- Principales informations
- Getting Started
- Datadog
- Site Datadog
- DevSecOps
- Serverless for AWS Lambda
- Agent
- Intégrations
- Conteneurs
- Dashboards
- Monitors
- Logs
- Tracing
- Profileur
- Tags
- API
- Service Catalog
- Session Replay
- Continuous Testing
- Surveillance Synthetic
- Incident Management
- Database Monitoring
- Cloud Security Management
- Cloud SIEM
- Application Security Management
- Workflow Automation
- CI Visibility
- Test Visibility
- Intelligent Test Runner
- Code Analysis
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Intégrations
- OpenTelemetry
- Développeurs
- Authorization
- DogStatsD
- Checks custom
- Intégrations
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Recommended Monitor
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- Checks de service
- IDE Plugins
- Communauté
- Guides
- API
- Application mobile
- CoScreen
- Cloudcraft
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Alertes
- Infrastructure
- Métriques
- Watchdog
- Bits AI
- Service Catalog
- API Catalog
- Error Tracking
- Service Management
- Infrastructure
- Universal Service Monitoring
- Conteneurs
- Sans serveur
- Surveillance réseau
- Cloud Cost
- Application Performance
- APM
- Profileur en continu
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Configuration de Postgres
- Configuration de MySQL
- Configuration de SQL Server
- Setting Up Oracle
- Setting Up MongoDB
- Connecting DBM and Traces
- Données collectées
- Exploring Database Hosts
- Explorer les métriques de requête
- Explorer des échantillons de requêtes
- Dépannage
- Guides
- Data Streams Monitoring
- Data Jobs Monitoring
- Digital Experience
- RUM et Session Replay
- Product Analytics
- Surveillance Synthetic
- Continuous Testing
- Software Delivery
- CI Visibility
- CD Visibility
- Test Visibility
- Exécuteur de tests intelligent
- Code Analysis
- Quality Gates
- DORA Metrics
- Securité
- Security Overview
- Cloud SIEM
- Cloud Security Management
- Application Security Management
- AI Observability
- Log Management
- Pipelines d'observabilité
- Log Management
- Administration
Automate open source risk reduction with Datadog SCA
Cette page n'est pas encore disponible en français, sa traduction est en cours.
Si vous avez des questions ou des retours sur notre projet de traduction actuel, n'hésitez pas à nous contacter.
Si vous avez des questions ou des retours sur notre projet de traduction actuel, n'hésitez pas à nous contacter.
Datadog Software Composition Analysis (SCA) enables you to easily identify, prioritize, and resolve vulnerabilities and other risks in the third-party, open source software (OSS) libraries used in your application services.
This topic describes how to use SCA to view and resolve vulnerabilities and risks in your open source libraries.
Benefits of SCA
SCA addresses the following risks associated with open source libraries:
- Security vulnerabilities: Known vulnerabilities, particularly those with CVEs (Common Vulnerabilities and Exposures).
- Malware: Malicious actors using techniques like typosquatting and hijacking to distribute malware.
- Licensing issues: Non-compliance with varied open source licenses can lead to legal problems.
- Deprecated libraries: Using outdated components can introduce unpatched vulnerabilities and compatibility issues.
- Unmaintained libraries: Lack of active development can lead to unresolved bugs and security flaws.
- Poor security hygiene: Some projects lack best practices in security, such as proper code reviews.
Datadog SCA helps automate risk reduction processes, enhancing productivity in the following ways:
- Integration across development lifecycle: Analyzes open source and third-party components, providing a detailed library catalog.
- Continuous evaluation: Offers real-time visibility into deployed services, enhancing the security posture by enabling prioritization of vulnerabilities in sensitive environments.
- Collaboration: Breaks down silos and involves more teams in security (DevOps, Operations, SREs), fostering a culture of collaboration.
View the libraries used in your services
The Libraries catalog displays the libraries and versions used across your services.
The catalog surfaces all library details using several public data sources (GuardDog, NIST, osv.dev, OpenSSF scores, etc.) and private data sources (including Datadog’s Security Research group).
To use the Libraries catalog, see Libraries or select Security > Application Security > Catalogs > Libraries.
In the Libraries catalog, you can:
- View all of the libraries used in each of your services.
- In View, select Runtime to view libraries detected at runtime.
- In View, select Static to view libraries detected in your source code repositories.
- Use the Vulnerability Severity facet to filter libraries according to vulnerability rating.
- View the source repository for each library.
- See library details such as the current version used in a service and the latest version available.
- View the OpenSSF Scorecard for the library.
View vulnerabilities and risks in libraries
In the Vulnerabilities explorer, you can view the vulnerabilities and risks for the libraries you are using.
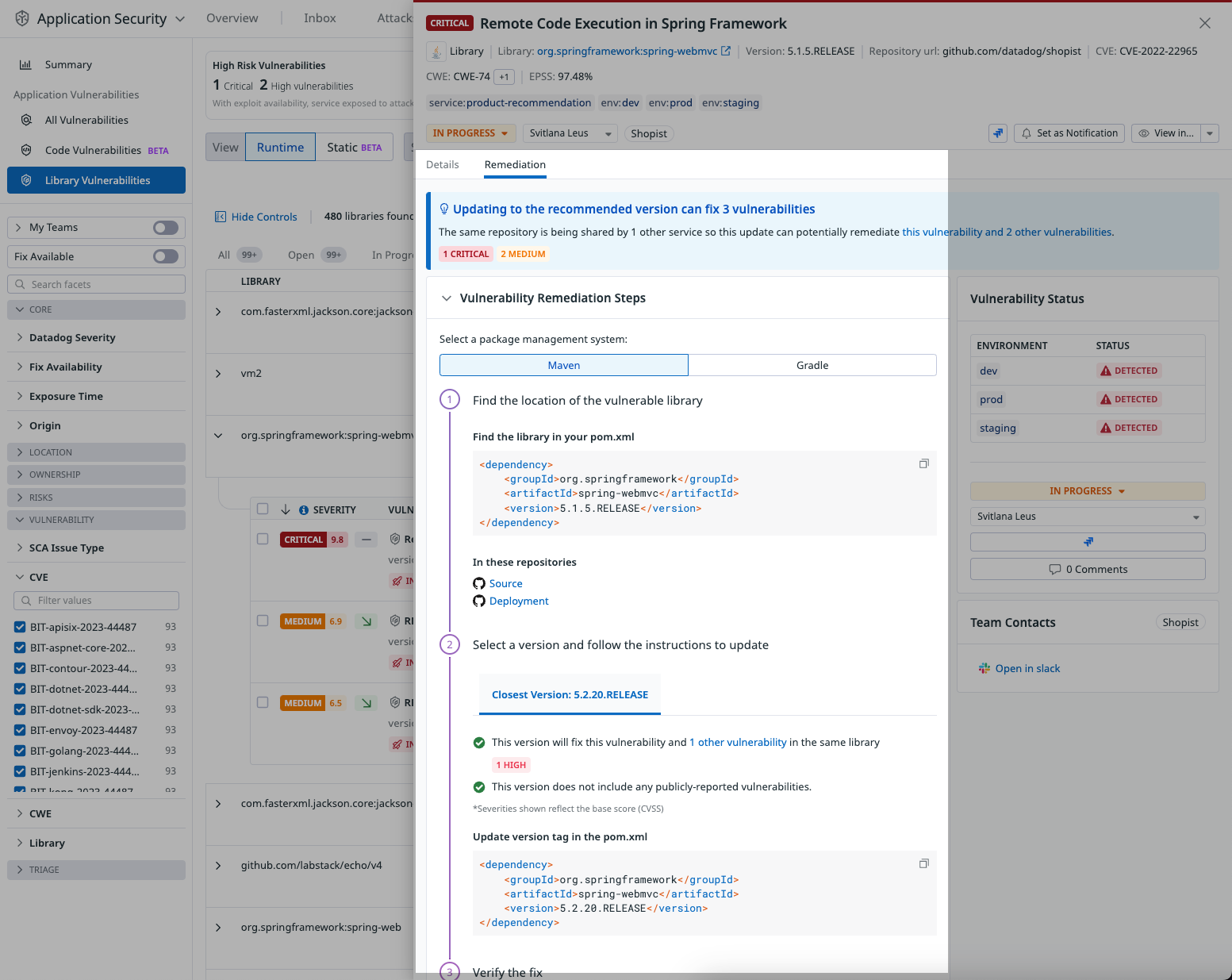
Library vulnerabilities
A library vulnerability is a security bug in a library.
To view your library vulnerabilities, see Library Vulnerabilities or navigate to Security > Vulnerabilities > Library Vulnerabilities.
In Library Vulnerabilities, you can:
- Use the Vulnerability facet to view different vulnerability types.
- For example, every vulnerability has an associated CVE ID, displayed in the explorer and each library detail. You can use the Vulnerability facet to sort by CVE ID.
- View vulnerability details like:
- Explanation
- Service and environment
- First and last detection
- Window of exposure
- Severity breakdown
- Remediation steps
Library risks
A library’s risks are a group of weaknesses that are not directly tied to security. For example, the library is deprecated, the licensing of the project is too restrictive, or the team follows poor security practices.
To view your library risks, see Library Risks or select Security > Vulnerabilities > Library Risks.
In Library Risks, you can:
- In View, select Runtime to view risks detected at runtime.
- In View, select Static to view risks detected in your source code repositories.
- View risk details like:
- Explanation
- Service and environment
- First and last detection
- Window of exposure
- Severity breakdown
Best practices to mitigate risks
To mitigate risks, follow these best practices:
- Due diligence: Evaluate open source projects thoroughly before use.
- Stay updated: Regularly update components and subscribe to security advisories.
- Vulnerability management: Establish processes to triage and remediate vulnerabilities.
- Measurement: Track metrics to understand and improve the security posture over time.
Further reading
Documentation, liens et articles supplémentaires utiles: