Plugins
- Community
- Guides
- OpenTelemetry
- Administrator's Guide
- API
- Partners
- Datadog Mobile App
- DDSQL Reference
- CoScreen
- CoTerm
- Cloudcraft (Standalone)
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Reference Tables
- Sheets
- Monitors and Alerting
- Metrics
- Watchdog
- Bits AI
- Internal Developer Portal
- Error Tracking
- Change Tracking
- Service Management
- Actions & Remediations
- Infrastructure
- Cloudcraft
- Resource Catalog
- Universal Service Monitoring
- Hosts
- Containers
- Processes
- Serverless
- Network Monitoring
- Cloud Cost
- Application Performance
- APM
- APM Terms and Concepts
- Application Instrumentation
- APM Metrics Collection
- Trace Pipeline Configuration
- Correlate Traces with Other Telemetry
- Trace Explorer
- Recommendations
- Code Origins for Spans
- Service Observability
- Endpoint Observability
- Dynamic Instrumentation
- Live Debugger
- Error Tracking
- Data Security
- Guides
- Troubleshooting
- Continuous Profiler
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Setting Up Postgres
- Setting Up MySQL
- Setting Up SQL Server
- Setting Up Oracle
- Setting Up Amazon DocumentDB
- Setting Up MongoDB
- Connecting DBM and Traces
- Data Collected
- Exploring Database Hosts
- Exploring Query Metrics
- Exploring Query Samples
- Exploring Database Schemas
- Exploring Recommendations
- Troubleshooting
- Guides
- Data Streams Monitoring
- Data Jobs Monitoring
- Digital Experience
- Real User Monitoring
- Synthetic Testing and Monitoring
- Continuous Testing
- Product Analytics
- Software Delivery
- CI Visibility
- CD Visibility
- Test Optimization
- Quality Gates
- DORA Metrics
- Security
- Security Overview
- Cloud SIEM
- Code Security
- Cloud Security
- App and API Protection
- Workload Protection
- Sensitive Data Scanner
- AI Observability
- Log Management
- Observability Pipelines
- Log Management
- Administration
Datadog FIPS Compliance
The Datadog FIPS Agent is available only in the US1-FED region.
The FIPS Agent is a flavor of the Datadog Agent that natively supports Federal Information Processing Standards (FIPS) compliance. The FIPS Agent’s compliance is based on its use of the FIPS 140-2 validated Cryptographic Module - Certificate #4282. See the related security policy for information about validated operating environments and restrictions. The FIPS Agent also includes limited support for integrations that need to collect observability data that is external to the host.
It is your responsibility to ensure operating environment compliance with the security policy and wider FIPS guidance.
Supported platforms and limitations
Supported platforms:
| Bare metal and VMs | RHEL >= 7 Debian >= 8 Ubuntu >= 14.04 SUSE >= 12 Windows Server >= 2016 Windows >= 10 |
| Cloud and container | Amazon ECS AWS EKS (Helm) Docker |
Supported products (Agent 7.65.0 and above):
- Metrics
- Logs
- APM traces
- APM profiles
- Processes
- Orchestrator Explorer
- Runtime Security
- Serverless Monitoring
The Datadog FIPS Agent does not support the following:
- Communication between Cluster Agent and Node Agents
- Outbound communication to anything other than GovCloud
- Datadog DDOT Collector1
Prerequisites
- A non-containerized Linux host.
- Your Linux OS must be in FIPS-compliant mode. See your OS vendor’s documentation on what steps are required to meet this requirement.
- FIPS-compliant storage backing the host file system.
- A non-containerized Windows host.
- Windows must be in FIPS-compliant mode.
- FIPS-compliant storage backing the host file system.
Ensure your AWS setup is FIPS compliant. This includes, but is not limited to, the following requirements:
- Use a FIPS-compliant region (for example, AWS GovCloud)
Ensure your AWS setup is FIPS compliant. This includes, but is not limited to, the following requirements:
- Use a FIPS-compliant region (for example, AWS GovCloud)
- Configure AWS compute services (EC2 or Fargate) in FIPS mode
- Use FIPS-compliant storage for your ECS tasks
Ensure your AWS setup is FIPS compliant. This includes, but is not limited to, the following requirements:
- Use a FIPS-compliant region (for example, AWS GovCloud)
- Configure EKS worker nodes in FIPS mode
- Use FIPS-compliant storage for your EKS worker nodes
In addition to the Operating System (OS) requirements above:
- You must have access to a FIPS-compliant Datadog environment (US1-FED).
- The FIPS Agent is only available on Agent versions 7.65.0 and above.
Installation
Install the Agent with FIPS support.
Note: FIPS support is only available on Agent versions 7.65.0 and above:
If you’re using the Agent install script, specify the
DD_AGENT_FLAVOR="datadog-fips-agent"environment variable in your installation command. For example:DD_SITE="ddog-gov.com" DD_API_KEY="MY_API_KEY" DD_AGENT_FLAVOR="datadog-fips-agent" … bash -c "$(curl -L https://s3.amazonaws.com/dd-agent/scripts/install_script_agent7.sh)"If you’re installing with a package, follow the instructions to install the latest
datadog-fips-agentpackage available for your platform.Add
GOFIPS=1to your Datadog environment variables, reload all service units, and restart the Datadog Agent service (datadog-agent.service). For example, if your host is using systemd:echo "GOFIPS=1" | sudo tee -a /etc/datadog-agent/environment systemctl daemon-reload systemctl restart 'datadog-agent*'
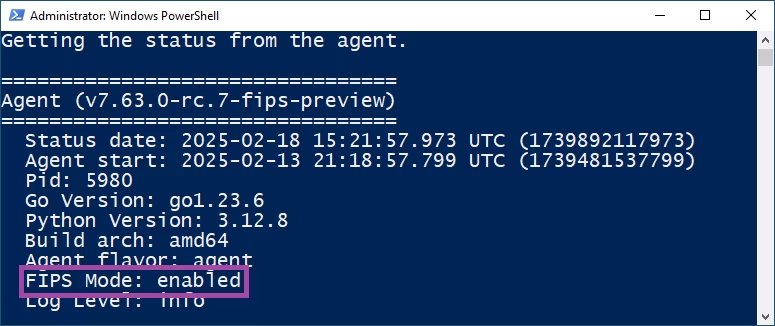
Run the
datadog-agent statuscommand and make sure you seeFIPS Mode: enabledin the status output.<div class="shortcode-wrapper shortcode-img expand"><figure class="text-center"><a href="https://datadog-docs-staging.imgix.net/images/agent/fips-linux.9b9ee1a25073301cb634384630327924.png?fit=max&auto=format" class="pop" data-bs-toggle="modal" data-bs-target="#popupImageModal"><picture class="" style="width:100%;" > <img class="img-fluid" srcset="https://datadog-docs-staging.imgix.net/images/agent/fips-linux.9b9ee1a25073301cb634384630327924.png?auto=format" style="width:100%;" alt="Agent status command output with FIPS Mode enabled - Linux" /> </picture></a></figure> </div>
Follow the Windows instructions to uninstall any existing Datadog Agent on the machine.
Run the command below to install the FIPS Agent, replacing
DATADOG_API_KEYwith your API key:Note: FIPS support is only available on Agent versions 7.65.0 and above:
$p = Start-Process -Wait -PassThru msiexec -ArgumentList '/qn /i https://windows-agent.datadoghq.com/datadog-fips-agent-7-latest.amd64.msi /log C:\Windows\SystemTemp\install-datadog.log APIKEY="<DATADOG_API_KEY>" SITE="ddog-gov.com"'
if ($p.ExitCode -ne 0) {
Write-Host "msiexec failed with exit code $($p.ExitCode) please check the logs at C:\Windows\SystemTemp\install-datadog.log" -ForegroundColor Red
}Run the Agent
statuscommand and make sure you seeFIPS Mode: enabledin the status output.& "$env:ProgramFiles\Datadog\Datadog Agent\bin\agent.exe" status
Note: The program name for the FIPS Agent in Add or Remove Programs is “Datadog FIPS Agent.”
For AWS Lambda FIPS compliance, follow the instructions in the AWS Lambda FIPS Compliance documentation.
When following the ECS installation instructions, make sure to use these FIPS-specific configuration values for your Task Definition:
- Set
image(incontainerDefinitionsobject) topublic.ecr.aws/datadog/agent:7-fips - Set
DD_SITEenvironment variable toddog-gov.com
When following the Datadog Agent installation on Kubernetes instructions, make sure to include these FIPS-specific configuration values depending on your chosen installation method (in datadog-agent.yaml file):
For the Datadog Operator:
datadog:
site: "ddog-gov.com"
useFIPSAgent: true
For the Datadog Helm Chart:
spec:
global:
site: "ddog-gov.com"
useFIPSAgent: true
Security and hardening
You, the Datadog customer, are responsible for host security and hardening.
Security considerations:
- While the Datadog images provided are constructed with security in mind, they have not been evaluated against CIS benchmark recommendations or DISA STIG standards.
- If you rebuild, reconfigure, or modify the Datadog FIPS Agent to fit your deployment or testing needs, you might end up with a technically working setup, but Datadog cannot guarantee FIPS compliance if the Datadog FIPS Agent is not used exactly as explained in the documentation.
- If you did not follow the installation steps listed above exactly as documented, Datadog cannot guarantee FIPS compliance.
Further reading
Additional helpful documentation, links, and articles: