- Essentials
- Getting Started
- Datadog
- Datadog Site
- DevSecOps
- Serverless for AWS Lambda
- Agent
- Integrations
- Containers
- Dashboards
- Monitors
- Logs
- APM Tracing
- Profiler
- Tags
- API
- Service Catalog
- Session Replay
- Continuous Testing
- Synthetic Monitoring
- Incident Management
- Database Monitoring
- Cloud Security Management
- Cloud SIEM
- Application Security Management
- Workflow Automation
- CI Visibility
- Test Visibility
- Test Impact Analysis
- Code Analysis
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- OpenTelemetry
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Recommended Monitor
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- Service Checks
- IDE Plugins
- Community
- Guides
- Administrator's Guide
- API
- Datadog Mobile App
- CoScreen
- Cloudcraft
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Sheets
- Monitors and Alerting
- Infrastructure
- Metrics
- Watchdog
- Bits AI
- Service Catalog
- API Catalog
- Error Tracking
- Service Management
- Infrastructure
- Application Performance
- APM
- Continuous Profiler
- Database Monitoring
- Data Streams Monitoring
- Data Jobs Monitoring
- Digital Experience
- Real User Monitoring
- Product Analytics
- Synthetic Testing and Monitoring
- Continuous Testing
- Software Delivery
- CI Visibility
- CD Visibility
- Test Optimization
- Code Analysis
- Quality Gates
- DORA Metrics
- Security
- Security Overview
- Cloud SIEM
- Cloud Security Management
- Application Security Management
- AI Observability
- Log Management
- Observability Pipelines
- Log Management
- Administration
Application Threat Management
Application Security Management is not supported for your selected Datadog site ().
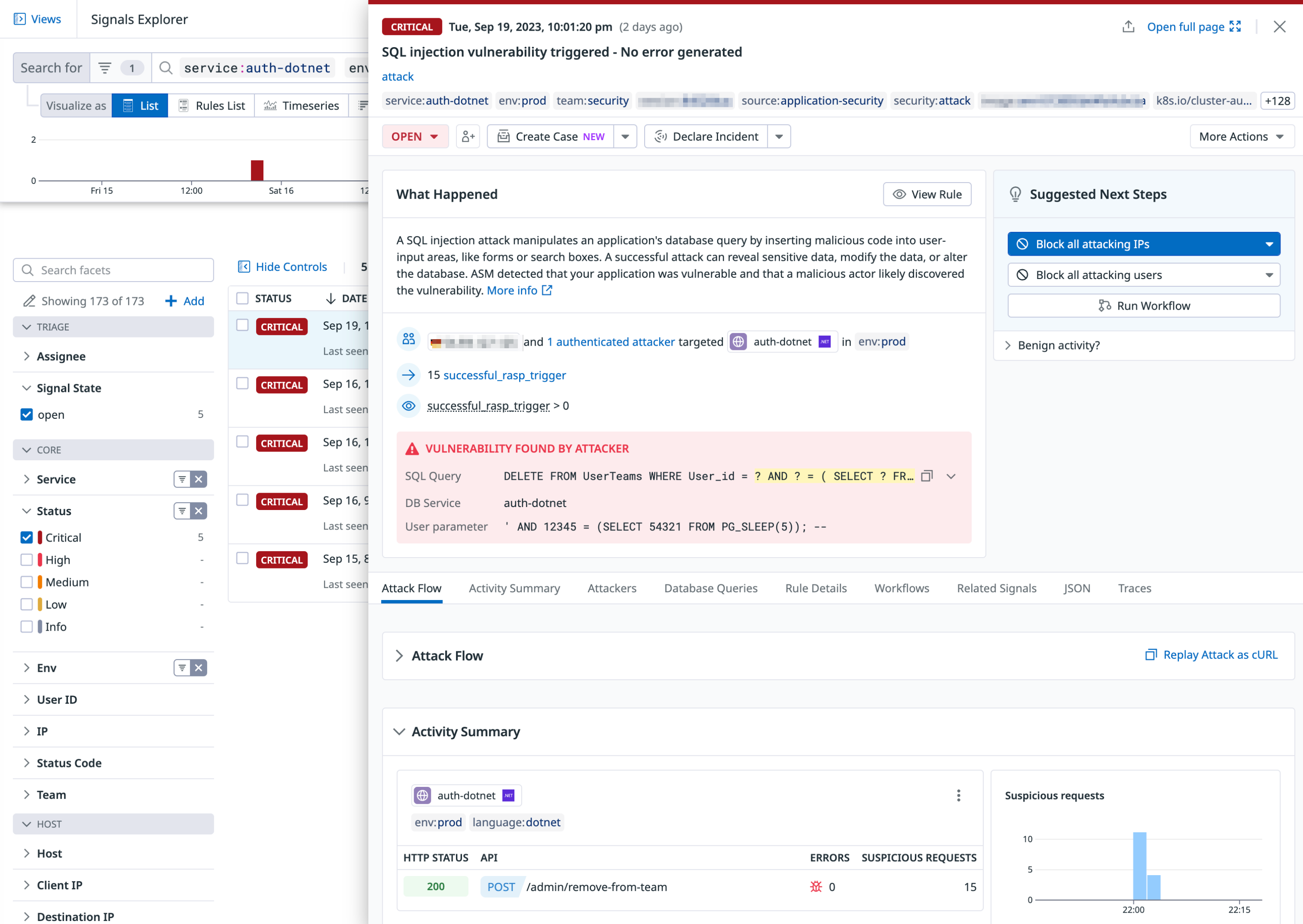
ASM Threat Management uses trace telemetry from your APM-instrumented applications to identify threats and attacks on your running services by comparing the observed behavior against known attack patterns, or by identifying business logic abuse.
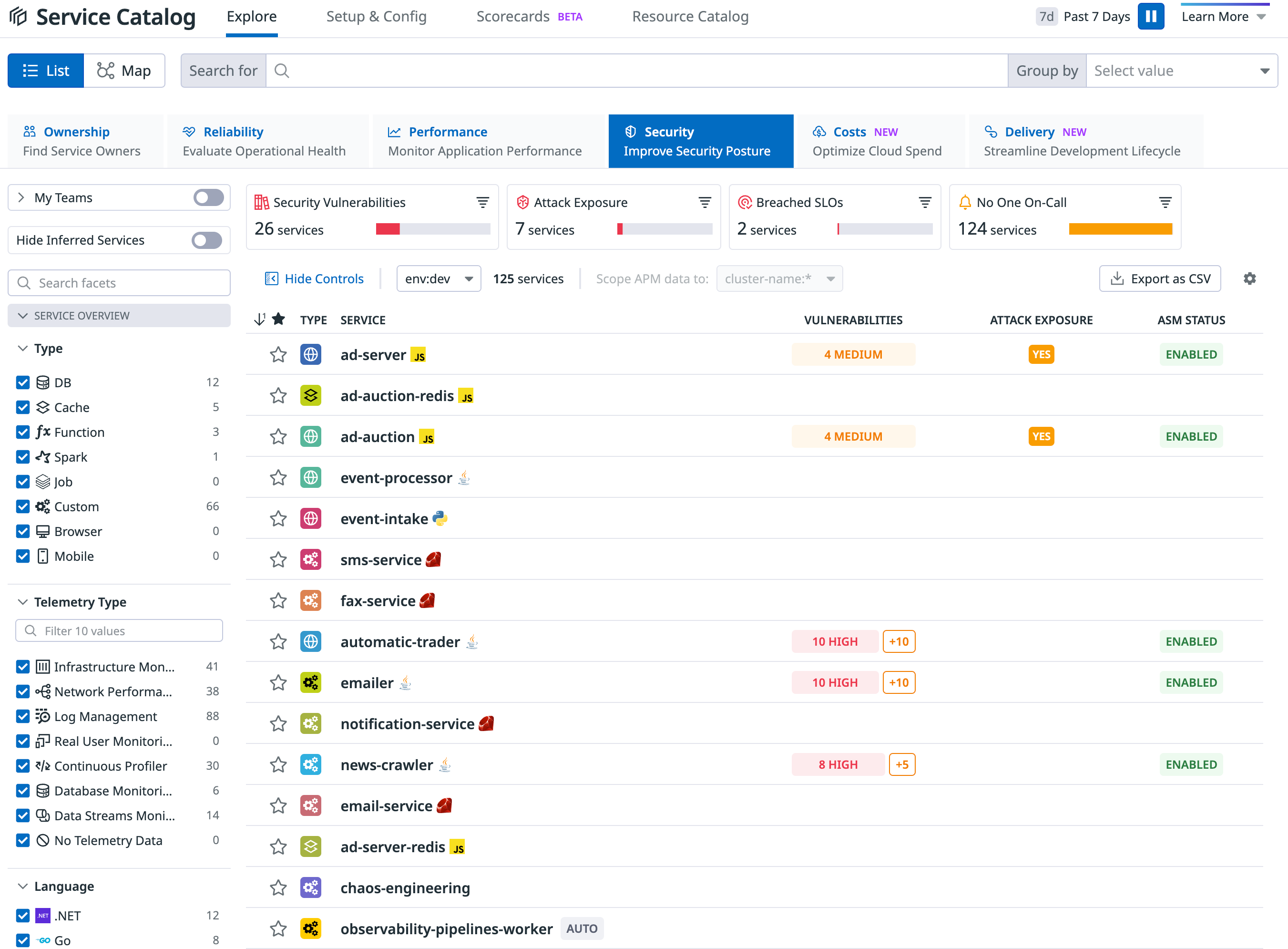
Security signals raised by Threat Monitoring are summarized and surfaced in views you already commonly visit to monitor service health and performance. The Service Catalog and individual Service Pages in APM provide insights into application threat signals, allowing you to investigate vulnerabilities, block attackers, and review attack exposures.
For additional information about how Threat Management works, read How ASM Works.
Explore threat signals
When threat data for your services is coming into Datadog, ASM Overview shows a summary of what’s happening. Here, you can enable vulnerability detection, review attacks, customize alerting and reporting, and enable ASM on your services. To investigate signals of suspicious activity, click a service’s Review link.
In the Signals Explorer, filter by attributes and facets to find critical threats. Click into a signal to see details for it, including the user information and their IP address, what rule they triggered, attack flow, and related traces and other security signals. From this page you can also click to create a case and declare an incident. For more information see Investigate Security Signals.
Create In-App WAF rules for identifying attack patterns
You can create In-App WAF rules that define what suspicious behavior looks like in your application, augmenting the default rules that come with ASM. Then specify custom rules to generate security signals from the attack attempts triggered from these rules, raising them in the Threat Monitoring views for your investigation.
Slow down attacks and attackers with ASM Protect
If your service is running an Agent with Remote Configuration enabled and a tracing library version that supports it, you can block attacks and attackers from the Datadog UI without additional configuration of the Agent or tracing libraries.
ASM Protect goes beyond Threat Detection and enables you to take blocking action to slow down attacks and attackers. Unlike perimeter WAFs that apply a broad range of rules to inspect traffic, ASM uses the full context of your application—its databases, frameworks, and programming language—to narrowly apply the most efficient set of inspection rules.
ASM leverages the same tracing libraries as Application Performance Monitoring (APM) to protect your applications against:
- Attacks: ASM’s In-App WAF inspects all incoming traffic and uses pattern-matching to detect and block malicious traffic (security traces).
- Attackers: IP addresses and authenticated users that are launching attacks against your applications are detected from the insights collected by the libraries and flagged in Security Signals.
Security traces are blocked in real time by the Datadog tracing libraries. Blocks are saved in Datadog, automatically and securely fetched by the Datadog Agent, deployed in your infrastructure, and applied to your services. For details, read How Remote Configuration Works.
To start leveraging Protection capabilities—In-App WAF, IP blocking, User blocking and more—read Protection.
Further reading
Additional helpful documentation, links, and articles: