- Principales informations
- Getting Started
- Datadog
- Site Datadog
- DevSecOps
- Serverless for AWS Lambda
- Agent
- Intégrations
- Conteneurs
- Dashboards
- Monitors
- Logs
- Tracing
- Profileur
- Tags
- API
- Service Catalog
- Session Replay
- Continuous Testing
- Surveillance Synthetic
- Incident Management
- Database Monitoring
- Cloud Security Management
- Cloud SIEM
- Application Security Management
- Workflow Automation
- CI Visibility
- Test Visibility
- Intelligent Test Runner
- Code Analysis
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Intégrations
- OpenTelemetry
- Développeurs
- Authorization
- DogStatsD
- Checks custom
- Intégrations
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Recommended Monitor
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- Checks de service
- IDE Plugins
- Communauté
- Guides
- API
- Application mobile
- CoScreen
- Cloudcraft
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Alertes
- Infrastructure
- Métriques
- Watchdog
- Bits AI
- Service Catalog
- API Catalog
- Error Tracking
- Service Management
- Infrastructure
- Universal Service Monitoring
- Conteneurs
- Sans serveur
- Surveillance réseau
- Cloud Cost
- Application Performance
- APM
- Profileur en continu
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Configuration de Postgres
- Configuration de MySQL
- Configuration de SQL Server
- Setting Up Oracle
- Setting Up MongoDB
- Connecting DBM and Traces
- Données collectées
- Exploring Database Hosts
- Explorer les métriques de requête
- Explorer des échantillons de requêtes
- Dépannage
- Guides
- Data Streams Monitoring
- Data Jobs Monitoring
- Digital Experience
- RUM et Session Replay
- Product Analytics
- Surveillance Synthetic
- Continuous Testing
- Software Delivery
- CI Visibility
- CD Visibility
- Test Visibility
- Exécuteur de tests intelligent
- Code Analysis
- Quality Gates
- DORA Metrics
- Securité
- Security Overview
- Cloud SIEM
- Cloud Security Management
- Application Security Management
- AI Observability
- Log Management
- Pipelines d'observabilité
- Log Management
- Administration
Proactively block crypto mining threats with Active Protection
Cette page n'est pas encore disponible en français, sa traduction est en cours.
Si vous avez des questions ou des retours sur notre projet de traduction actuel, n'hésitez pas à nous contacter.
Si vous avez des questions ou des retours sur notre projet de traduction actuel, n'hésitez pas à nous contacter.
Please contact Datadog Support to enable Active Protection.
CSM Threats Active Protection is in beta.
This topic explains how to use the CSM Threats Active Protection feature to block crypto mining threats automatically.
By default, all OOTB Agent threat detection rules are enabled and actively monitoring for crypto threats.
Active Protection enables you to proactively block and terminate crypto mining threats identified by the Datadog Agent threat detection rules.
Active Protection streamlines threat detection and targeted response, resulting in risk reduction, allowing DevSecOps and security teams to tackle evolving crypto mining threats effectively:
- Security decides which threats warrant an automated action.
- DevOps decides which applications and resources are resilient enough to withstand targeted protection.
The end result is crypto mining threat detection followed by immediate surgical mitigation against high confidence, true positive attacks.
RBAC for Active Protection
Here are some important [role and permissions][11] to use for custom rules and Active Protection RBAC:
- The
security_monitoring_cws_agent_rules_actionspermission can be used to turn on and configure the Active Protection feature.- To use the
security_monitoring_cws_agent_rules_actionspermission, a user with the Datadog Admin role must create a role containing thesecurity_monitoring_cws_agent_rules_actionspermission and then add only those users that manage Active Protection to this role.
- To use the
- The Datadog Standard role enables users to create/update a custom rule by default, as long as the operation does not change the protection settings on the rule.
Protection options
You have three options for Agent rules:
- Monitoring: This is the default setting for enabled rules, regardless of whether Active Protection is enabled. The Agent monitors for the enabled rule and displays detections in Signals.
- Blocking:
- Blocking is available when Active Protection is enabled. Blocking is available on select OOTB rules that have high confidence, true positives.
- The Agent monitors for the enabled rule, terminates the corresponding actions instantly, and displays detections in Signals.
- Disabled: The Agent does not monitor for the rule events and does not send detections to the Datadog backend.
Blocking is applied to all threats detected after blocking is enabled. Blocking is not retroactive.
Active Protection availability
Active Protection is enabled at the organization level.
Active Protection blocking functionality is available in a subset of the OOTB Agent rules only. Agent rule monitoring runs regardless of whether Active Protection is enabled.
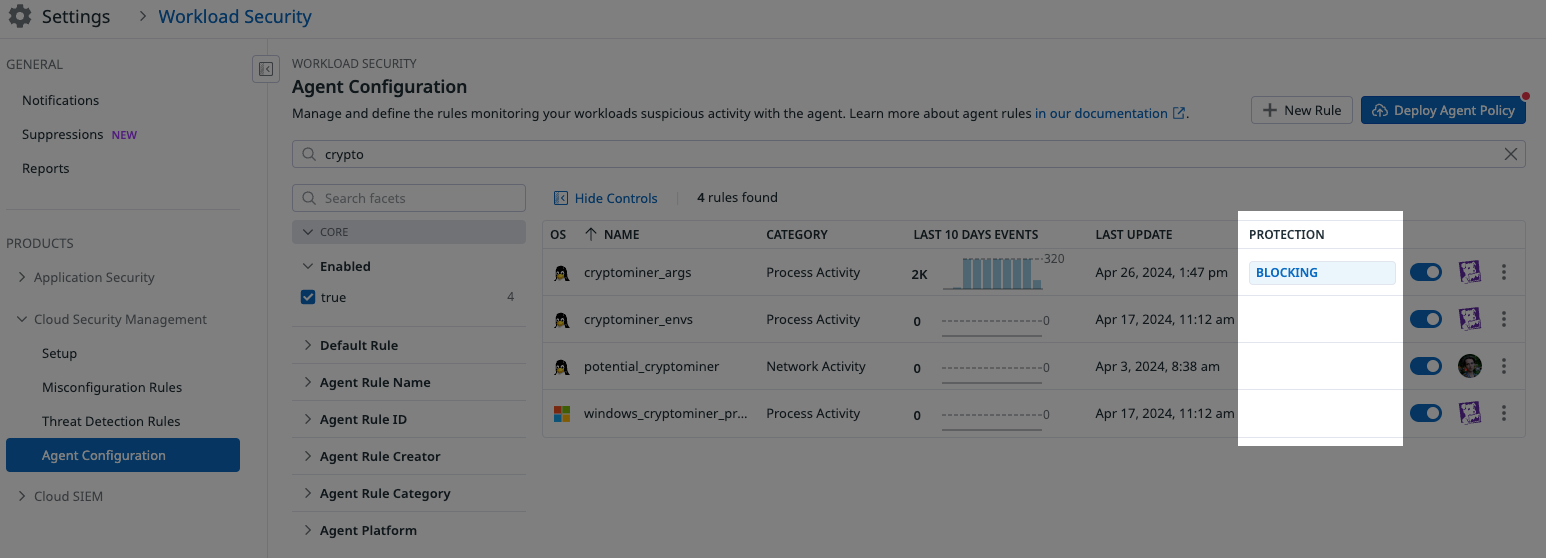
To check if Active Protection is already enabled in your organization, go to Agent Configuration. If Active Protection is enabled, a Protection column is displayed in the Agent rule list.
If Active Protection is available for a crypto mining rule, then Monitoring or Blocking is listed in the Protection column.
If there is no Monitoring or Blocking in the Protection column, then Active Protection is not available for that crypto mining rule yet.
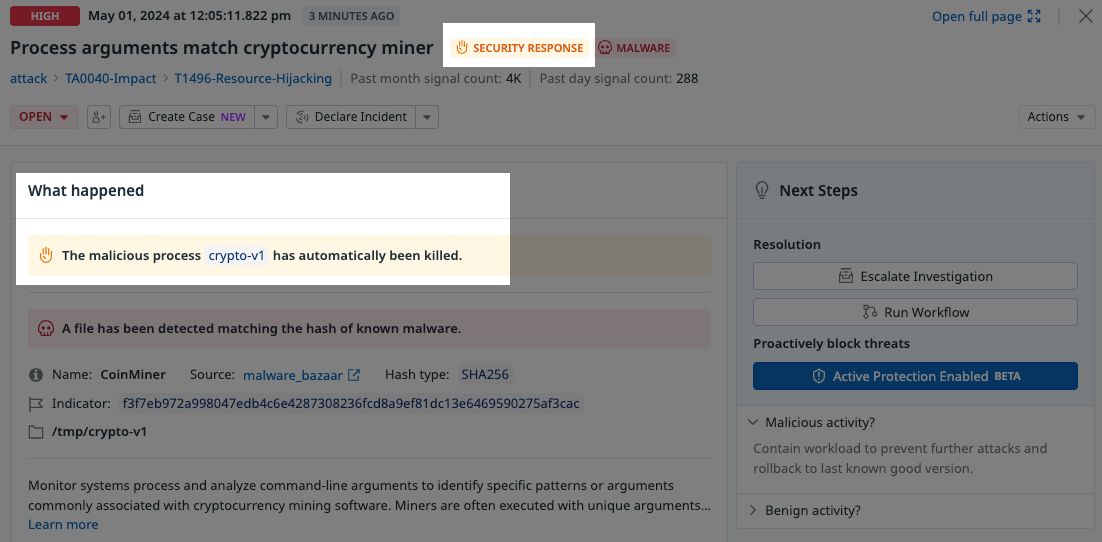
When Active Protection is enabled, and applies to a crypto mining rule that generated a signal, you can see it by doing the following:
- In Signals, open a signal.
- In the signal, view Next Steps.
- If Active Protection is enabled, in Proactively block threats, the Active Protection Enabled is displayed.
- If Active Protection is not enabled, Active Protection Enabled is not displayed.
If Active Protection is enabled and available for an Agent crypto mining rule, you can see it by looking at the rule:
- In Agent Configuration, select a crypto mining rule.
- In the crypto mining rule, if Active Protection is enabled and available, there is a Protection section.
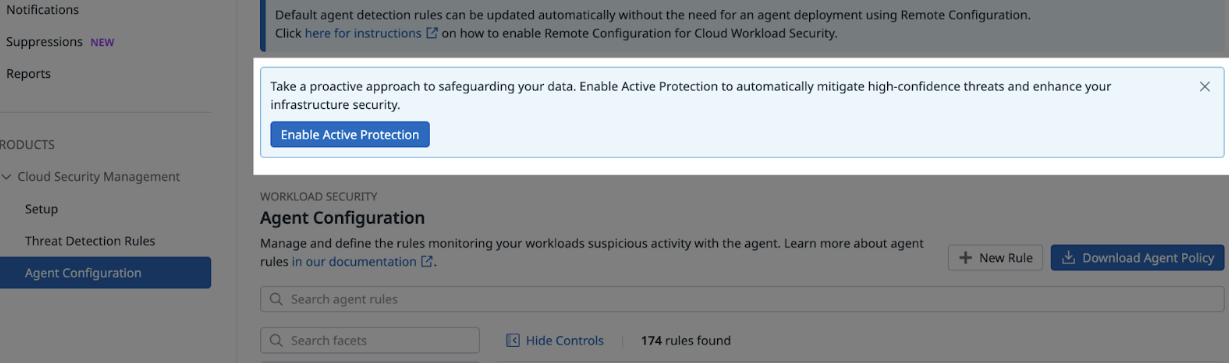
Enable Active Protection
When you enable Active Protection, you are enabling the Active Protection capability for your entire Datadog org. Active Protection is not limited to individual users.
By default, all OOTB Agent crypto mining rules are in a monitoring state. Enabling Active Protection does not immediately change the default state. Enabling Active Protection allows you to change the state of a crypto mining rule from monitoring to blocking.
Consequently, you do not need to worry that enabling Active Protection immediately changes the state of threat detection.
To enable Active Protection:
Go to CSM Agent Configuration rules.
Select Enable Active Protection.
After Active Protection is enabled, the Agent Configuration rules list contains a Protection column.
The Protection column indicates if a rule is in the Monitoring or Blocking state. When you first enable Active Protection, rules are only in a monitoring state. You must configure the blocking option manually.
Disabling Active Protection
After Active Protection is enabled, you can disable it on each Agent Configuration rule.
Block threats detected by an Agent rule
After Active Protection is enabled, you can configure the Blocking option on an Agent crypto mining rule and the Agent will terminate the corresponding crypto mining actions instantly.
To enable blocking on an Agent rule:
In Agent Configuration, open a crypto mining rule that has Monitoring in the Protection column. If there is no Monitoring or Blocking in the Protection column, then Active Protection is not available for that rule yet.
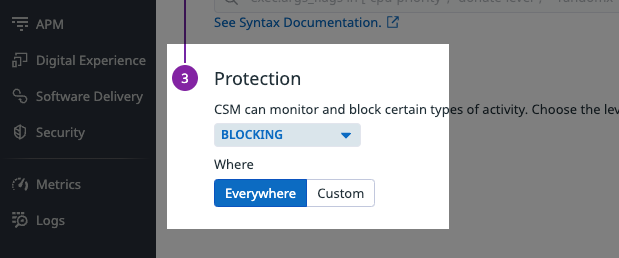
In the Agent rule, in Protection, select Blocking.
In Where, select Everywhere or Custom. For details on these options, see Scoping the Agent rule below.
Select Save Changes.
In Agent Configuration, select Deploy Agent Policy.
Scoping the Agent rule
When you create or edit an Agent crypto mining rule after Active Protection is enabled, you can select Blocking in the rule Protection setting.
When you select Blocking, you can scope where Datadog should apply the rule using the Everywhere and Custom options.
Everywhere
The rule applies to all services, hosts, and images.
Custom
In Custom, you can specify services or tags to automatically generate an expression for where to apply blocking protection.
Any service or image that is not matched by the expression is not blocked, but it is still monitored.
You can use services and tags to generate an expression. Datadog matches the rule using the services or tags you provide.
- Services: Enter one or more service names. You can use wildcards. For example, entering
a*generates the expressionprocess.envp in ["DD_SERVICE=a*"]. - Tags: Enter one or more tags for container images. If you enter multiple tags, all tags must match for the Protection to apply. There are two options:
image_tag: The image tag only. For example,stable-perl.short_image: The image name without a tag. For example,nginx.- For example, a Github Container registry image such as
ghcr.io/MY_NAMESPACE/MY_IMAGE:2.5can be referenced using:image_tag:2.5.short_image:MY_IMAGE.
Blocked attack example
After Active Protection is enabled and set to Blocking for an Agent rule, blocked threats appear in Signals.
A signal for a blocked threat contains the messages SECURITY RESPONSE and The malicious process <THREAT NAME> has automatically been killed.: