- Essentials
- Getting Started
- Datadog
- Datadog Site
- DevSecOps
- Serverless for AWS Lambda
- Agent
- Integrations
- Containers
- Dashboards
- Monitors
- Logs
- APM Tracing
- Profiler
- Tags
- API
- Service Catalog
- Session Replay
- Continuous Testing
- Synthetic Monitoring
- Incident Management
- Database Monitoring
- Cloud Security Management
- Cloud SIEM
- Application Security Management
- Workflow Automation
- CI Visibility
- Test Visibility
- Test Impact Analysis
- Code Analysis
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- OpenTelemetry
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Recommended Monitor
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- Service Checks
- IDE Plugins
- Community
- Guides
- API
- Datadog Mobile App
- CoScreen
- Cloudcraft
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Sheets
- Monitors and Alerting
- Infrastructure
- Metrics
- Watchdog
- Bits AI
- Service Catalog
- API Catalog
- Error Tracking
- Service Management
- Infrastructure
- Application Performance
- APM
- Continuous Profiler
- Database Monitoring
- Data Streams Monitoring
- Data Jobs Monitoring
- Digital Experience
- Real User Monitoring
- Product Analytics
- Synthetic Testing and Monitoring
- Continuous Testing
- Software Delivery
- CI Visibility
- CD Visibility
- Test Optimization
- Code Analysis
- Quality Gates
- DORA Metrics
- Security
- Security Overview
- Cloud SIEM
- Cloud Security Management
- Application Security Management
- AI Observability
- Log Management
- Observability Pipelines
- Log Management
- Administration
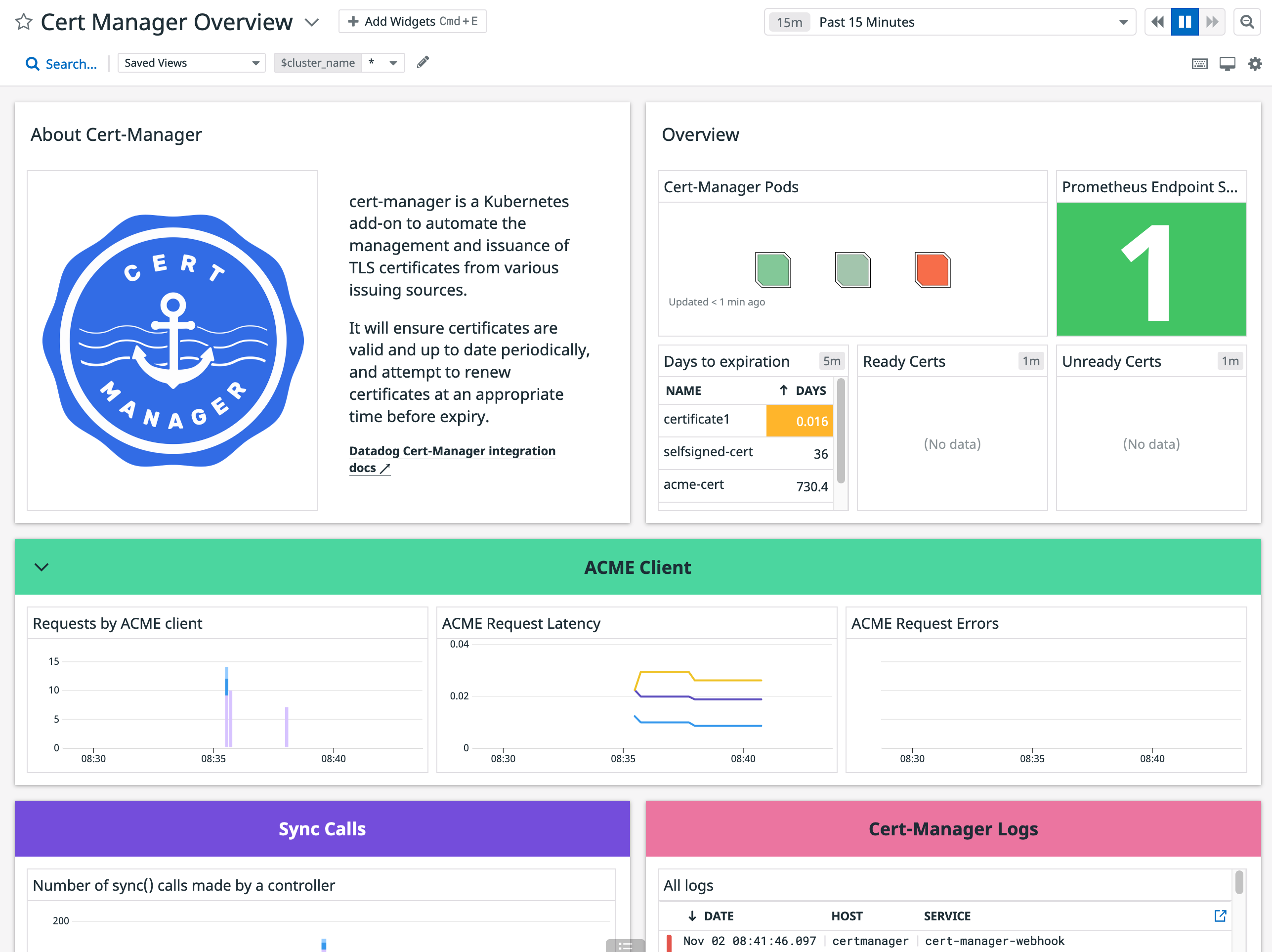
cert-manager
Supported OS
Integration version5.1.0
Overview
This check collects metrics from cert-manager.
Setup
Follow the instructions below to install and configure this check for an Agent running on a host. For containerized environments, see the Autodiscovery Integration Templates for guidance on applying these instructions.
Installation
The cert_manager check is included in the Datadog Agent package. No additional installation is needed on your server.
Configuration
Edit the
cert_manager.d/conf.yamlfile in theconf.d/folder at the root of your Agent’s configuration directory to start collecting your cert_manager performance data. See the sample cert_manager.d/conf.yaml for all available configuration options.
Validation
Run the Agent’s status subcommand and look for cert_manager under the Checks section.
Data Collected
Metrics
| cert_manager.certificate.expiration_timestamp (gauge) | The date after which the certificate expires. Expressed as a Unix Epoch Time Shown as second |
| cert_manager.certificate.ready_status (gauge) | The ready status of the certificate |
| cert_manager.clock_time (gauge) | The clock time given in seconds (from 1970/01/01 UTC) Shown as second |
| cert_manager.controller.sync_call.count (count) | The number of sync() calls made by a controller |
| cert_manager.http_acme_client.request.count (count) | The number of requests made by the ACME client |
| cert_manager.http_acme_client.request.duration.count (count) | The count of the HTTP request latencies in seconds for the ACME client |
| cert_manager.http_acme_client.request.duration.quantile (gauge) | The quantiles of the HTTP request latencies in seconds for the ACME client |
| cert_manager.http_acme_client.request.duration.sum (count) | The sum of the HTTP request latencies in seconds for the ACME client |
Events
The cert_manager integration does not include any events.
Service Checks
cert_manager.openmetrics.health
Returns CRITICAL if the agent fails to connect to the OpenMetrics endpoint, otherwise OK.
Statuses: ok, critical
Troubleshooting
Duplicate name tags
Each certificate name is exposed within the name label in the Prometheus payload and is converted to a tag by the Datadog Agent. If your hosts also use the name tag (for instance, automatically collected by the AWS integration), metrics coming from this integration will present both values. To avoid duplicate name tags, you can use the rename_labelsconfiguration parameter to map the Prometheus label name to the Datadog tag cert_name. This ensures you have a single value within the tag cert_name to identify your certificates :
init_config:
instances:
- openmetrics_endpoint: <OPENMETRICS_ENDPOINT>
rename_labels:
name: cert_name
Need further help? Contact Datadog support.
