- Essentials
- Getting Started
- Datadog
- Datadog Site
- DevSecOps
- Serverless for AWS Lambda
- Agent
- Integrations
- Containers
- Dashboards
- Monitors
- Logs
- APM Tracing
- Profiler
- Tags
- API
- Service Catalog
- Session Replay
- Continuous Testing
- Synthetic Monitoring
- Incident Management
- Database Monitoring
- Cloud Security Management
- Cloud SIEM
- Application Security Management
- Workflow Automation
- CI Visibility
- Test Visibility
- Test Impact Analysis
- Code Analysis
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- OpenTelemetry
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Recommended Monitor
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- Service Checks
- IDE Plugins
- Community
- Guides
- Administrator's Guide
- API
- Datadog Mobile App
- CoScreen
- Cloudcraft
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Sheets
- Monitors and Alerting
- Infrastructure
- Metrics
- Watchdog
- Bits AI
- Service Catalog
- API Catalog
- Error Tracking
- Service Management
- Infrastructure
- Application Performance
- APM
- Continuous Profiler
- Database Monitoring
- Data Streams Monitoring
- Data Jobs Monitoring
- Digital Experience
- Real User Monitoring
- Product Analytics
- Synthetic Testing and Monitoring
- Continuous Testing
- Software Delivery
- CI Visibility
- CD Visibility
- Test Optimization
- Code Analysis
- Quality Gates
- DORA Metrics
- Security
- Security Overview
- Cloud SIEM
- Cloud Security Management
- Application Security Management
- AI Observability
- Log Management
- Observability Pipelines
- Log Management
- Administration
SAML Group Mapping
Overview
With Datadog, you can map attributes in your Identity Provider (IdP)’s response to Datadog entities.
You can map attributes to the following principals:
Users with the Access Management permission can assign or remove Datadog principals based on a user’s SAML-assigned attributes.
Setting up a mapping from SAML attributes to Datadog entities allows you to manage users solely in your identity provider. The system then provisions users in Datadog according to the mappings you set up.
Prerequisites
It’s important to understand what is sent in an assertion before turning on mappings, as mappings require correct attributes. Every IdP has specific mappings. For example, Azure works with object IDs, and Okta requires you to set attributes in Okta settings. Datadog recommends cross-referencing with built-in browser tooling such as Chrome DevTools or browser extensions and validating your SAML assertions before creating mappings.
Map SAML attributes to Datadog roles
Cross-reference and validate your SAML assertion to understand your IdP’s attributes.
Go to Organization Settings and click the SAML Group Mappings tab.
If it is visible, ensure the Role Mappings tab is selected.
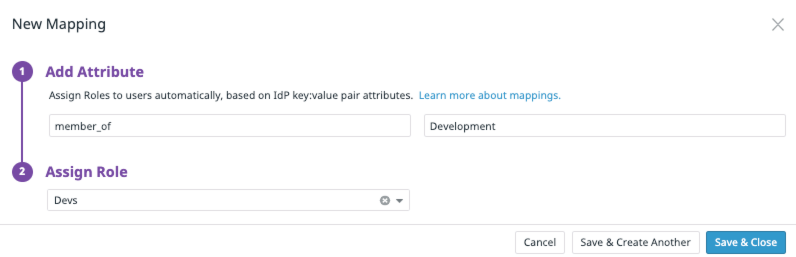
Click New Mapping. A dialog box appears.
Specify the SAML identity provider
key-valuepair that you want to associate with an existing Datadog role (either default or custom). Note: These entries are case-sensitive. For example, if you want all users whosemember_ofattribute has a value ofDevelopmentto be assigned to a custom Datadog role calledDevs:Note: Every identity provider is different. Some allow you to set your attribute key or label. Others provide one by default. Datadog recommends you use an assertion inspector on your login to view the details of your particular assertion to understand how your Identity Provider is sending your group membership.
If you have not already done so, enable mappings by clicking Enable Mappings.
When a user logs in who has the specified identity provider attribute, they are automatically assigned the Datadog role. Likewise, if someone has that identity provider attribute removed, they lose access to the role (unless another mapping adds it).
Important: If a user does not match any mapping, they lose any roles they had previously and are prevented from logging into the org with SAML. Double-check your mapping definitions and inspect your own assertions before enabling Mappings to prevent any scenarios where your users are unable to login.
Make changes to a mapping by clicking the pencil (Edit) icon, or remove a mapping by clicking the garbage (Delete) icon. These actions affect only the mapping, not the identity provider attributes or the Datadog roles.
Alternatively, you can create and change mappings of SAML attributes to Datadog roles with the authn_mappings endpoint. For more information, see Federated Authentication to Role Mapping API.
Map SAML attributes to Teams
- Ensure you selected either SAML or All sources when choosing your provisioning source for team memberships.
- Cross-reference and validate your SAML assertion to understand your IdP’s attributes.
- Go to Organization Settings and click the SAML Group Mappings tab.
- Ensure the Team Mappings tab is selected.
- Click New Mapping. A dialog box appears.
- Specify the SAML identity provider
key-valuepair that you want to associate with a Datadog Team. Note: These entries are case-sensitive. Note: Every identity provider is different. Some allow you to set your attribute key or label. Others provide one by default. Datadog recommends you use an assertion inspector on your login to view the details of your particular assertion to understand how your Identity Provider is sending your group membership. - Select a Team from the dropdown menu.
- To add an additional mapping, click Add Row.
- When you are done adding mappings, click Create.
- If you have not already done so, enable mappings by clicking Enable Mappings.
Make changes to a mapping by clicking the pencil (Edit) icon, or remove a mapping by clicking the garbage (Delete) icon. These actions affect only the mapping, not the identity provider attributes or the Datadog Team.
Note: Unlike Roles, Teams do not affect the login experience in any way. Datadog uses Team mapping purely as a provisioning source. For example, when a user does not belong to any Teams, they can still sign in to Datadog.