- Essentials
- Getting Started
- Datadog
- Datadog Site
- DevSecOps
- Serverless for AWS Lambda
- Agent
- Integrations
- Containers
- Dashboards
- Monitors
- Logs
- APM Tracing
- Profiler
- Tags
- API
- Service Catalog
- Session Replay
- Continuous Testing
- Synthetic Monitoring
- Incident Management
- Database Monitoring
- Cloud Security Management
- Cloud SIEM
- Application Security Management
- Workflow Automation
- CI Visibility
- Test Visibility
- Test Impact Analysis
- Code Analysis
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- OpenTelemetry
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Recommended Monitor
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- Service Checks
- IDE Plugins
- Community
- Guides
- API
- Datadog Mobile App
- CoScreen
- Cloudcraft
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Sheets
- Monitors and Alerting
- Infrastructure
- Metrics
- Watchdog
- Bits AI
- Service Catalog
- API Catalog
- Error Tracking
- Service Management
- Infrastructure
- Application Performance
- APM
- Continuous Profiler
- Database Monitoring
- Data Streams Monitoring
- Data Jobs Monitoring
- Digital Experience
- Real User Monitoring
- Product Analytics
- Synthetic Testing and Monitoring
- Continuous Testing
- Software Delivery
- CI Visibility
- CD Visibility
- Test Optimization
- Code Analysis
- Quality Gates
- DORA Metrics
- Security
- Security Overview
- Cloud SIEM
- Cloud Security Management
- Application Security Management
- AI Observability
- Log Management
- Observability Pipelines
- Log Management
- Administration
Palo Alto Panorama
Supported OS
Integration version1.0.0
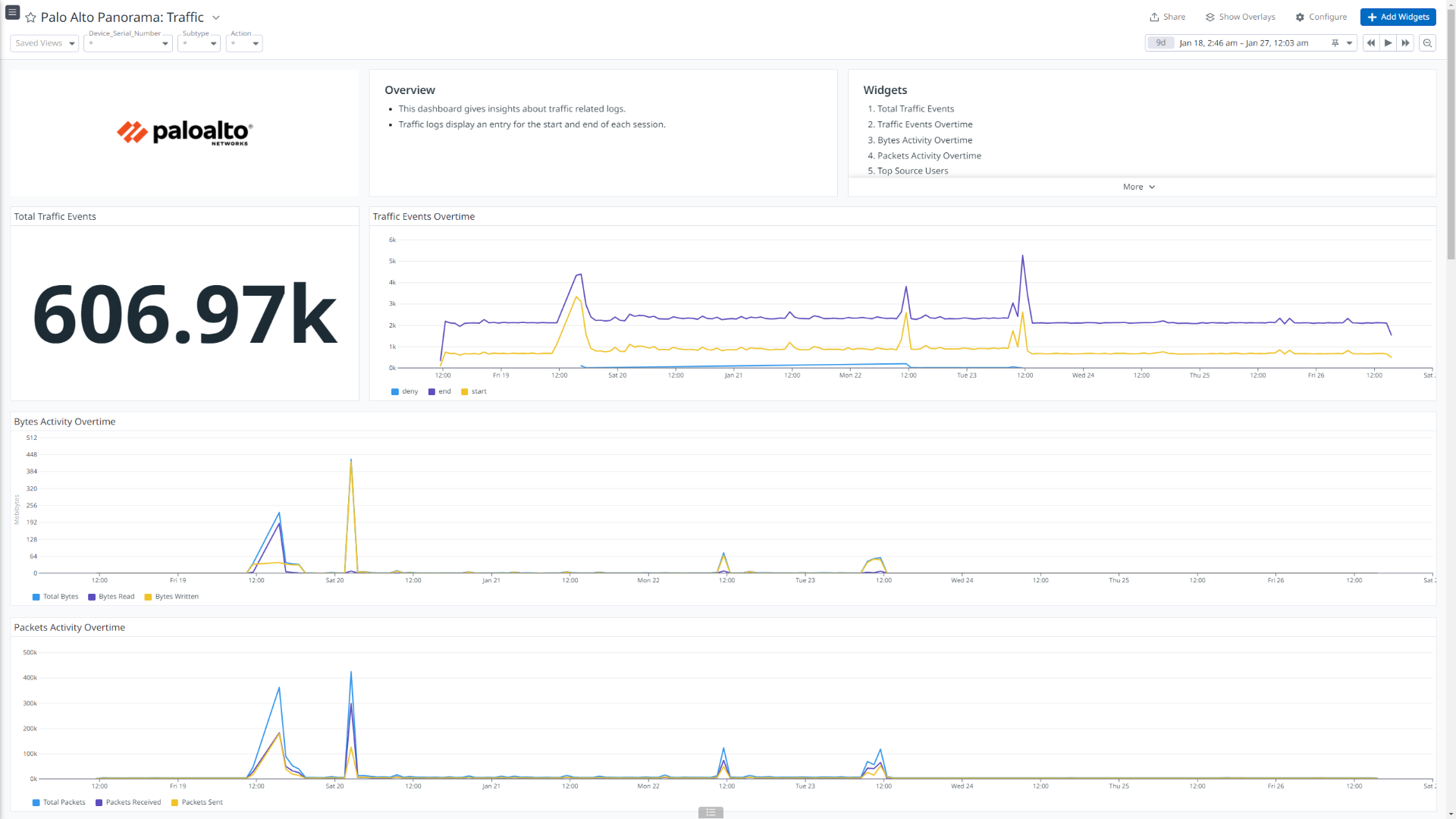

Palo Alto Panorama: Traffic
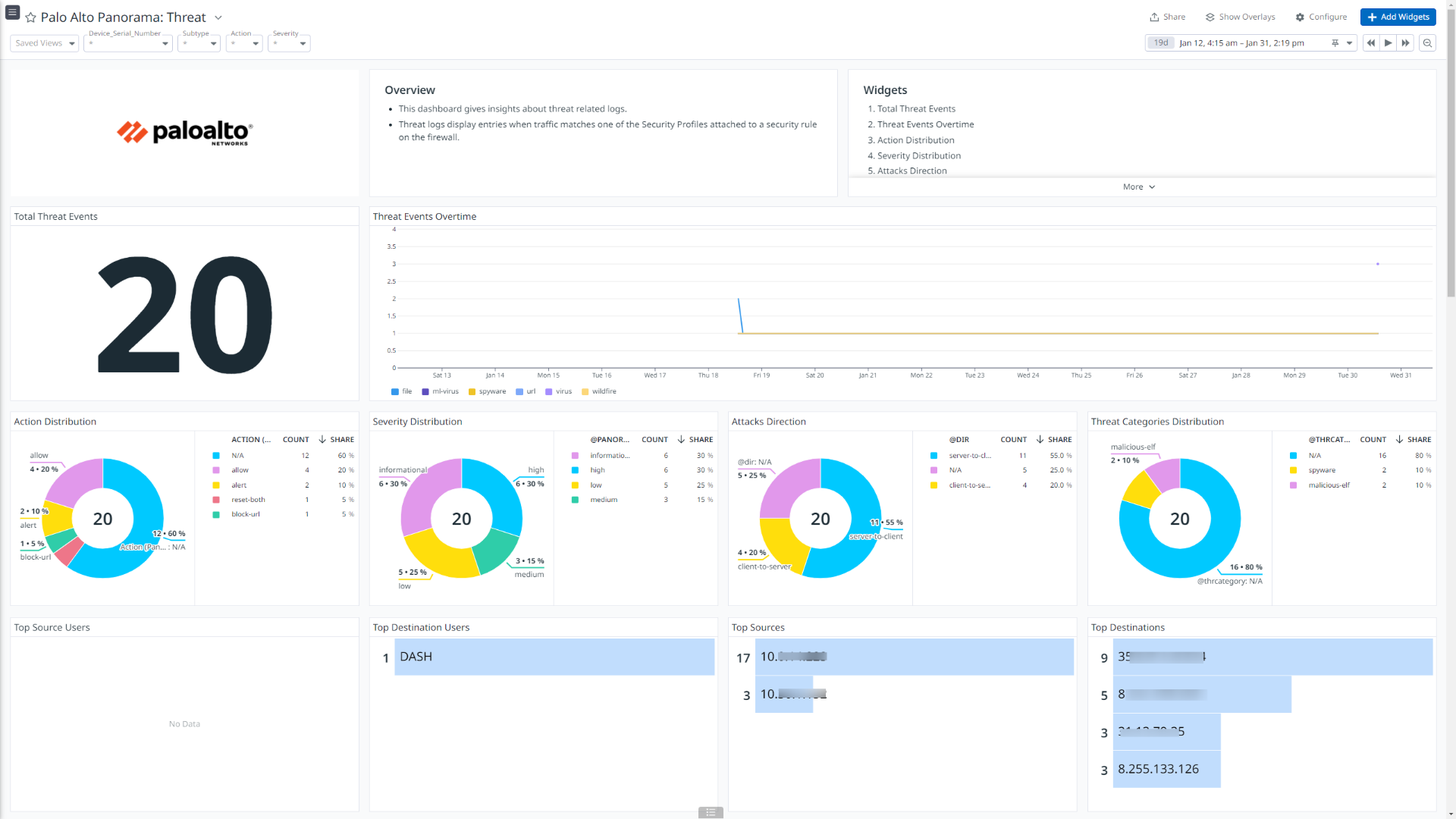
Palo Alto Panorama: Threat
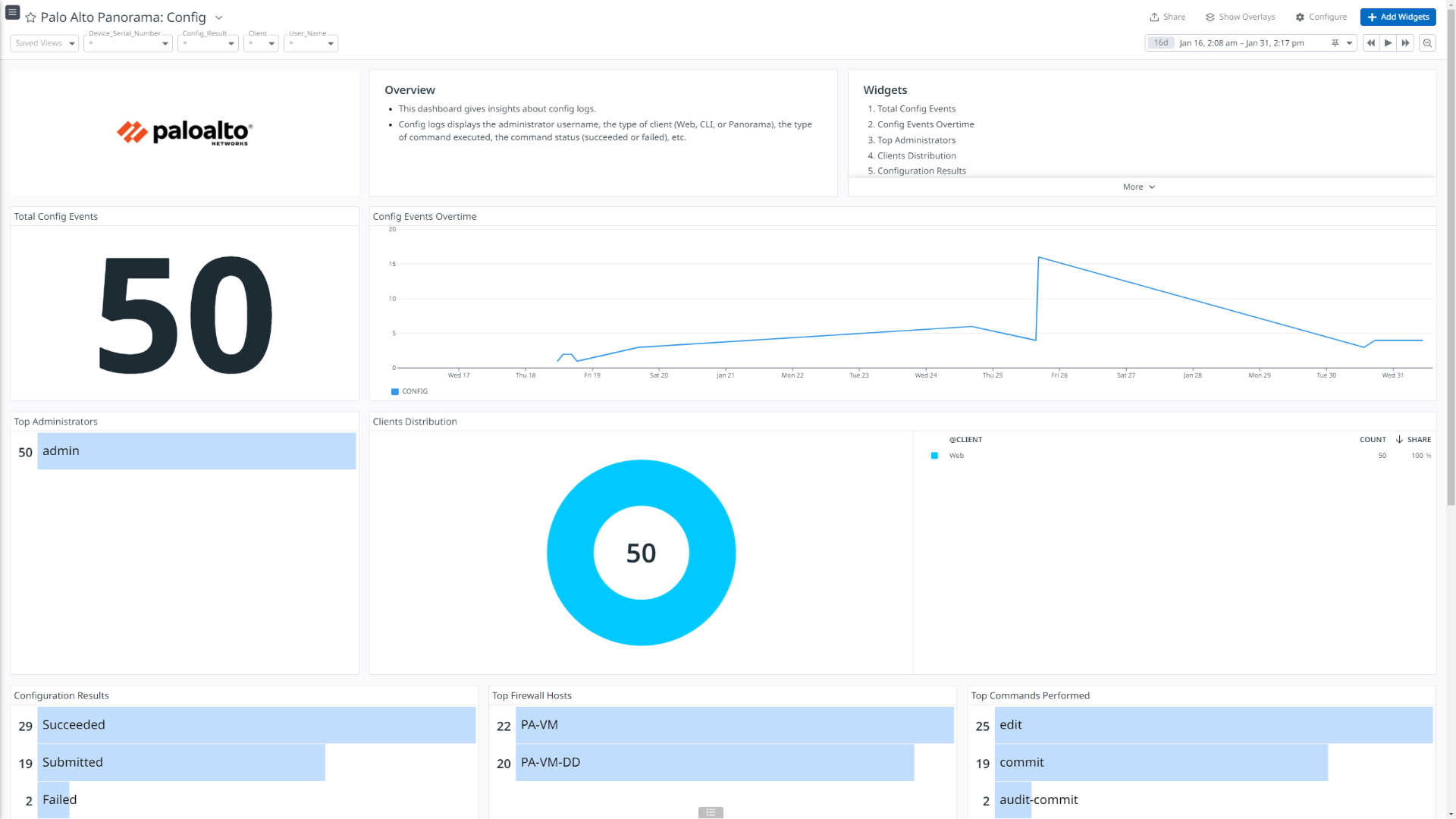
Palo Alto Panorama: Config
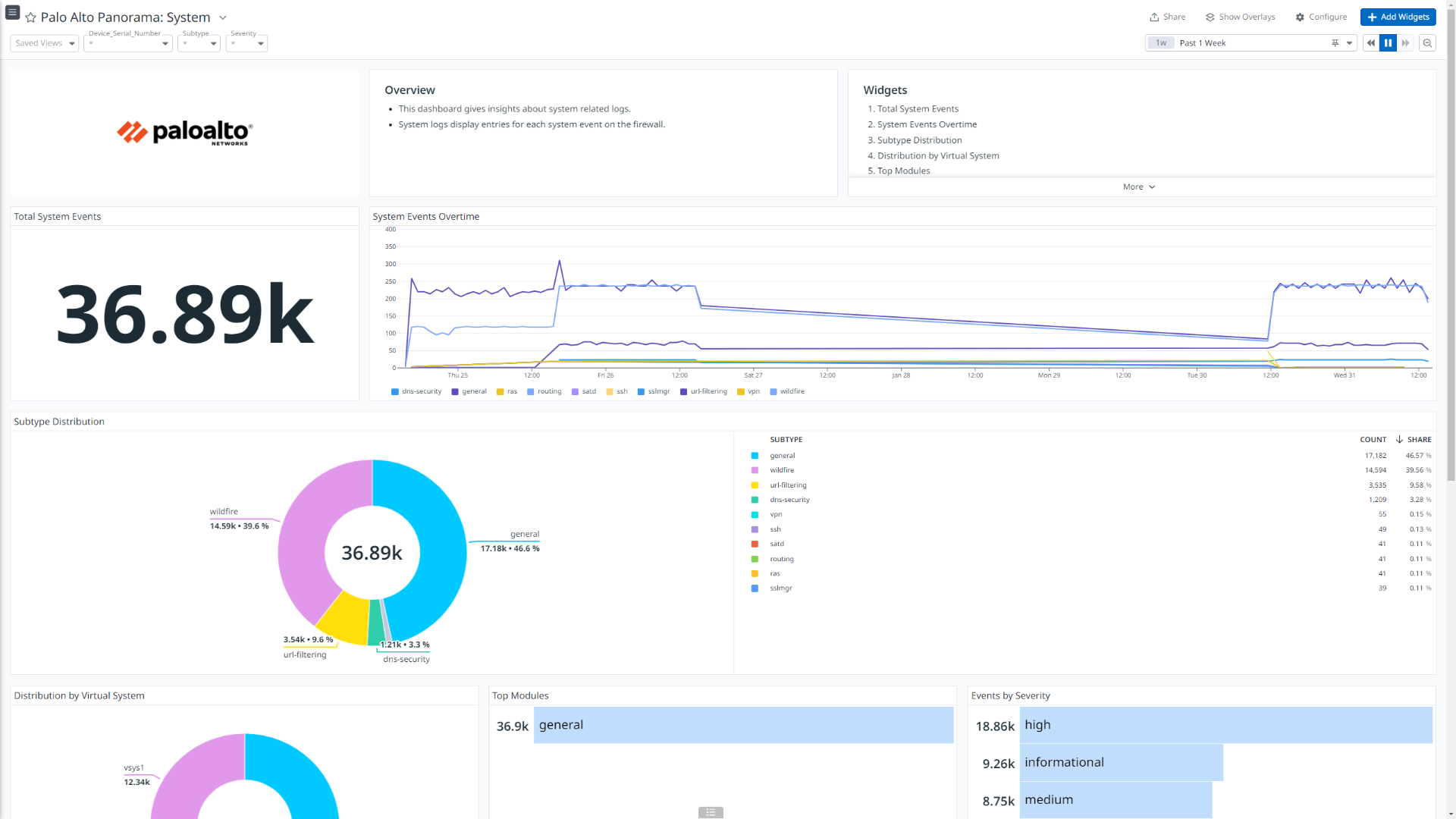
Palo Alto Panorama: System
Palo Alto Panorama: Decryption
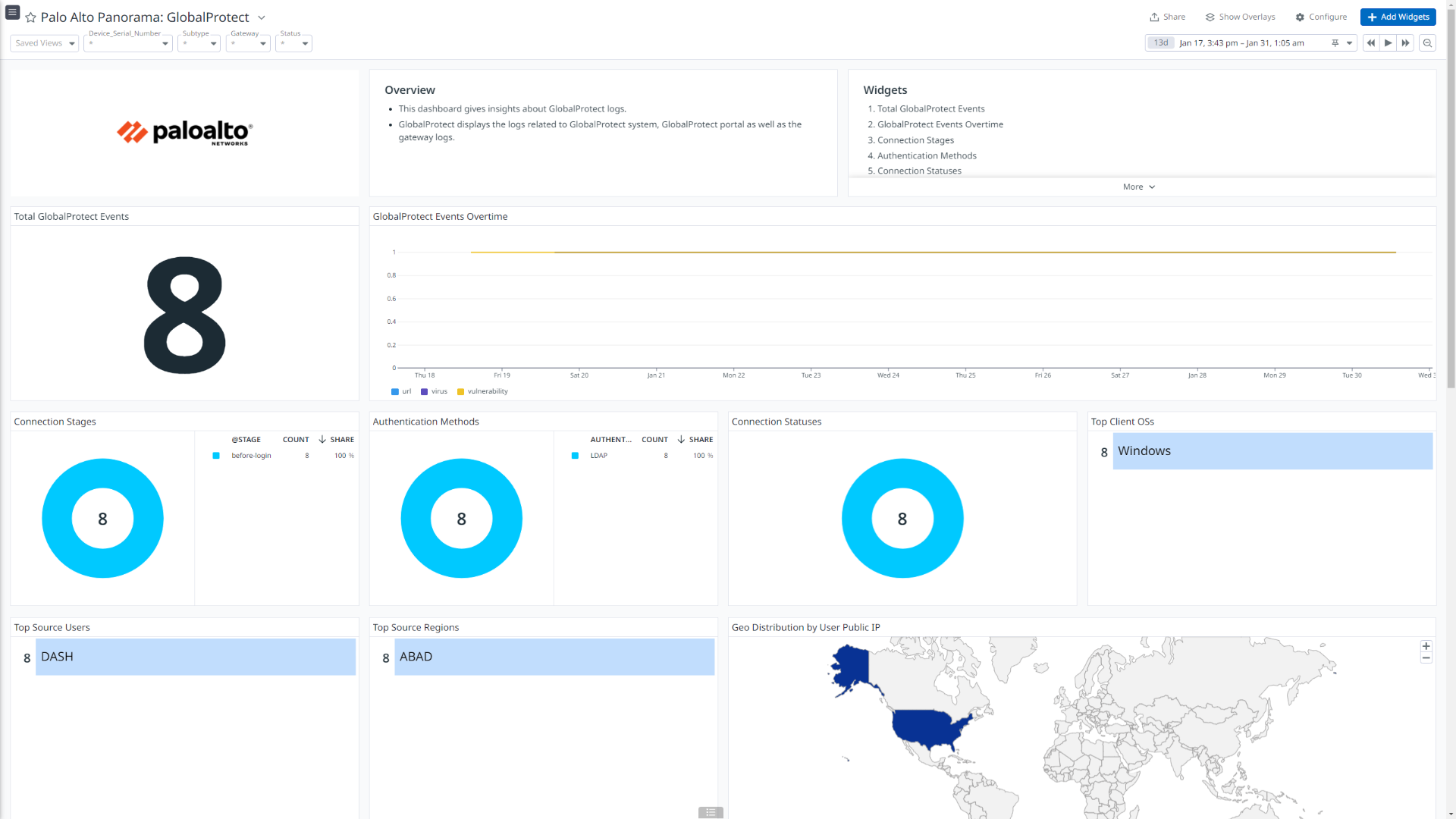
Palo Alto Panorama: Global Protect
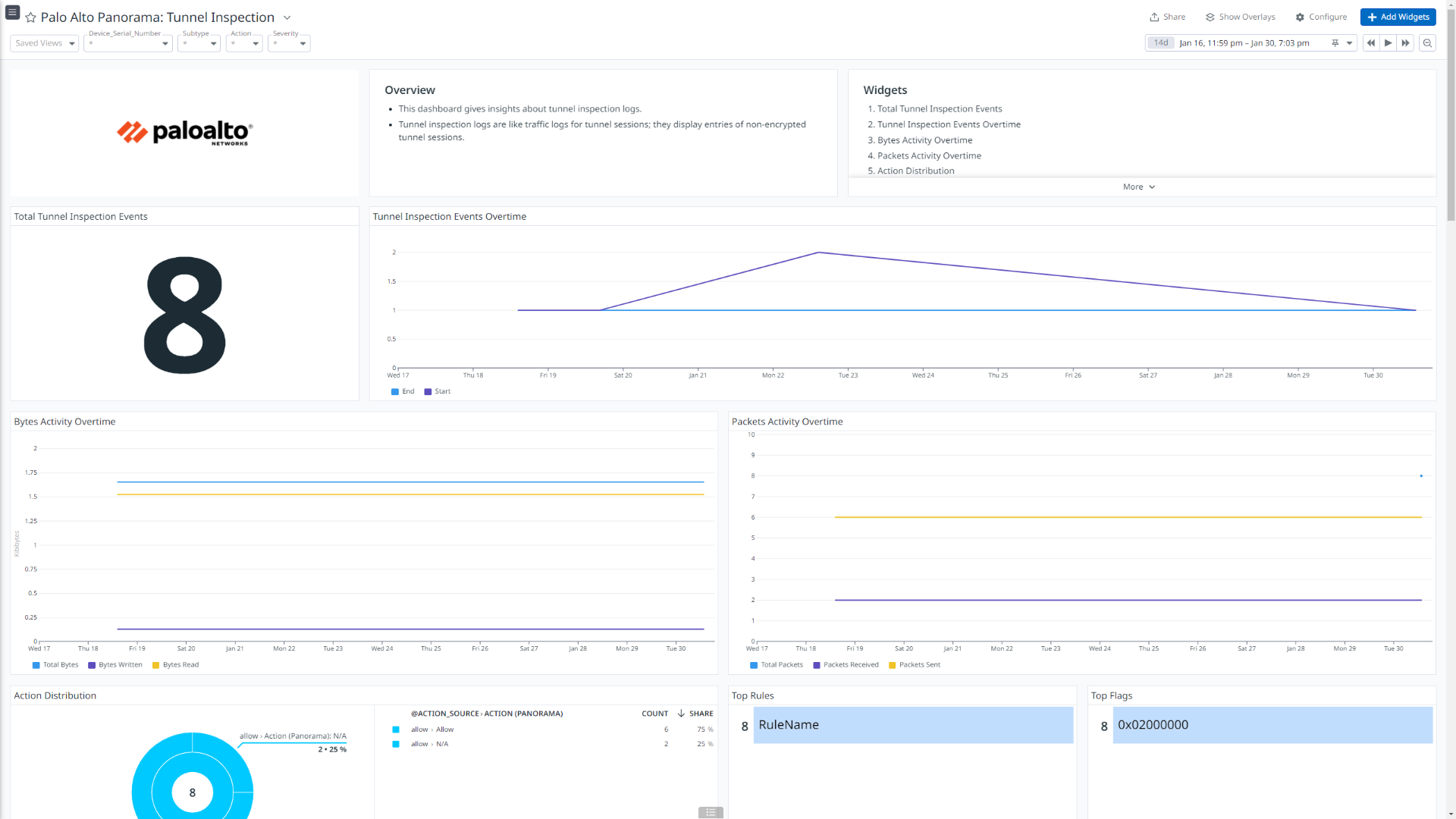
Palo Alto Panorama: Tunnel Inspection
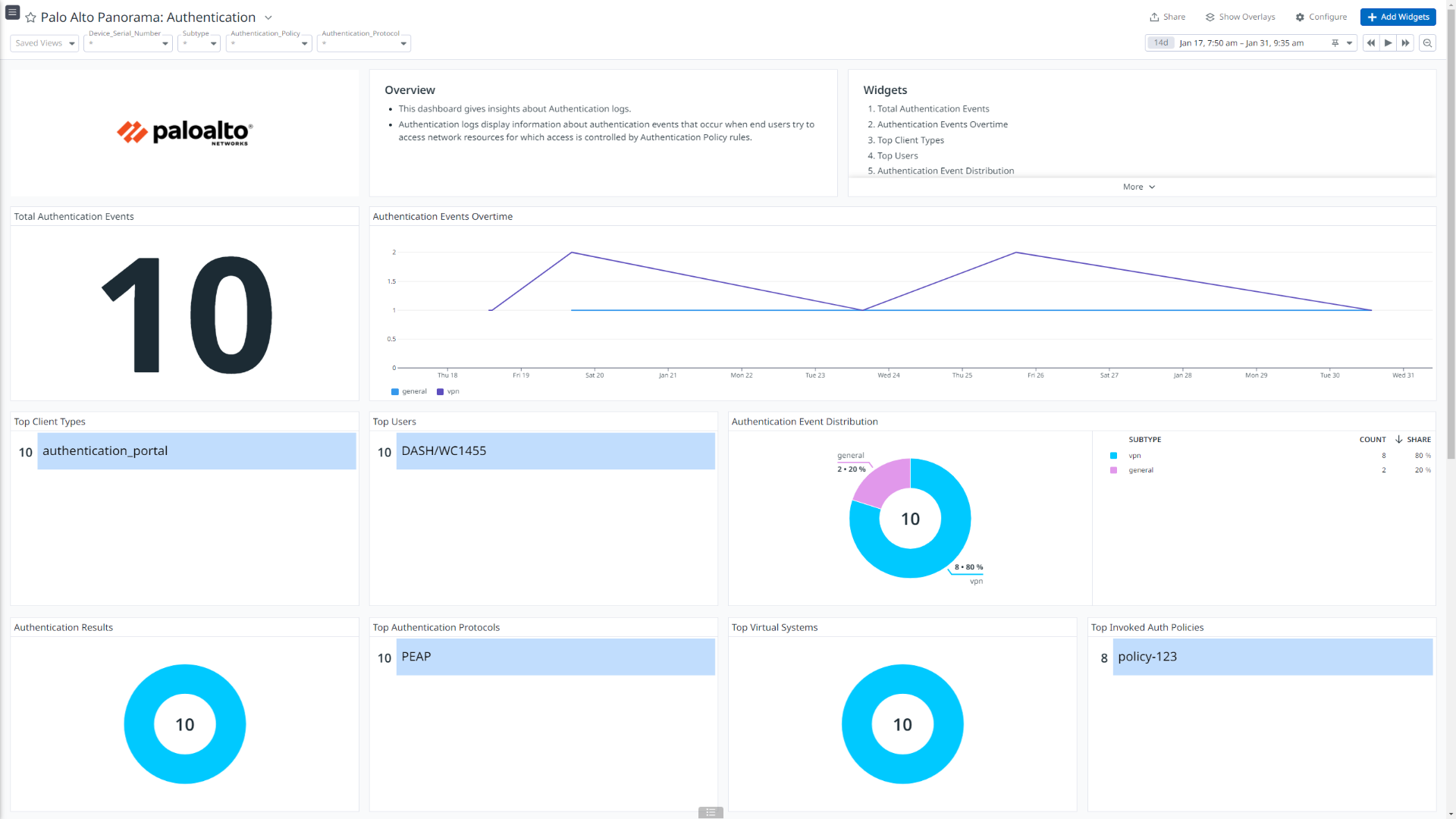
Palo Alto Panorama: Authentication
Overview
Palo Alto Panorama is a security management software application developed by Palo Alto Networks. It’s designed to provide centralized management, logging, and reporting for Palo Alto Network firewalls.
This integration ingests Traffic, Threat, Authentication, HIP Match, User ID, Tunnel Inspection, Config, System, Correleated Events, URL Filtering, Data Filtering, GlobalProtect, and Decryption log types with the integration log pipeline to enrich the logs and normalizes data to Datadog standard attributes.
This integration offers dashboard visualizations with detailed insights into inbound and outbound traffic flows, threats details, insights into user authentications, events generated by globalprotect, mapping between users and IP address, and more.
Setup
Installation
To install the Palo Alto Panorama integration, run the following Agent installation command and the steps below. For more information, see the Integration Management documentation.
Note: This step is not necessary for Agent version >= 7.52.0.
Linux command:
sudo -u dd-agent -- datadog-agent integration install datadog-palo_alto_panorama==1.0.0
Configuration
Log collection
Palo Alto Panorama:
Collecting logs is disabled by default in the Datadog Agent. Enable it in the
datadog.yamlfile:logs_enabled: trueAdd this configuration block to your
palo_alto_panorama.d/conf.yamlfile to start collecting your Palo Alto Panorama logs.See the sample palo_alto_panorama.d/conf.yaml for available configuration options.
logs: - type: tcp/udp port: <PORT> service: palo-alto-panorama source: palo-alto-panoramaConfigure Panorama to send data to Datadog:
- Login into the Panorama System
- Follow the Syslog log forwarding configuration steps.
- For Step 1.4, use
TCP/UDPforTransporttype andBSDformat for thesyslog messages. - For Step 1.5, use the provided custom logs format below:
- Traffic
serial=$serial|type=$type|subtype=$subtype|time_generated=$cef-formatted-time_generated|src=$src|dst=$dst|natsrc=$natsrc|natdst=$natdst|rule=$rule|suser=$srcuser|duser=$dstuser|app=$app|vsys=$vsys|from=$from|to=$to|inboundif=$inbound_if|outboundif=$outbound_if|logset=$logset|sessionid=$sessionid|repeatcnt=$repeatcnt|sport=$sport|dport=$dport|natsport=$natsport|natdport=$natdport|flags=$flags|proto=$proto|act=$action|bytes=$bytes|bytes_sent=$bytes_sent|bytes_received=$bytes_received|pkt=$packets|start=$start|elapsed=$elapsed|cat=$category|seq=$seqno|actflag=$actionflags|sloc=$srcloc|dloc=$dstloc|pktsent=$pkts_sent|pktrcvd=$pkts_received|sessionendreason=$session_end_reason|vsysname=$vsys_name|dvc=$device_name|actsrc=$action_source|suuid=$src_uuid|duuid=$dst_uuid|tunnelid=$tunnelid|monitortag=$monitortag|parentid=$parent_session_id|parentst=$parent_start_time|tunnel=$tunnel|associd=$assoc_id|chunk=$chunks|chunksent=$chunks_sent|chunkrcvd=$chunks_received|ruleuuid=$rule_uuid|http2conn=$http2_connection|appflap=$link_change_count|policyid=$policy_id|dynusrgrp=$dynusergroup_name|xffip=$xff_ip|scat=$src_category|sprofile=$src_profile|smodel=$src_model|sven=$src_vendor|sosfam=$src_osfamily|sosver=$src_osversion|shost=$src_host|smac=$src_mac|dcat=$dst_category|dprofile=$dst_profile|dmodel=$dst_model|dven=$dst_vendor|dosfam=$dst_osfamily|dosver=$dst_osversion|dhost=$dst_host|dmac=$dst_mac|contid=$container_id|podnamespace=$pod_namespace|podname=$pod_name|sedl=$src_edl|dedl=$dst_edl|hostid=$hostid|srnum=$serialnumber|sessionown=$session_owner|subcatapp=$subcategory_of_app|appcat=$category_of_app|apptech=$technology_of_app|apprisk=$risk_of_app|appchar=$characteristic_of_app|appcont=$container_of_app|tunneledapp=$tunneled_app|appsaas=$is_saas_of_app|appstate=$sanctioned_state_of_app|offloaded=$offloaded|flowtype=$flow_type|cluster=$cluster_name|link=$link_switches|sdag=$src_dag|ddag=$dst_dag - Threat
serial=$serial|type=$type|subtype=$subtype|time_generated=$cef-formatted-time_generated|src=$src|dst=$dst|natsrc=$natsrc|natdst=$natdst|rule=$rule|suser=$srcuser|duser=$dstuser|app=$app|vsys=$vsys|from=$from|to=$to|inboundif=$inbound_if|outboundif=$outbound_if|logset=$logset|sessionid=$sessionid|repeatcnt=$repeatcnt|sport=$sport|dport=$dport|natsport=$natsport|natdport=$natdport|flags=$flags|proto=$proto|act=$action|misc=$misc|threatid=$threatid|cat=$category|severity=$severity|dir=$direction|seqno=$seqno|actflags=$actionflags|sloc=$srcloc|dloc=$dstloc|contenttype=$contenttype|pcapip=$pcap_id|filedigest=$filedigest|cloud=$cloud|urlidx=$url_idx|useragent=$user_agent|filetype=$filetype|xff=$xff|ref=$referer|sender=$sender|sub=$subject|recipient=$recipient|reportid=$reportid|vsysname=$vsys_name|dvc=$device_name|suuid=$src_uuid|duuid=$dst_uuid|http_method=$http_method|tunnelid=$tunnel_id|monitortag=$monitortag|tunnel=$tunnel|thrcategory=$thr_category|contentver=$contentver|ppid=$ppid|httpheaders=$http_headers|urlcategory=$url_category_list|ruleuuid=$rule_uuid|http2conn=$http2_connection|dynusrgrp=$dynusergroup_name|xffip=$xff_ip|scat=$src_category|sprofile=$src_profile|smodel=$src_model|sven=$src_vendor|sosfam=$src_osfamily|sosver=$src_osversion|shost=$src_host|smac=$src_mac|dcat=$dst_category|dprofile=$dst_profile|dmodel=$dst_model|dven=$dst_vendor|dosfam=$dst_osfamily|dosver=$dst_osversion|dhost=$dst_host|dmac=$dst_mac|contid=$container_id|podnamespace=$pod_namespace|podname=$pod_name|hostid=$hostid|srnum=$serialnumber|reason=$reason|justification=$justification|subcatApp=$subcategory_of_app|appcat=$category_of_app|apptech=$technology_of_app|apprisk=$risk_of_app|appchar=$characteristic_of_app|appcont=$container_of_app|tunneledapp=$tunneled_app|appsaas=$is_saas_of_app|appstate=$sanctioned_state_of_app|cloudreportid=$cloud_reportid|cluster=$cluster_name|flowtype=$flow_type - Authentication
receive_time=$receive_time|serial=$serial|type=$type|subtype=$subtype|time_generated=$cef-formatted-time_generated|vsys=$vsys|ip=$ip|user=$user|normalize_user=$normalize_user|object=$object|authpolicy=$authpolicy|repeatcnt=$repeatcnt|authid=$authid|vendor=$vendor|logset=$logset|serverprofile=$serverprofile|desc=$desc|clienttype=$clienttype|event=$event|factorno=$factorno|seqno=$seqno|actionflags=$actionflags|dg_hier_level_1=$dg_hier_level_1|dg_hier_level_2=$dg_hier_level_2|dg_hier_level_3=$dg_hier_level_3|dg_hier_level_4=$dg_hier_level_4|vsys_name=$vsys_name|device_name=$device_name|vsys_id=$vsys_id|authproto=$authproto|rule_uuid=$rule_uuid|high_res_timestamp=$high_res_timestamp|src_category=$src_category|src_profile=$src_profile|src_model=$src_model|src_vendor=$src_vendor|src_osfamily=$src_osfamily|src_osversion=$src_osversion|src_host=$src_host|src_mac=$src_mac|region=$region|user_agent=$user_agent|sessionid=$sessionid|cluster_name=$cluster_name - HIP Match
receive_time=$receive_time|serial=$serial|type=$type|subtype=$subtype|time_generated=$cef-formatted-time_generated|srcuser=$srcuser|vsys=$vsys|machinename=$machinename|os=$os|src=$src|matchname=$matchname|repeatcnt=$repeatcnt|matchtype=$matchtype|seqno=$seqno|actionflags=$actionflags|dg_hier_level_1=$dg_hier_level_1|dg_hier_level_2=$dg_hier_level_2|dg_hier_level_3=$dg_hier_level_3|dg_hier_level_4=$dg_hier_level_4|vsys_name=$vsys_name|device_name=$device_name|vsys_id=$vsys_id|srcipv6=$srcipv6|hostid=$hostid|serialnumber=$serialnumber|mac=$mac|high_res_timestamp=$high_res_timestamp|cluster_name=$cluster_name - User ID
receive_time=$receive_time|serial=$serial|type=$type|subtype=$subtype|time_generated=$cef-formatted-time_generated|vsys=$vsys|ip=$ip|user=$user|datasourcename=$datasourcename|eventid=$eventid|repeatcnt=$repeatcnt|timeout=$timeout|beginport=$beginport|endport=$endport|datasource=$datasource|datasourcetype=$datasourcetype|seqno=$seqno|actionflags=$actionflags|dg_hier_level_1=$dg_hier_level_1|dg_hier_level_2=$dg_hier_level_2|dg_hier_level_3=$dg_hier_level_3|dg_hier_level_4=$dg_hier_level_4|vsys_name=$vsys_name|device_name=$device_name|vsys_id=$vsys_id|factortype=$factortype|factorcompletiontime=$factorcompletiontime|factorno=$factorno|ugflags=$ugflags|userbysource=$userbysource|tag_name=$tag_name|high_res_timestamp=$high_res_timestamp|origindatasource=$origindatasource|cluster_name=$cluster_name - Tunnel Inspection
receive_time=$receive_time|serial=$serial|type=$type|subtype=$subtype|time_generated=$cef-formatted-time_generated|src=$src|dst=$dst|natsrc=$natsrc|natdst=$natdst|rule=$rule|srcuser=$srcuser|dstuser=$dstuser|app=$app|vsys=$vsys|from=$from|to=$to|inbound_if=$inbound_if|outbound_if=$outbound_if|logset=$logset|sessionid=$sessionid|repeatcnt=$repeatcnt|sport=$sport|dport=$dport|natsport=$natsport|natdport=$natdport|flags=$flags|proto=$proto|act=$action|severity=$severity|seqno=$seqno|actionflags=$actionflags|srcloc=$srcloc|dstloc=$dstloc|dg_hier_level_1=$dg_hier_level_1|dg_hier_level_2=$dg_hier_level_2|dg_hier_level_3=$dg_hier_level_3|dg_hier_level_4=$dg_hier_level_4|vsys_name=$vsys_name|device_name=$device_name|tunnelid=$tunnelid|monitortag=$monitortag|parent_session_id=$parent_session_id|parent_start_time=$parent_start_time|tunnel=$tunnel|bytes=$bytes|bytes_sent=$bytes_sent|bytes_received=$bytes_received|pkt=$packets|pkts_sent=$pkts_sent|pkts_received=$pkts_received|max_encap=$max_encap|unknown_proto=$unknown_proto|strict_check=$strict_check|tunnel_fragment=$tunnel_fragment|sessions_created=$sessions_created|sessions_closed=$sessions_closed|session_end_reason=$session_end_reason|action_source=$action_source|start=$start|elapsed=$elapsed|tunnel_insp_rule=$tunnel_insp_rule|remote_user_ip=$remote_user_ip|remote_user_id=$remote_user_id|rule_uuid=$rule_uuid|pcap_id=$pcap_id|dynusergroup_name=$dynusergroup_name|src_edl=$src_edl|dst_edl=$dst_edl|high_res_timestamp=$high_res_timestamp|nssai_sd=$nssai_sd|nssai_sst=$nssai_sst|pdu_session_id=$pdu_session_id|subcategory_of_app=$subcategory_of_app|category_of_app=$category_of_app|technology_of_app=$technology_of_app|risk_of_app=$risk_of_app|characteristic_of_app=$characteristic_of_app|container_of_app=$container_of_app|is_saas_of_app=$is_saas_of_app|sanctioned_state_of_app=$sanctioned_state_of_app|cluster_name=$cluster_name - Config
receive_time=$receive_time|serial=$serial|type=$type|subtype=$subtype|time_generated=$cef-formatted-time_generated|host=$host|vsys=$vsys|cmd=$cmd|admin=$admin|client=$client|result=$result|path=$path|seqno=$seqno|actionflags=$actionflags|dg_hier_level_1=$dg_hier_level_1|dg_hier_level_2=$dg_hier_level_2|dg_hier_level_3=$dg_hier_level_3|dg_hier_level_4=$dg_hier_level_4|vsys_name=$vsys_name|device_name=$device_name|dg_id=$dg_id|comment=$comment|high_res_timestamp=$high_res_timestamp|before-change-detail=$before-change-detail|after-change-detail=$after-change-detail - System
receive_time=$receive_time|serial=$serial|type=$type|subtype=$subtype|time_generated=$cef-formatted-time_generated|vsys=$vsys|eventid=$eventid|object=$object|module=$module|severity=$severity|opaque=$opaque|seqno=$seqno|actionflags=$actionflags|dg_hier_level_1=$dg_hier_level_1|dg_hier_level_2=$dg_hier_level_2|dg_hier_level_3=$dg_hier_level_3|dg_hier_level_4=$dg_hier_level_4|vsys_name=$vsys_name|device_name=$device_name|high_res_timestamp=$high_res_timestamp - Correleated Events
receive_time=$receive_time|serial=$serial|type=$type|subtype=$subtype|time_generated=$cef-formatted-time_generated|src=$src|srcuser=$srcuser|vsys=$vsys|category=$category|severity=$severity|dg_hier_level_1=$dg_hier_level_1|dg_hier_level_2=$dg_hier_level_2|dg_hier_level_3=$dg_hier_level_3|dg_hier_level_4=$dg_hier_level_4|vsys_name=$vsys_name|device_name=$device_name|vsys_id=$vsys_id|objectname=$objectname|object_id=$object_id|evidence=$evidence - GlobalProtect
receive_time=$receive_time|serial=$serial|type=$type|subtype=$subtype|time_generated=$cef-formatted-time_generated|vsys=$vsys|eventid=$eventid|stage=$stage|auth_method=$auth_method|tunnel_type=$tunnel_type|srcuser=$srcuser|srcregion=$srcregion|machinename=$machinename|public_ip=$public_ip|public_ipv6=$public_ipv6|private_ip=$private_ip|private_ipv6=$private_ipv6|hostid=$hostid|serialnumber=$serialnumber|client_ver=$client_ver|client_os=$client_os|client_os_ver=$client_os_ver|repeatcnt=$repeatcnt|reason=$reason|error=$error|opaque=$opaque|status=$status|location=$location|login_duration=$login_duration|connect_method=$connect_method|error_code=$error_code|portal=$portal|seqno=$seqno|actionflags=$actionflags|selection_type=$selection_type|response_time=$response_time|priority=$priority|attempted_gateways=$attempted_gateways|gateway=$gateway|dg_hier_level_1=$dg_hier_level_1|dg_hier_level_2=$dg_hier_level_2|dg_hier_level_3=$dg_hier_level_3|dg_hier_level_4=$dg_hier_level_4|vsys_name=$vsys_name|device_name=$device_name|vsys_id=$vsys_id|cluster_name=$cluster_name - Decryption
serial=$serial|type=$type|subtype=$subtype|configver=$config_ver|time_generated=$cef-formatted-time_generated|src=$src|dst=$dst|natsrc=$natsrc|natdst=$natdst|rule=$rule|suser=$srcuser|duser=$dstuser|app=$app|vsys=$vsys|from=$from|to=$to|inboundif=$inbound_if|outboundif=$outbound_if|logset=$logset|time_received=$time_received|sessionid=$sessionid|repeatcnt=$repeatcnt|sport=$sport|dport=$dport|natsport=$natsport|natdport=$natdport|flags=$flags|proto=$proto|act=$action|tunnel=$tunnel|suuid=$src_uuid|duuid=$dst_uuid|ruleuuid=$rule_uuid|hsstagec2f=$hs_stage_c2f|hsstagef2s=$hs_stage_f2s|tlsver=$tls_version|tlskeyxchg=$tls_keyxchg|tlsenc=$tls_enc|tlsauth=$tls_auth|policyname=$policy_name|eccurve=$ec_curve|errindex=$err_index|rootstatus=$root_status|chainstatus=$chain_status|proxytype=$proxy_type|certserial=$cert_serial|fingerprint=$fingerprint|notbefore=$notbefore|notafter=$notafter|certver=$cert_ver|certsize=$cert_size|cnlen=$cn_len|issuerlen=$issuer_len|rootcnlen=$rootcn_len|snilen=$sni_len|certflags=$cert_flags|cn=$cn|issuercn=$issuer_cn|rootcn=$root_cn|sni=$sni|err=$error|contid=$container_id|podnamespace=$pod_namespace|podname=$pod_name|sedl=$src_edl|dedl=$dst_edl|scat=$src_category|sprofile=$src_profile|smodel=$src_model|sven=$src_vendor|src_osfamily=$src_osfamily|sosver=$src_osversion|shost=$src_host|smac=$src_mac|dcat=$dst_category|dprofile=$dst_profile|dmodel=$dst_model|dven=$dst_vendor|dosfam=$dst_osfamily|dosver=$dst_osversion|dhost=$dst_host|dmac=$dst_mac|seqno=$seqno|actflag=$actionflags|vsysname=$vsys_name|dvc=$device_name|vsysid=$vsys_id|appsubcat=$subcategory_of_app|appcat=$category_of_app|apptech=$technology_of_app|apprisk=$risk_of_app|appchar=$characteristic_of_app|appcont=$container_of_app|appsaas=$is_saas_of_app|appstate=$sanctioned_state_of_app|cluster=$cluster_name|sdag=$src_dag|ddag=$dst_dag
- Traffic
- For Step 1.4, use
Validation
Run the Agent’s status subcommand and look for palo_alto_panorama under the Checks section.
Data Collected
Logs
The Palo Alto Panorama integration collects Traffic, Threat, Authentication, HIP Match, User ID, Tunnel Inspection, Config, System, Correlated Events, URL Filtering, Data Filtering, GlobalProtect, and Decryption logs.
Metrics
The Palo Alto Panorama integration does not include any metrics.
Events
The Palo Alto Panorama integration does not include any events.
Service Checks
The Palo Alto Panorama integration does not include any service checks.
Troubleshooting
Permission denied while port binding:
If you see a Permission denied error while port binding in the Agent logs, see the following instructions:
Binding to a port number under 1024 requires elevated permissions. Grant access to the port using the
setcapcommand:Grant access to the port using the
setcapcommand:sudo setcap CAP_NET_BIND_SERVICE=+ep /opt/datadog-agent/bin/agent/agentVerify the setup is correct by running the
getcapcommand:sudo getcap /opt/datadog-agent/bin/agent/agentWith the expected output:
/opt/datadog-agent/bin/agent/agent = cap_net_bind_service+epNote: Re-run this
setcapcommand every time you upgrade the Agent.
Data is not being collected:
Make sure that traffic is bypassed from the configured port if the firewall is enabled.
Port already in use:
If you see the Port <PORT-NO> Already in Use error, see the following instructions. The example below is for PORT-NO = 514:
On systems using Syslog, if the Agent listens for Zeek logs on port 514, the following error can appear in the Agent logs: Can't start UDP forwarder on port 514: listen udp :514: bind: address already in use.
This error occurs because by default, Syslog listens on port 514. To resolve this error, take one of the following steps:
- Disable Syslog
- Configure the Agent to listen on a different, available port
For further assistance, contact Datadog support.
