- Essentials
- Getting Started
- Datadog
- Datadog Site
- DevSecOps
- Serverless for AWS Lambda
- Agent
- Integrations
- Containers
- Dashboards
- Monitors
- Logs
- APM Tracing
- Profiler
- Tags
- API
- Service Catalog
- Session Replay
- Continuous Testing
- Synthetic Monitoring
- Incident Management
- Database Monitoring
- Cloud Security Management
- Cloud SIEM
- Application Security Management
- Workflow Automation
- CI Visibility
- Test Visibility
- Test Impact Analysis
- Code Analysis
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- OpenTelemetry
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Recommended Monitor
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- Service Checks
- IDE Plugins
- Community
- Guides
- API
- Datadog Mobile App
- CoScreen
- Cloudcraft
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Sheets
- Monitors and Alerting
- Infrastructure
- Metrics
- Watchdog
- Bits AI
- Service Catalog
- API Catalog
- Error Tracking
- Service Management
- Infrastructure
- Application Performance
- APM
- Continuous Profiler
- Database Monitoring
- Data Streams Monitoring
- Data Jobs Monitoring
- Digital Experience
- Real User Monitoring
- Product Analytics
- Synthetic Testing and Monitoring
- Continuous Testing
- Software Delivery
- CI Visibility
- CD Visibility
- Test Optimization
- Code Analysis
- Quality Gates
- DORA Metrics
- Security
- Security Overview
- Cloud SIEM
- Cloud Security Management
- Application Security Management
- AI Observability
- Log Management
- Observability Pipelines
- Log Management
- Administration
Microsoft 365 Security and Audit Logs
Overview
Integrate with Microsoft 365 to:
- View and parse your audit logs using Datadog’s logging product
- Set monitors on events from your Microsoft 365 platform
- Leverage the Datadog suite of security tools to set security rules
Setup
Installation
Use the Datadog Microsoft 365 tile to install the integration.
Click Install a New Tenant. This directs you to login to your Microsoft 365 account for authorization. You must login with an admin account.
Optionally add comma separated custom tags that get attached to every log for this newly setup tenant, for example, environment:prod,team:us. These tags can be used to filter/analyze logs.
Note: Your organization must have audit logging enabled to use Datadog audit logging.
Data Collected
Logs
You can collect audit logs for all services mentioned in Office 365 Management API schemas, such as:
- Microsoft Teams
- Power BI
- Azure Active Directory
- Dynamics 365
- Exchange
- SharePoint
The Microsoft 365 integration produces one log event per audit log. Collected logs are tagged with the source microsoft-365. Click below for a list of common log sources with summaries and links to preset log queries in Datadog.
Click to view common log sources
AirInvestigation- Related to Advanced eDiscovery and Advanced Threat Protection (ATP) investigations within Microsoft 365. These logs contain information about security incidents, investigations, and actions taken to mitigate threats, such as alerts, remediation steps, and forensic data.
Audit.AzureActiveDirectory- Represents logs generated by Azure Active Directory (Azure AD), Microsoft’s cloud-based identity and access management service. Azure AD logs provide insights into user sign-in activities, directory and group management, application access, and security-related events. It enables organizations to manage user access and detect potential security risks.
Audit.Exchange- Pertains to logs generated by Microsoft Exchange Server. Exchange logs contain information about email delivery, mailbox access, client connections, and administrative actions within the Exchange environment. It helps organizations monitor and troubleshoot email-related issues.
Audit.General- Contains information about various activities and events occurring within your Microsoft 365 environment, such as user and admin activities, system events, security incidents, and other actions that are not directly associated with specific services like Exchange or SharePoint.
Audit.MicrosoftForms- Represents logs generated by Microsoft Forms, a tool for creating surveys, quizzes, and forms. Forms logs include information about form creation, access, responses, and user activities. It assists organizations in tracking and securing their forms data.
Audit.MicrosoftStream- Refers to logs generated by Microsoft Stream, a video-sharing platform within the Microsoft ecosystem. Stream logs contain information about video uploads, access, sharing, and user activities. It helps organizations track and secure their video content.
Audit.MicrosoftTeams- Encompasses logs produced by Microsoft Teams, a collaboration and communication platform. Teams logs include information about user activities, team and channel management, file sharing, and meeting events. It assists organizations in monitoring user interactions and ensuring secure collaboration.
Audit.OneDrive- Refers to logs generated by OneDrive, Microsoft’s cloud-based file storage and synchronization service. OneDrive logs include information about file access, sharing, modifications, and user activities. It helps organizations monitor and secure their cloud-based data.
Audit.PowerBI- Refers to logs produced by Power BI, Microsoft’s business analytics and data visualization tool. Power BI logs contain information about data access, report generation, dashboard activities, and user interactions. It helps organizations monitor and secure their business intelligence data.
Audit.Project- Refers to the audit logs for Microsoft Project, a project management tool within the Microsoft 365 suite. These logs capture events related to user activities, administrative actions, and system events within Microsoft Project, such as project creation, task updates, resource allocation, and permission changes.
Audit.SharePoint- Refers to logs produced by Microsoft SharePoint. SharePoint logs record user access, document modifications, site administration, and security-related events. It enables organizations to maintain data integrity and secure their SharePoint sites and content.
Audit.SkypeForBusiness- Refers to the audit logs for Skype for Business activities. These logs capture events related to user and administrative actions within the Skype for Business service, such as call detail records, conference detail records, messaging activities, and admin actions like user management and policy updates.
Audit.Yammer- Represents logs produced by Yammer, a social networking platform for enterprises. Yammer logs include information about user activities, group and community management, and content sharing. It helps organizations monitor and secure their internal social networks.
ComplianceManager- Related to the Microsoft Compliance Manager tool, which helps organizations assess, manage, and track their compliance activities in Microsoft 365. These logs contain information about compliance assessments, tasks, improvement actions, and progress towards meeting regulatory requirements.
DLP.All- Captures events related to DLP policies, detections, and actions across all Microsoft 365 services, including Exchange, SharePoint, OneDrive, Microsoft Teams, and others. These logs provide insights into policy violations, sensitive information detections, and the actions taken to protect the data, such as blocking content, notifying users or administrators, and more.
Dynamics365- Collect events from any of your Microsoft Dynamics 365 services and applications.
MicrosoftFlow- Associated with the Microsoft Power Automate service (formerly known as Microsoft Flow), a cloud-based platform that allows users to create and manage automated workflows between various applications and services. These logs capture events related to workflow runs, errors, and administrative actions, such as creating, updating, or deleting flows.
Mip- Pertains to logs generated by Microsoft Information Protection (MIP), a suite of tools and services for classifying, labeling, and protecting sensitive data. MIP logs provide insights into data classification, access, and protection events. It enables organizations to manage and secure their sensitive information.
MyAnalytics- Related to the Microsoft MyAnalytics service, which provides insights into an individual’s work habits and productivity trends within the Microsoft 365 suite. These logs contain information about users’ activities, such as time spent on meetings, emails, collaboration, and focus time.
PowerApps- Refers to logs generated by Power Apps, Microsoft’s low-code application development platform. Power Apps logs contain information about app creation, access, usage, and user activities.
Quarantine- Represents logs generated by email quarantine systems used to isolate and review potentially malicious or unwanted emails. Quarantine logs include information about quarantined emails, sender and recipient details, and actions taken. It assists organizations in managing email security and preventing threats.
Rdl- Related to SQL Server Reporting Services (SSRS), a server-based reporting platform that allows users to create, publish, and manage reports in various formats. The Rdl log source captures events related to report execution, access, and administrative actions, such as generating, updating, or deleting reports.
SecurityComplianceCenter- Pertains to logs generated by Microsoft’s Security & Compliance Center, a centralized platform for managing security and compliance features across Microsoft 365 services. These logs provide insights into security incidents, policy violations, and compliance management activities. It helps organizations maintain a secure and compliant IT environment.
SecurityMonitoringEntityReducer- Associated with security event logs and alert aggregation activities in Microsoft 365. These logs provide insights into security events, anomalies, and potential threats detected across the Microsoft 365 environment.
ThreatIntelligence- Encompasses logs generated by threat intelligence systems or tools that collect, analyze, and share information about emerging security threats. Threat intelligence logs provide insights into potential threats, vulnerabilities, and indicators of compromise. It helps organizations proactively defend against cyberattacks.
See Office 365 Management API schemas for the full list of potential log sources.
Security
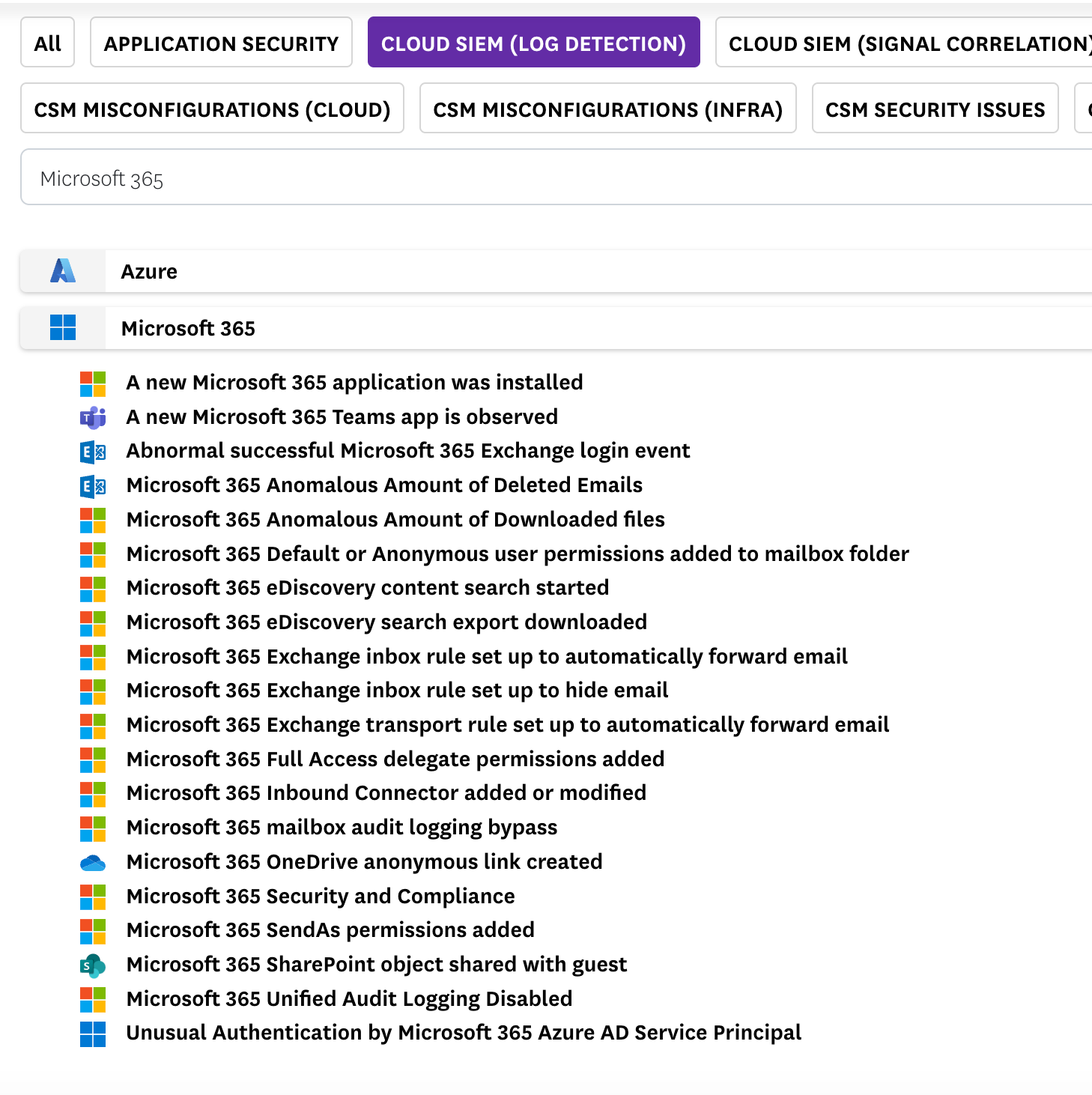
You can use Datadog’s Cloud SIEM to detect real-time threats in your environment with Microsoft 365 audit logs. See the full list of out-of-the-box Microsoft 365 detection rules or create a custom detection rule.
Metrics
The Microsoft 365 integration does not collect any metrics.
Service checks
The Microsoft 365 integration does not collect any service checks.
Troubleshooting
Datadog’s log intake only supports backdating log events up to 18 hours in the past. Log events with an earlier timestamp are discarded.
Datadog does not support GCC government, GCC High government, or DoD tenants, because they require different Microsoft endpoints.
Need help? Contact Datadog support.
Further reading
Additional helpful documentation, links, and articles: