- Principales informations
- Getting Started
- Datadog
- Site Datadog
- DevSecOps
- Serverless for AWS Lambda
- Agent
- Intégrations
- Conteneurs
- Dashboards
- Monitors
- Logs
- Tracing
- Profileur
- Tags
- API
- Service Catalog
- Session Replay
- Continuous Testing
- Surveillance Synthetic
- Incident Management
- Database Monitoring
- Cloud Security Management
- Cloud SIEM
- Application Security Management
- Workflow Automation
- CI Visibility
- Test Visibility
- Intelligent Test Runner
- Code Analysis
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Intégrations
- OpenTelemetry
- Développeurs
- Authorization
- DogStatsD
- Checks custom
- Intégrations
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Recommended Monitor
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- Checks de service
- IDE Plugins
- Communauté
- Guides
- API
- Application mobile
- CoScreen
- Cloudcraft
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Alertes
- Infrastructure
- Métriques
- Watchdog
- Bits AI
- Service Catalog
- API Catalog
- Error Tracking
- Service Management
- Infrastructure
- Universal Service Monitoring
- Conteneurs
- Sans serveur
- Surveillance réseau
- Cloud Cost
- Application Performance
- APM
- Profileur en continu
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Configuration de Postgres
- Configuration de MySQL
- Configuration de SQL Server
- Setting Up Oracle
- Setting Up MongoDB
- Connecting DBM and Traces
- Données collectées
- Exploring Database Hosts
- Explorer les métriques de requête
- Explorer des échantillons de requêtes
- Dépannage
- Guides
- Data Streams Monitoring
- Data Jobs Monitoring
- Digital Experience
- RUM et Session Replay
- Product Analytics
- Surveillance Synthetic
- Continuous Testing
- Software Delivery
- CI Visibility
- CD Visibility
- Test Visibility
- Exécuteur de tests intelligent
- Code Analysis
- Quality Gates
- DORA Metrics
- Securité
- Security Overview
- Cloud SIEM
- Cloud Security Management
- Application Security Management
- AI Observability
- Log Management
- Pipelines d'observabilité
- Log Management
- Administration
Investigate Security Signals
Cette page n'est pas encore disponible en français, sa traduction est en cours.
Si vous avez des questions ou des retours sur notre projet de traduction actuel, n'hésitez pas à nous contacter.
Si vous avez des questions ou des retours sur notre projet de traduction actuel, n'hésitez pas à nous contacter.
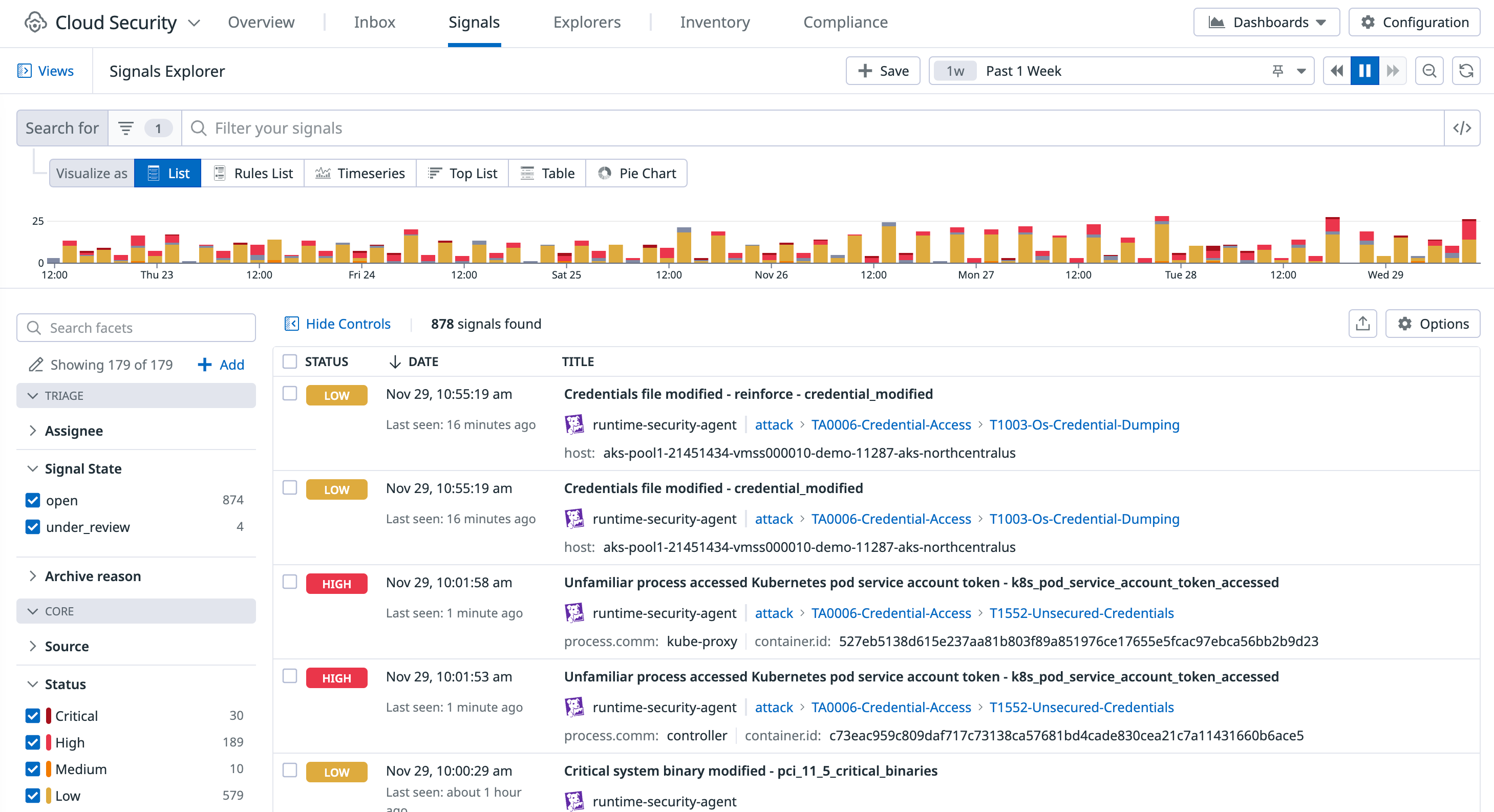
Cloud Security Management Threats (CSM Threats) security signals are created when Datadog detects a threat based on a security rule. View, search, filter, and investigate security signals in the Signals Explorer, or configure Notification Rules to send signals to third-party tools.
To modify security signals, you must have the security_monitoring_signals_write permission. See Role Based Access Control for more information about Datadog’s default roles and granular role-based access control permissions available for Cloud Security Management.
Filter security signals
To filter the security signals in the Signals Explorer, use the search query @workflow.triage.state:<status>, where <status> is the state you want to filter on (open, under_review, or archived). You can also use the Signal State facet on the facet panel.
Triage a signal
You can triage a signal by assigning it to a user for further investigation. The assigned user can then track their review by updating the signal’s status.
- On the Signals Explorer, select a security signal.
- On the signal side panel, click the user profile icon and select a user.
- To update the status of the security signal, click the triage status dropdown menu and select a status. The default status is Open.
- Open: The signal has not yet been resolved.
- Under Review: The signal is actively being investigated. From the Under Review state, you can move the signal to Archived or Open as needed.
- Archived: The detection that caused the signal has been resolved. From the Archived state, you can move the signal back to Open if it’s within 30 days of when the signal was originally detected.
Create a case
Case Management is not supported for your selected Datadog site ().
Use Case Management to track, triage, and investigate security signals.
- On the Signals Explorer, select a security signal.
- On the signal side panel, click the Escalate Investigation dropdown menu and select Create a case. Alternatively, select Add to an existing case to add the signal to an existing case.
- Enter a title and optional description.
- Click Create Case.
Declare an incident
Use Incident Management to create an incident for a security signal.
- On the Signals Explorer, select a security signal.
- On the signal side panel under Next Steps, click the Show all actions dropdown menu and select Declare incident.
- Alternatively, select Add to incident to add the signal to an existing incident.
- On the incident creation modal, configure the incident by specifying details such as the severity level and incident commander.
- Click Declare Incident.
Run a workflow
Use Workflow Automation to manually trigger a workflow for a security signal. See Trigger a Workflow from a Security Signal for more information.
- On the Signals Explorer, select a security signal.
- On the signal side panel, click the Workflows tab.
- Click Run Workflow.
- On the workflow modal, select the workflow you want to run. The workflow must have a security trigger to appear in the list. Depending on the workflow, you may be required to enter additional input parameters.
- Click Run.
Further Reading
Documentation, liens et articles supplémentaires utiles: