- Essentials
- Getting Started
- Datadog
- Datadog Site
- DevSecOps
- Serverless for AWS Lambda
- Agent
- Integrations
- Containers
- Dashboards
- Monitors
- Logs
- APM Tracing
- Profiler
- Tags
- API
- Service Catalog
- Session Replay
- Continuous Testing
- Synthetic Monitoring
- Incident Management
- Database Monitoring
- Cloud Security Management
- Cloud SIEM
- Application Security Management
- Workflow Automation
- CI Visibility
- Test Visibility
- Intelligent Test Runner
- Code Analysis
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- OpenTelemetry
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Recommended Monitor
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- Service Checks
- IDE Plugins
- Community
- Guides
- API
- Datadog Mobile App
- CoScreen
- Cloudcraft
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Sheets
- Monitors and Alerting
- Infrastructure
- Metrics
- Watchdog
- Bits AI
- Service Catalog
- API Catalog
- Error Tracking
- Service Management
- Infrastructure
- Application Performance
- APM
- Continuous Profiler
- Database Monitoring
- Data Streams Monitoring
- Data Jobs Monitoring
- Digital Experience
- Real User Monitoring
- Product Analytics
- Synthetic Testing and Monitoring
- Continuous Testing
- Software Delivery
- CI Visibility
- CD Visibility
- Test Visibility
- Intelligent Test Runner
- Code Analysis
- Quality Gates
- DORA Metrics
- Security
- Security Overview
- Cloud SIEM
- Cloud Security Management
- Application Security Management
- AI Observability
- Log Management
- Observability Pipelines
- Log Management
- Administration
Upcoming Changes to Security Notification Rules
This article outlines upcoming changes to how notification rules are configured. These changes mostly impact Cloud Security Management (CSM), and more specifically cloud configuration and infrastructure configuration signals.
Note that for the time being, the changes will only affect how you get notified after manually upgrading a notification rule, or after the final deprecation date is reached (early 2025).
Signals deprecation for CSM Misconfigurations
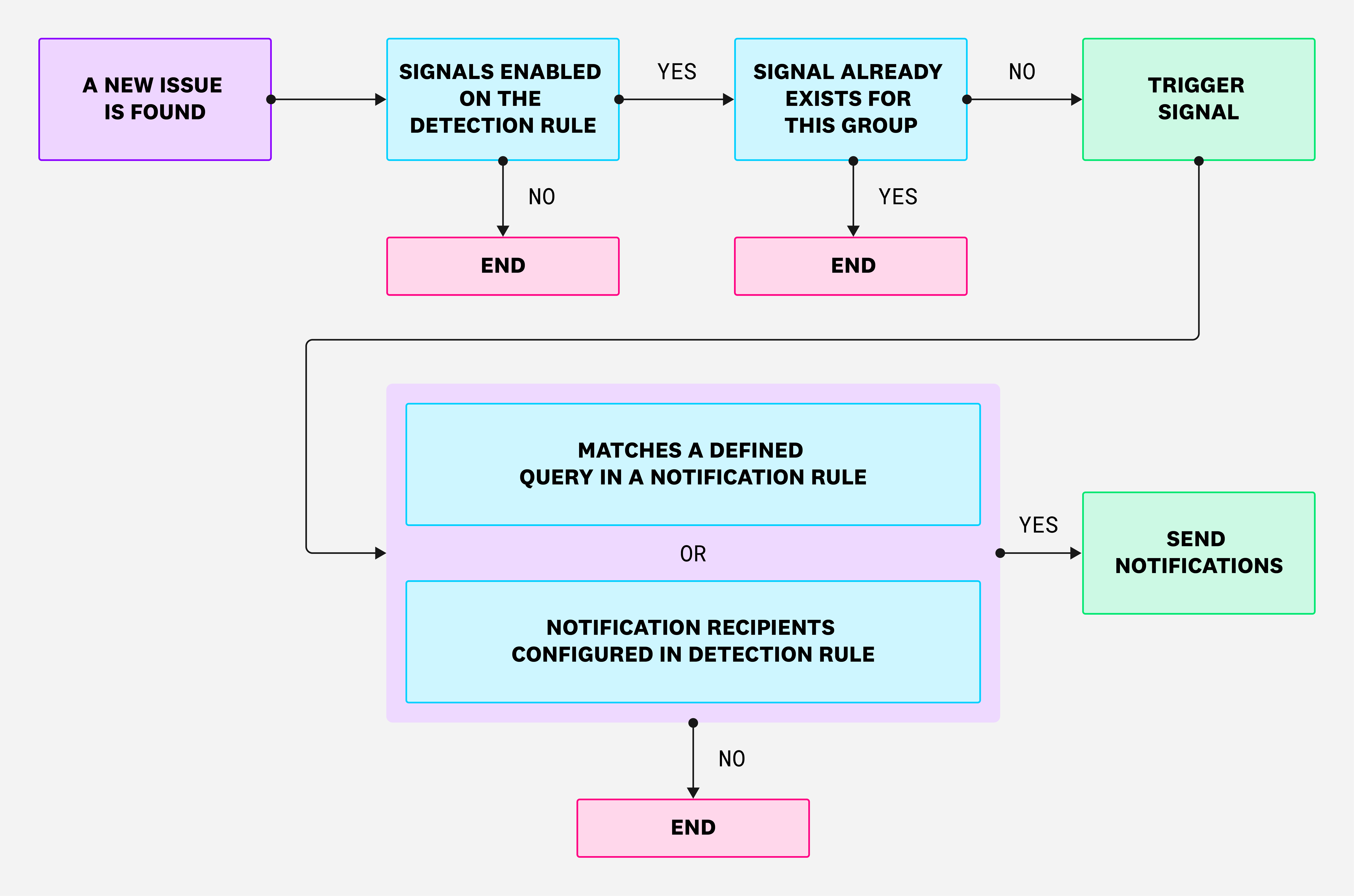
Until today, notifications for CSM Misconfigurations would only be sent out for detection rules that have signals enabled, as shown in the following diagram:
Previous workflow:
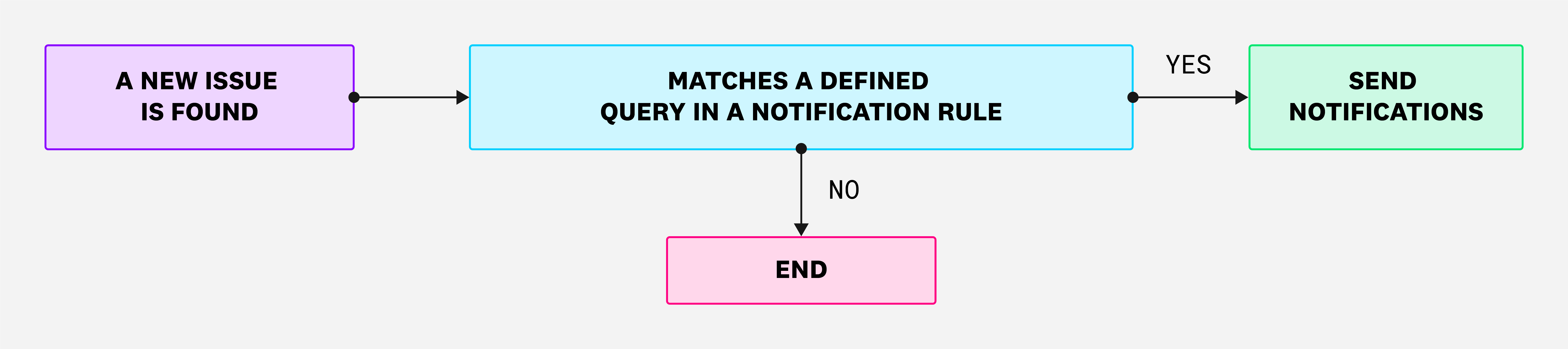
As part of the upcoming changes to notification rules, you are no longer required to enable signals in order to generate notifications. The new workflow is shown in the following diagram:
New workflow:
This change has the following impact on how notifications are generated for CSM Misconfigurations:
- You will now be able to specify misconfiguration as a source type when creating notification rules.
- You will now be able to choose whether you want to get notified for every new issue matching your query, or if you want to receive periodic notifications that summarize the new findings.
- Signals are no longer generated for CSM Misconfigurations. This also means that notifications can no longer be enabled and configured at the detection rule level.
- Support for CSM Misconfigurations signals will be deprecated in early 2025. Legacy signals will be retained for 15 months from their trigger date (free of charge).
While there will be no immediate change in behavior, depending on how you configure your new notification rules, you may notice an increase in the number of notifications generated. If the conditions set in a notification rule results in a high number of notifications, a warning message is displayed in the Preview of Matching Results panel. To help control noise, you can refine your query and use the new time aggregation mechanism. At this time, this feature is only available for vulnerabilities.
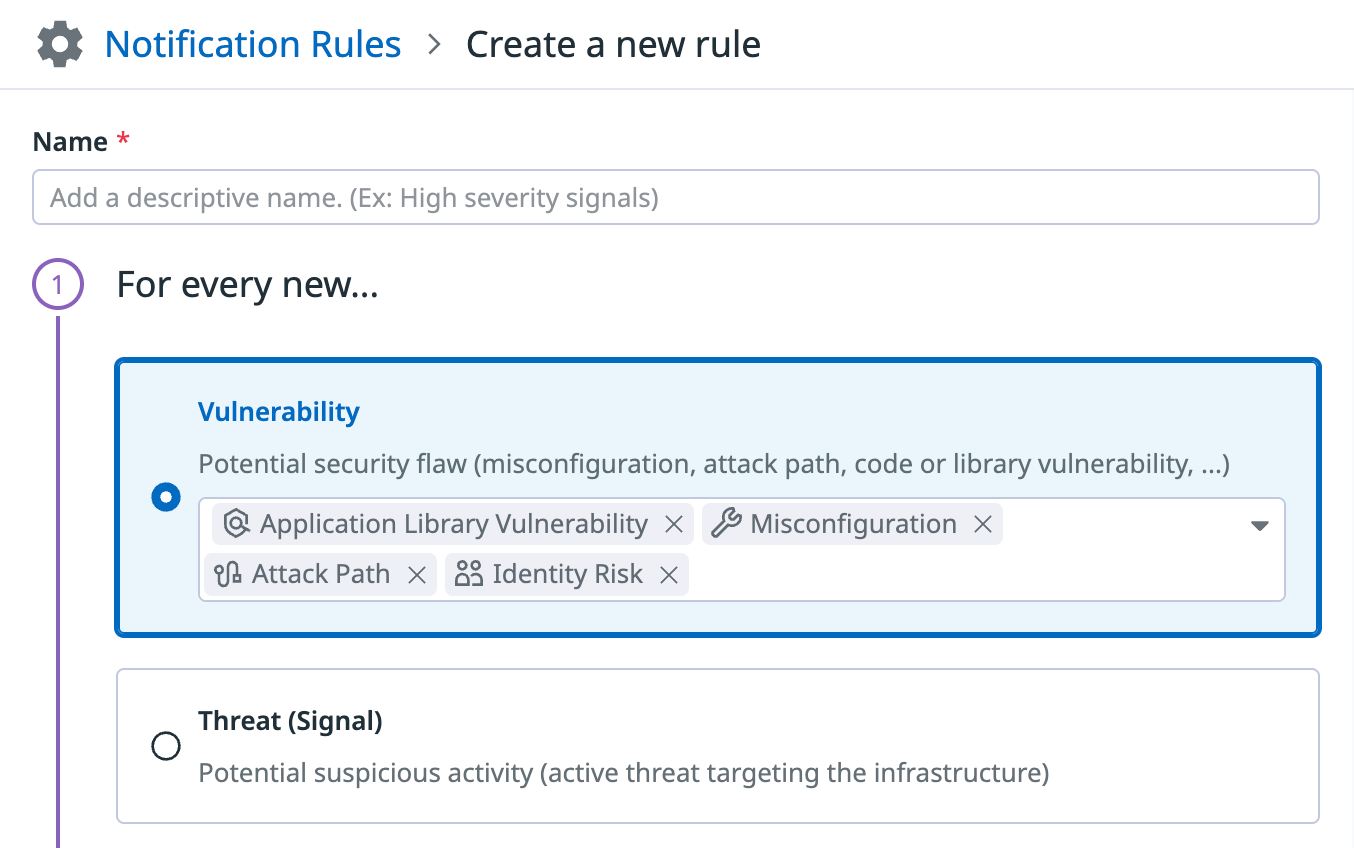
Notification rules source types selector
When you create a notification rule, you are now required to choose between two different source types: Vulnerability or Threat (Signal).
- A vulnerability represents a potential security flaw in your infrastructure.
- A threat (signal) represents suspicious activity that poses an active threat against your infrastructure.
Additional changes
- Notification rules can now be configured for identity risks and attack paths, as well as container image vulnerabilities.
- CSM Misconfigurations notifications now contain the full finding metadata. Previously, the notification contained only limited signal metadata.
- Terraformed custom detection rules using the legacy notifications attribute will no longer be supported after the final deprecation date (early 2025). Terraform support for Notification Rules will be available in late 2024.
How to migrate existing notifications
Detection rule notifications
To migrate notifications that are configured for individual detection rules:
On the Misconfiguration Rules page, select a detection rule that has notifications enabled for it.
In the banner displayed in the Set severity and notifications section, click Update in 1-Click.
The Notification Rules editor page is displayed with the fields pre-populated with the information from the rule.
Modify the settings, if desired.
Click Save and Activate.
Notification rules configured for cloud or infrastructure configuration signals
To migrate notification rules configured for cloud or infrastructure configuration signals, change the target from Cloud Configuration or Infrastructure Configuration to Vulnerability > Misconfiguration.
If you have any questions, contact Datadog support.
Further Reading
Additional helpful documentation, links, and articles: