- 重要な情報
- はじめに
- Datadog
- Datadog サイト
- DevSecOps
- AWS Lambda のサーバーレス
- エージェント
- インテグレーション
- コンテナ
- ダッシュボード
- アラート設定
- ログ管理
- トレーシング
- プロファイラー
- タグ
- API
- Service Catalog
- Session Replay
- Continuous Testing
- Synthetic モニタリング
- Incident Management
- Database Monitoring
- Cloud Security Management
- Cloud SIEM
- Application Security Management
- Workflow Automation
- CI Visibility
- Test Visibility
- Intelligent Test Runner
- Code Analysis
- Learning Center
- Support
- 用語集
- Standard Attributes
- ガイド
- インテグレーション
- エージェント
- OpenTelemetry
- 開発者
- 認可
- DogStatsD
- カスタムチェック
- インテグレーション
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Recommended Monitor
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- サービスのチェック
- IDE インテグレーション
- コミュニティ
- ガイド
- API
- モバイルアプリケーション
- CoScreen
- Cloudcraft
- アプリ内
- Service Management
- インフラストラクチャー
- アプリケーションパフォーマンス
- APM
- Continuous Profiler
- データベース モニタリング
- Data Streams Monitoring
- Data Jobs Monitoring
- Digital Experience
- Software Delivery
- CI Visibility (CI/CDの可視化)
- CD Visibility
- Test Visibility
- Intelligent Test Runner
- Code Analysis
- Quality Gates
- DORA Metrics
- セキュリティ
- セキュリティの概要
- Cloud SIEM
- クラウド セキュリティ マネジメント
- Application Security Management
- AI Observability
- ログ管理
- Observability Pipelines(観測データの制御)
- ログ管理
- 管理
Handling Private Action Credentials
このページは日本語には対応しておりません。随時翻訳に取り組んでいます。翻訳に関してご質問やご意見ございましたら、お気軽にご連絡ください。
このページは日本語には対応しておりません。随時翻訳に取り組んでいます。翻訳に関してご質問やご意見ございましたら、お気軽にご連絡ください。
Join the Preview!
Private Actions are in Preview. Use this form to request access today.
Request AccessOverview
Private actions allow your Datadog workflows and apps to interact with services hosted on your private network without exposing your services to the public internet. To use private actions, you must use Docker to install a private action runner on a host in your network and pair the runner with a Datadog Connection. For more information on setting up a runner and pairing it with a connection, see Private Actions for Workflows or Private Actions for App Builder.
Some private actions, such as Jenkins and PostgreSQL, require credentials to function. To configure credentials for a private action, you must:
- Create a JSON file for the credential and use the JSON structure provided in Credential files.
- Store your credential files in the configuration directory you created during setup.
- Specify the path to the credential in the runner’s connection. Use the path to the credential on the container. For example:
/etc/dd-action-runner/creds/jenkins_creds.json.
Credential files
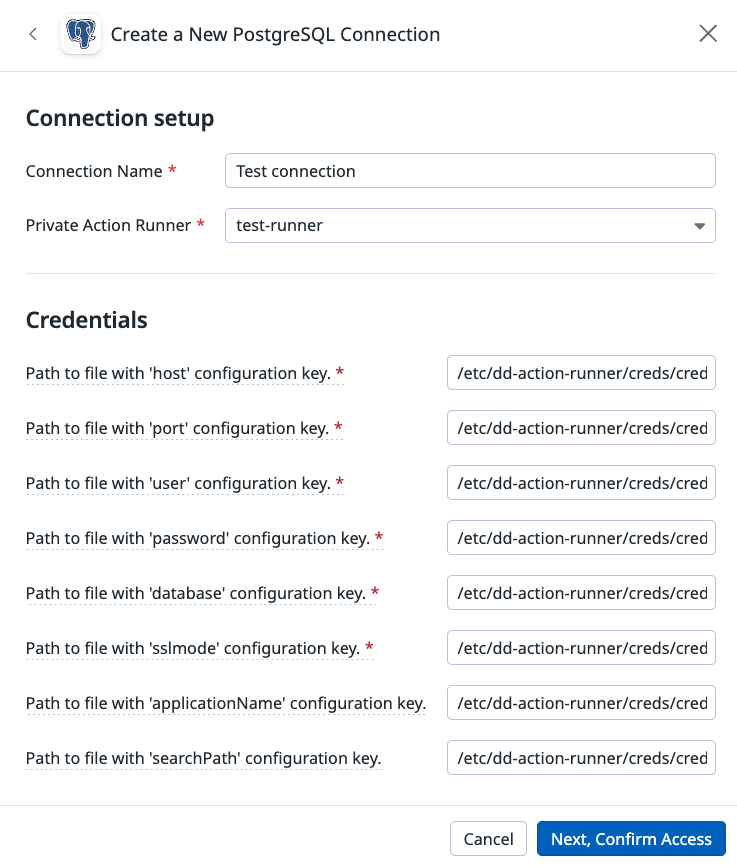
The PostgreSQL connection accepts the following credentials:
| Credential | Required | Description |
|---|---|---|
host | Yes | The name of the host to connect to. For more information, see the official PostGreSQL documentation. |
port | Yes | The port number to connect to at the server host, or socket filename extension for UNIX-domain connections. For more information, see the official PostGreSQL documentation. |
user | Yes | The PostgreSQL user name to connect as. For more information, see the official PostGreSQL documentation. |
password | Yes | The password to use if the server demands password authentication. For more information, see the official PostGreSQL documentation. |
database | Yes | The database name. For more information, see the official PostGreSQL documentation. |
sslmode | Yes | This option determines whether or with what priority a secure SSL TCP/IP connection is negotiated with the server. Available options are require and disable.For more information, see the official PostGreSQL documentation. |
applicationName | No | The name of the application connecting to the PostGreSQL server. For more information, see the official PostGreSQL documentation. |
searchPath | No | Set a schema search path. For more information, see the official PostGreSQL documentation. |
Include all credentials in a single file.
In the runner’s connection, specify the location of the credential file on the private action runner’s container. In this example, all three credentials are stored in a single file. Replace the capitalized example values with your credentials.
/etc/dd-action-runner/creds/creds.pgpass
{
"auth_type": "Token Auth",
"credentials": [
{
"tokenName": "host",
"tokenValue": "YOUR_HOST_NAME"
},
{
"tokenName": "port",
"tokenValue": "YOUR_PORT"
},
{
"tokenName": "user",
"tokenValue": "YOUR_USER"
},
{
"tokenName": "password",
"tokenValue": "YOUR_PASSWORD"
},
{
"tokenName": "database",
"tokenValue": "YOUR_DATABASE_NAME"
},
{
"tokenName": "sslmode",
"tokenValue": "disable"
},
{
"tokenName": "applicationName",
"tokenValue": "YOUR_APPLICATION_NAME"
},
{
"tokenName": "searchPath",
"tokenValue": "YOUR_SEARCH_PATH"
}
]
}In the runner’s connection, specify the location of the credential file on the private action runner’s container. Your PostgreSQL connection points to the same path for all credentials. In this example, the credential file is stored at /etc/dd-action-runner/creds/creds.pgpass on the runner.
Jenkins connections require three credentials:
- username: The username of the Jenkins user that you want to use to authenticate with the Jenkins server. This user must have the necessary permissions to perform the actions you want to perform.
- token: The API token of the Jenkins user that you want to use to authenticate with the Jenkins server. This user must have the necessary permissions to perform the actions you want to perform. You can generate an API token in the Jenkins user settings.
- domain: The domain of the Jenkins server that you want to connect to.
You can include all credentials in a single file or store each credential in a separate file.
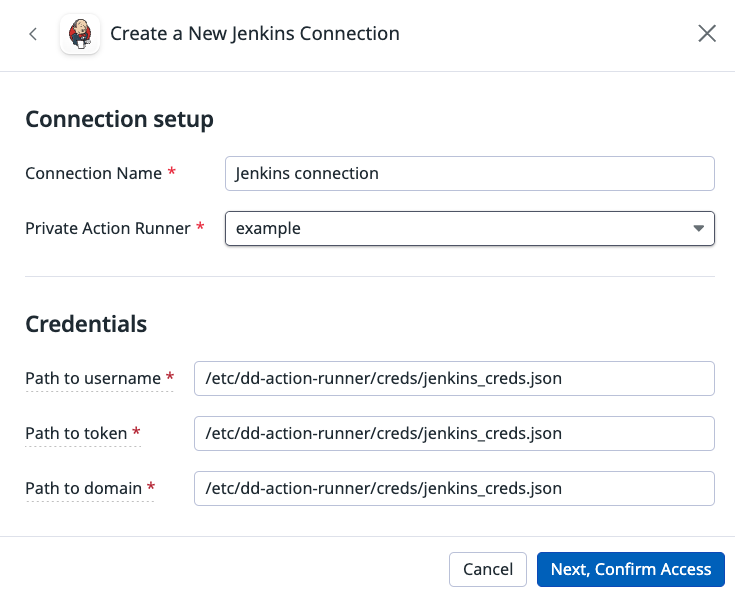
Single file example
Single file example
In the runner’s connection, specify the location of the credential file on the private action runner’s container. In this example, all three credentials are stored in a single file. Replace USERNAME, TOKEN, and DOMAIN with your username, token, and domain.
/etc/dd-action-runner/creds/jenkins_creds.json
{
"auth_type": "Token Auth",
"credentials": [
{
"tokenName": "username",
"tokenValue": "USERNAME"
},
{
"tokenName": "token",
"tokenValue": "TOKEN"
},
{
"tokenName": "domain",
"tokenValue": "DOMAIN"
}
]
}In the runner’s connection, specify the location of the credential file on the private action runner’s container. Your Jenkins connection points to the same path for all credentials. In this example, the credential file is stored at /etc/dd-action-runner/creds/jenkins_creds.json on the runner.
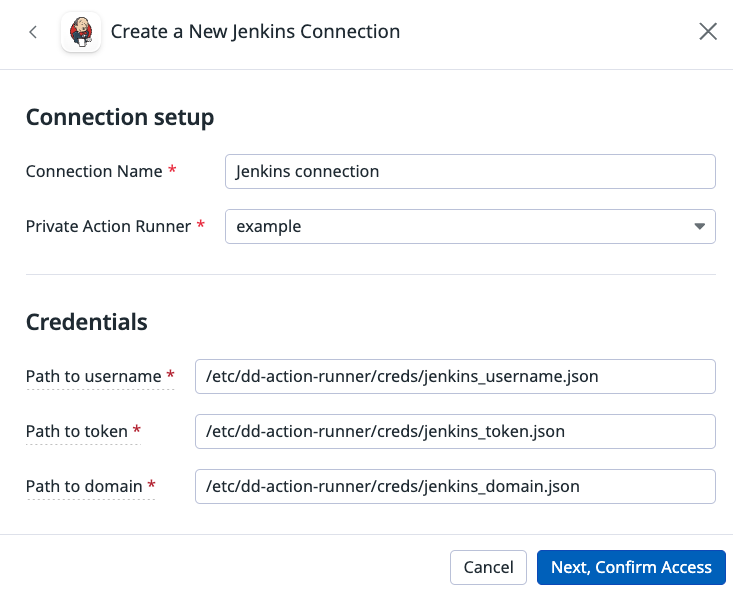
Multiple file example
Multiple file example
In this example, each Jenkins credential is stored in a separate file.
For the username credential, replace USERNAME with your username.
/etc/dd-action-runner/creds/jenkins_username.json
{
"auth_type": "Token Auth",
"credentials": [
{
"tokenName": "username",
"tokenValue": "USERNAME"
}
]
}For the token credential, replace TOKEN with your token.
/etc/dd-action-runner/creds/jenkins_token.json
{
"auth_type": "Token Auth",
"credentials": [
{
"tokenName": "token",
"tokenValue": "TOKEN"
}
]
}For the domain credential, replace DOMAIN with your domain.
/etc/dd-action-runner/creds/jenkins_domain.json
{
"auth_type": "Token Auth",
"credentials": [
{
"tokenName": "domain",
"tokenValue": "DOMAIN"
}
]
}In the runner’s connection, specify the location of the credential file on the private action runner’s container. Your Jenkins connection points to the path to each credential. In this example, the credential files are stored at the following locations on the runner:
/etc/dd-action-runner/creds/jenkins_username.json/etc/dd-action-runner/creds/jenkins_token.json/etc/dd-action-runner/creds/jenkins_domain.json
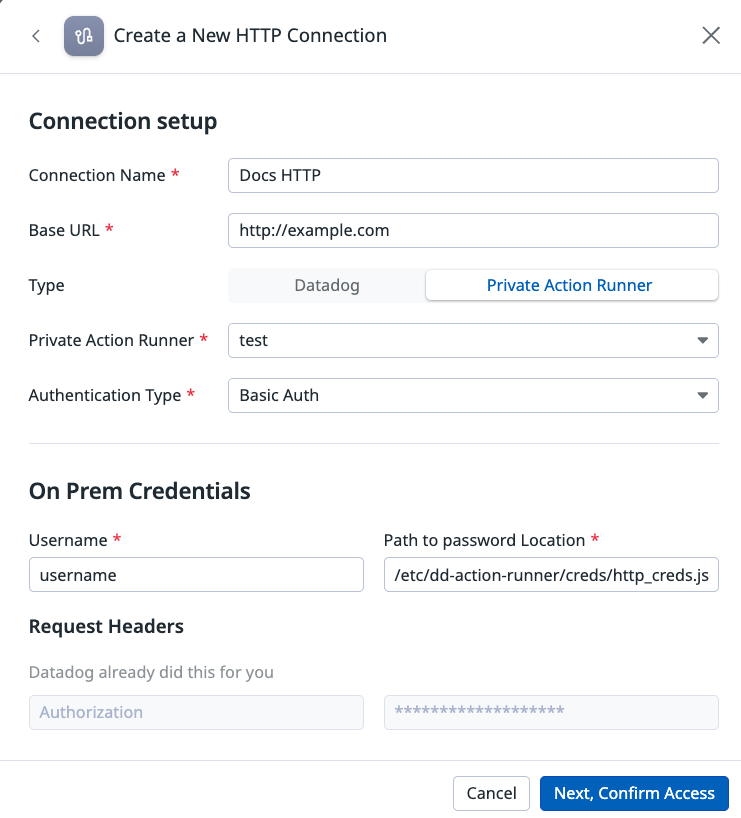
Basic authentication
Basic authentication for the HTTP connection requires a credential file with a username and a password.
Replace USERNAME and PASSWORD with your username and password.
/etc/dd-action-runner/creds/http_creds.json
{
"auth_type": "Basic Auth",
"credentials": [
{
"username": "USERNAME",
"password": "PASSWORD"
}
]
}In the runner’s connection, specify the location of the credential file on the private action runner’s container. In this example, the credential file is stored at /etc/dd-action-runner/creds/http_creds.json on the runner.
Token authentication
Token authentication for the HTTP connection requires a credential file with an array of token names and values.
The example below includes two tokens named TOKEN1 and TOKEN2. Replace the example token names and values with your token names and values.
/etc/dd-action-runner/creds/http_creds.json
{
"auth_type": "Token Auth",
"credentials": [
{
"tokenName": "TOKEN1",
"tokenValue": "VALUE1"
},
{
"tokenName": "TOKEN2",
"tokenValue": "VALUE2"
}
]
}In the runner’s connection, specify the location of the credential file on the private action runner’s container. In this example, the credential file is stored at /etc/dd-action-runner/creds/http_creds.json on the runner.