- Principales informations
- Getting Started
- Datadog
- Site Datadog
- DevSecOps
- Serverless for AWS Lambda
- Agent
- Intégrations
- Conteneurs
- Dashboards
- Monitors
- Logs
- Tracing
- Profileur
- Tags
- API
- Service Catalog
- Session Replay
- Continuous Testing
- Surveillance Synthetic
- Incident Management
- Database Monitoring
- Cloud Security Management
- Cloud SIEM
- Application Security Management
- Workflow Automation
- CI Visibility
- Test Visibility
- Intelligent Test Runner
- Code Analysis
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Intégrations
- OpenTelemetry
- Développeurs
- Authorization
- DogStatsD
- Checks custom
- Intégrations
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Recommended Monitor
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- Checks de service
- IDE Plugins
- Communauté
- Guides
- API
- Application mobile
- CoScreen
- Cloudcraft
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Alertes
- Infrastructure
- Métriques
- Watchdog
- Bits AI
- Service Catalog
- API Catalog
- Error Tracking
- Service Management
- Infrastructure
- Universal Service Monitoring
- Conteneurs
- Sans serveur
- Surveillance réseau
- Cloud Cost
- Application Performance
- APM
- Profileur en continu
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Configuration de Postgres
- Configuration de MySQL
- Configuration de SQL Server
- Setting Up Oracle
- Setting Up MongoDB
- Connecting DBM and Traces
- Données collectées
- Exploring Database Hosts
- Explorer les métriques de requête
- Explorer des échantillons de requêtes
- Dépannage
- Guides
- Data Streams Monitoring
- Data Jobs Monitoring
- Digital Experience
- RUM et Session Replay
- Product Analytics
- Surveillance Synthetic
- Continuous Testing
- Software Delivery
- CI Visibility
- CD Visibility
- Test Visibility
- Exécuteur de tests intelligent
- Code Analysis
- Quality Gates
- DORA Metrics
- Securité
- Security Overview
- Cloud SIEM
- Cloud Security Management
- Application Security Management
- AI Observability
- Log Management
- Pipelines d'observabilité
- Log Management
- Administration
Multi-Factor Authentication (MFA)
Cette page n'est pas encore disponible en français, sa traduction est en cours.
Si vous avez des questions ou des retours sur notre projet de traduction actuel, n'hésitez pas à nous contacter.
Si vous avez des questions ou des retours sur notre projet de traduction actuel, n'hésitez pas à nous contacter.
Overview
Multi-Factor Authentication (MFA), or Two-Factor Authentication (2FA) requires a user to present more than one type of verification to authenticate to a system. MFA defends against the majority of password-related attacks, including brute-force, credential stuffing, and password spraying.
Capabilities
- MFA for native Datadog accounts: MFA is available as an extra layer of security during login for accounts that log into Datadog directly using an email and password. Native email/password accounts are more vulnerable to attack than accounts maintained through an identity provider.
- Opt-in MFA: MFA is available for end users as an optional feature. Enable MFA at any time through your personal settings.
- Authenticator apps: Any authenticator app that supports time-based one-time password (TOTP) authentication can be used for MFA. Examples include Microsoft Authenticator, Google Authenticator, Authy, and Duo.
Limitations
- MFA is not available for accounts using Single Sign-On (SSO) only. To use MFA with SAML and Google Auth, configure it through your Identity Provider (IdP).
- MFA does not protect against all types of attacks. For example, if an attacker has access to your email, they may be able to turn off MFA and compromise your account.
- MFA supports at most one authenticator app.
Prerequisites
To configure MFA for your account, log in using your email and password. Users who log in using SSO do not see MFA configuration options.
Configure MFA for your user account
To find the Password & Authentication page:
- Ensure you are logged in with a username and password combination, not through SSO.
- Navigate to Personal Settings from your account menu.
- Under Security, select Password & Authentication.
The multi-factor authentication section lists any configured authenticator apps.
- Next to Authenticator App, select Add.
- Follow your authenticator app’s documentation for instructions on adding a new QR code.
- Enter the latest code generated by your authenticator app into the prompt to confirm the device was set up correctly.
- Save a copy of the recovery codes in a secure location. The codes cannot be retrieved after setup is complete.
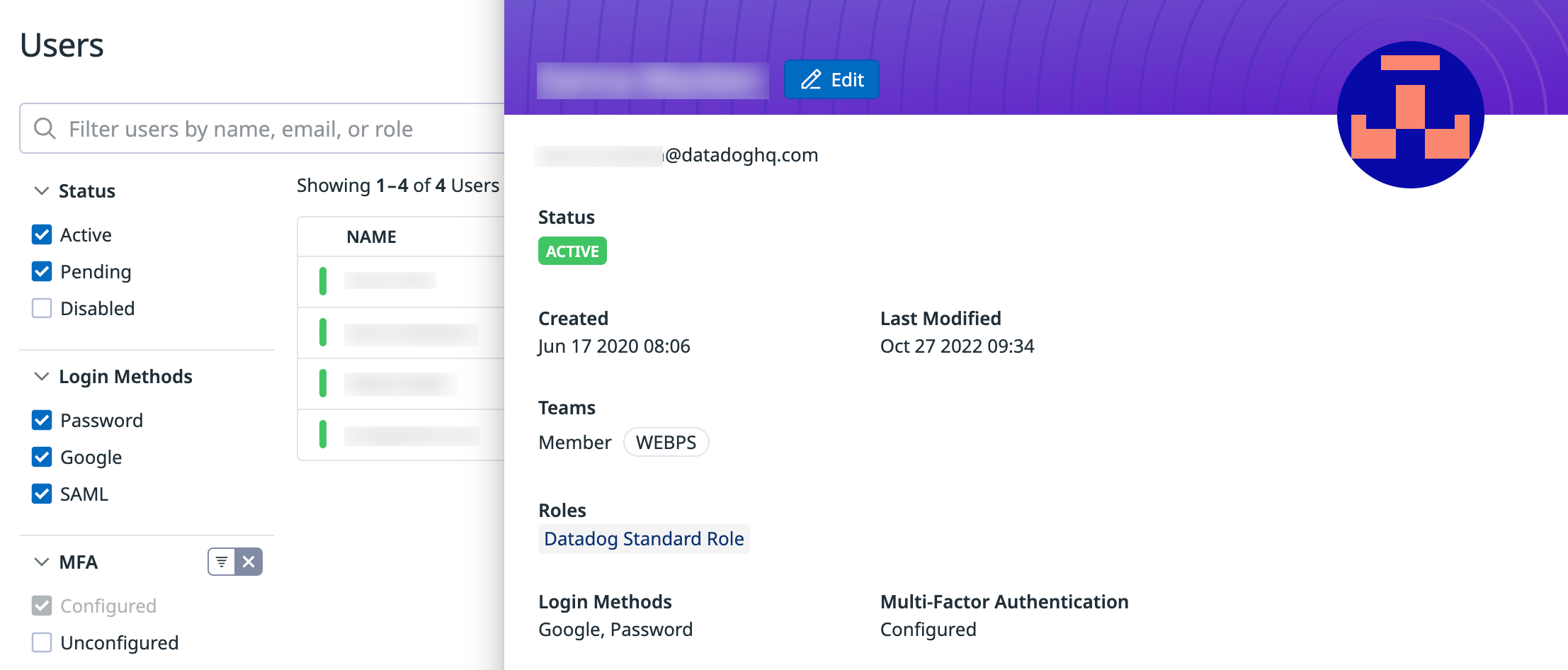
View a user’s MFA status
To view if a user has MFA configured or not, you can filter on the Users table. The MFA status is also available on the user details panel.
MFA recovery
If you don’t have access to your authenticator app, during the login process you can use a recovery code instead of a one-time password. Each of the recovery codes can only be used once.
- Navigate to the login page.
- Enter your email address and password, then select Log in.
- Select Don’t have access to your authenticator?
- Enter one of your unused recovery codes and click Verify.
MFA rescue
If you don’t have access to your authenticator app or recovery codes, during the login process you can request a one-time recovery link via email.
- Navigate to the login page.
- Enter your email address and password, then select Log in.
- Select Don’t have access to your authenticator?
- Select Don’t have access to your recovery codes? Get a one time recovery link via email.
- Check your email inbox for a message with the subject line “Recovery link for logging into your Datadog account.”
- Select the Log in to Datadog link to finish logging into your account.
If you have lost access to your registered authenticator app, Datadog recommends that you remove the lost device and add a new one. Maintaining a valid authenticator app helps prevent issues logging into your account in the future.