- Principales informations
- Getting Started
- Datadog
- Site Datadog
- DevSecOps
- Serverless for AWS Lambda
- Agent
- Intégrations
- Conteneurs
- Dashboards
- Monitors
- Logs
- Tracing
- Profileur
- Tags
- API
- Service Catalog
- Session Replay
- Continuous Testing
- Surveillance Synthetic
- Incident Management
- Database Monitoring
- Cloud Security Management
- Cloud SIEM
- Application Security Management
- Workflow Automation
- CI Visibility
- Test Visibility
- Intelligent Test Runner
- Code Analysis
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Intégrations
- OpenTelemetry
- Développeurs
- Authorization
- DogStatsD
- Checks custom
- Intégrations
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Recommended Monitor
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- Checks de service
- IDE Plugins
- Communauté
- Guides
- Administrator's Guide
- API
- Application mobile
- CoScreen
- Cloudcraft
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Alertes
- Infrastructure
- Métriques
- Watchdog
- Bits AI
- Service Catalog
- API Catalog
- Error Tracking
- Service Management
- Infrastructure
- Universal Service Monitoring
- Conteneurs
- Sans serveur
- Surveillance réseau
- Cloud Cost
- Application Performance
- APM
- Profileur en continu
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Configuration de Postgres
- Configuration de MySQL
- Configuration de SQL Server
- Setting Up Oracle
- Setting Up MongoDB
- Connecting DBM and Traces
- Données collectées
- Exploring Database Hosts
- Explorer les métriques de requête
- Explorer des échantillons de requêtes
- Dépannage
- Guides
- Data Streams Monitoring
- Data Jobs Monitoring
- Digital Experience
- RUM et Session Replay
- Product Analytics
- Surveillance Synthetic
- Continuous Testing
- Software Delivery
- CI Visibility
- CD Visibility
- Test Visibility
- Exécuteur de tests intelligent
- Code Analysis
- Quality Gates
- DORA Metrics
- Securité
- Security Overview
- Cloud SIEM
- Cloud Security Management
- Application Security Management
- AI Observability
- Log Management
- Pipelines d'observabilité
- Log Management
- Administration
NetFlow Monitoring
Cette page n'est pas encore disponible en français, sa traduction est en cours.
Si vous avez des questions ou des retours sur notre projet de traduction actuel, n'hésitez pas à nous contacter.
Si vous avez des questions ou des retours sur notre projet de traduction actuel, n'hésitez pas à nous contacter.
Overview
Use NetFlow Monitoring in Datadog to visualize and monitor your flow records from your NetFlow-enabled devices.
Installation
To use NetFlow Monitoring with Network Device Monitoring, ensure you are using the Agent version 7.45 or newer.
Note: Configuring metric collection from Network Device Monitoring is not a requirement for sending NetFlow data, although it is strongly recommended as this extra data can be used to enrich your flow records with information such as the device name, model, and vendor, as well as the inbound/outbound interface name.
Configuration
To configure your devices to send NetFlow, jFlow, sFlow, or IPFIX traffic to the Agent NetFlow server, your devices must be configured to send traffic to the IP address that the Datadog Agent is installed on, specifically the flow_type and port.
Edit your datadog.yaml Agent configuration file to enable NetFlow:
network_devices:
netflow:
enabled: true
listeners:
- flow_type: netflow9 # choices: netflow5, netflow9, ipfix, sflow5
port: 2055 # devices need to be configured to the same port number
- flow_type: netflow5
port: 2056
- flow_type: ipfix
port: 4739
- flow_type: sflow5
port: 6343
## Set to true to enable reverse DNS enrichment of private source and destination IP addresses in NetFlow records
reverse_dns_enrichment_enabled: false
After saving your changes, restart the Agent.
Aggregation
The Datadog Agent automatically aggregates the data received into NetFlow to limit the number of records sent to the platform while maintaining most of the information. By default, flow recordings that have the same identifiers, such as source, destination address, port, and protocol, are aggregated together in five minute intervals. Additionally, the Datadog Agent can detect ephemeral ports and remove them. As a result, you may see Flows with port:*.
Enrichment
Your NetFlow data is processed by the Datadog backend and enriched with the available metadata from your devices and interfaces. Enrichment is based on the NetFlow exporter IP and the interface indexes. To disambiguate possible collisions between reused private IPs, you can configure a different namespace for each Agent configuration file (with the setting network_devices.namespace).
If the NetFlow exporter IP is one of the device IPs, but not the one configured on the SNMP integration, Datadog attempts to locate the device that the exporter IP belongs to, and enriches your NetFlow data with it is as long as the match is unique.
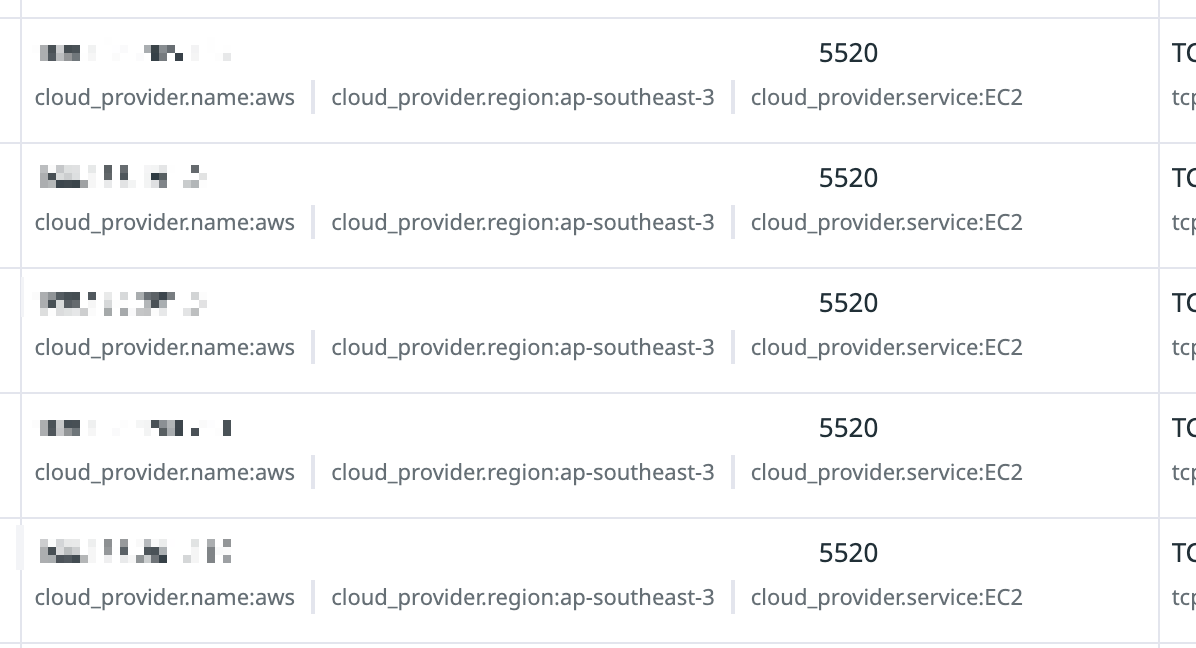
Cloud provider IP enrichment
Datadog enriches IPs with public cloud provider service and region for IPv4 addresses, so you can filter for flow records from a specific service and region.
Port enrichment
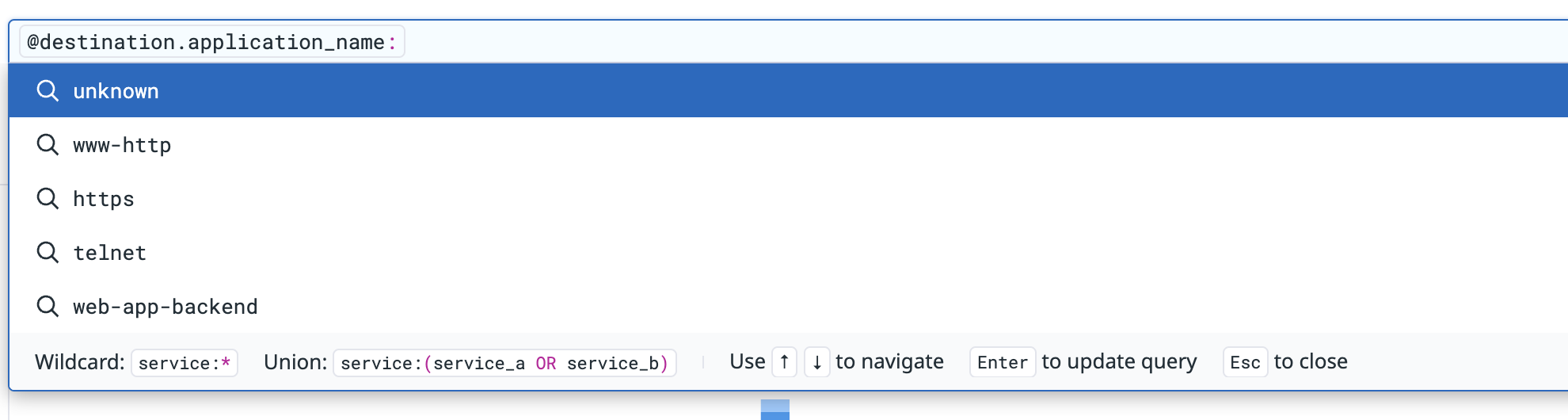
Datadog enriches ports in NetFlow with IANA (Internet Assigned Numbers Authority) data to resolve well known port mappings (such as Postgres on 5432 and HTTPS on 443). This can be seen when searching for source or destination application names on NetFlow.
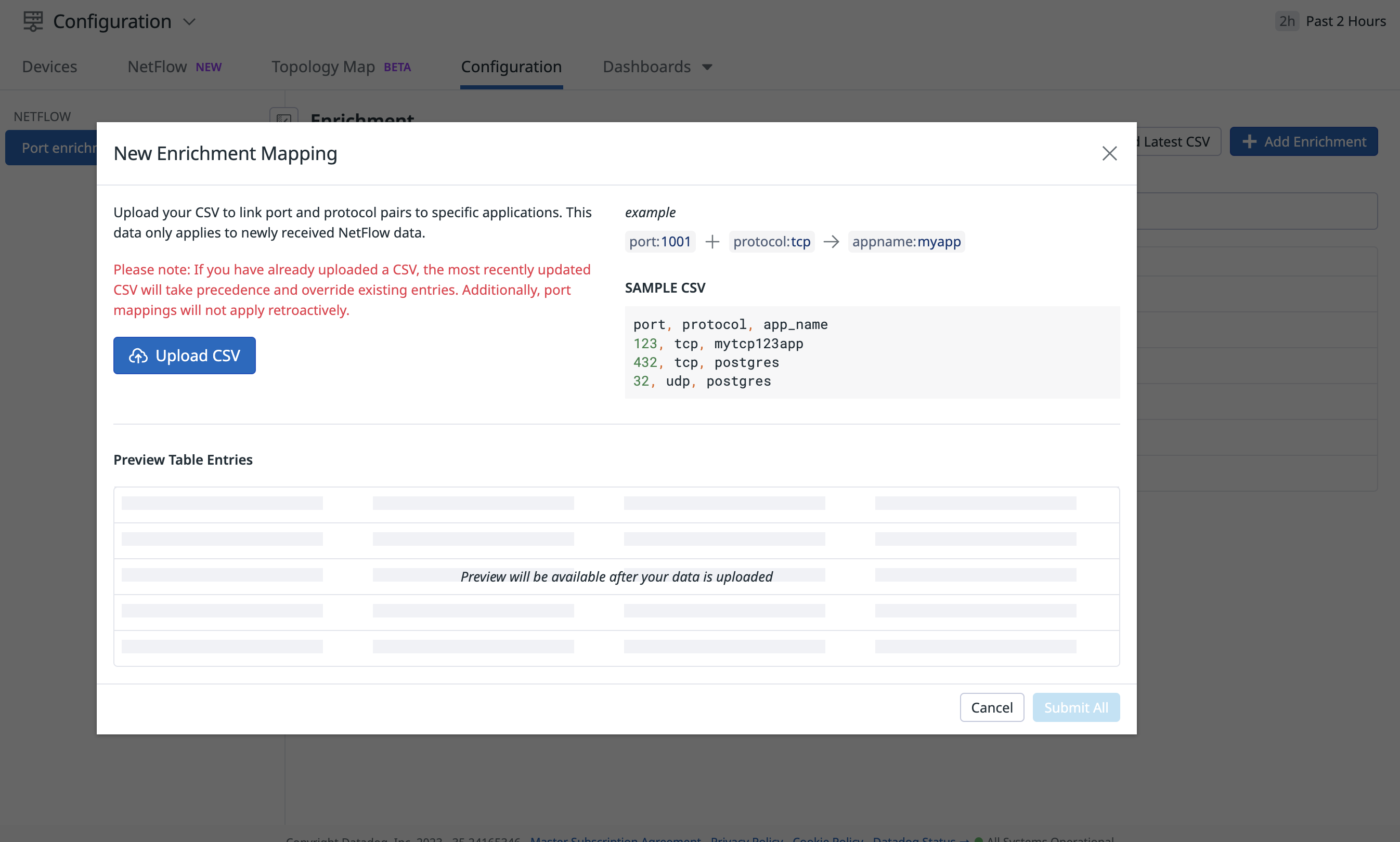
Custom port enrichment
You can also add your own custom enrichments to map ports and protocols to specific applications (for example, if a custom service runs on a specific port). This makes it easier for network engineers and their teams to interpret and query NetFlow data with human-readable names.
From the Configuration tab in NetFlow, click Add Enrichment to upload the CSV file containing your custom enrichments.
Reverse DNS private IP enrichment
Enable Reverse DNS private IP enrichment to perform DNS lookups for hostnames associated with source or destination IP addresses. When enabled, the Agent conducts reverse DNS lookups on source and destination IPs within private address ranges, enriching NetFlow records with the corresponding hostnames.
By default, the Reverse DNS IP enrichment in your datadog.yaml file is disabled. To enable, see the Configuration section of this page.
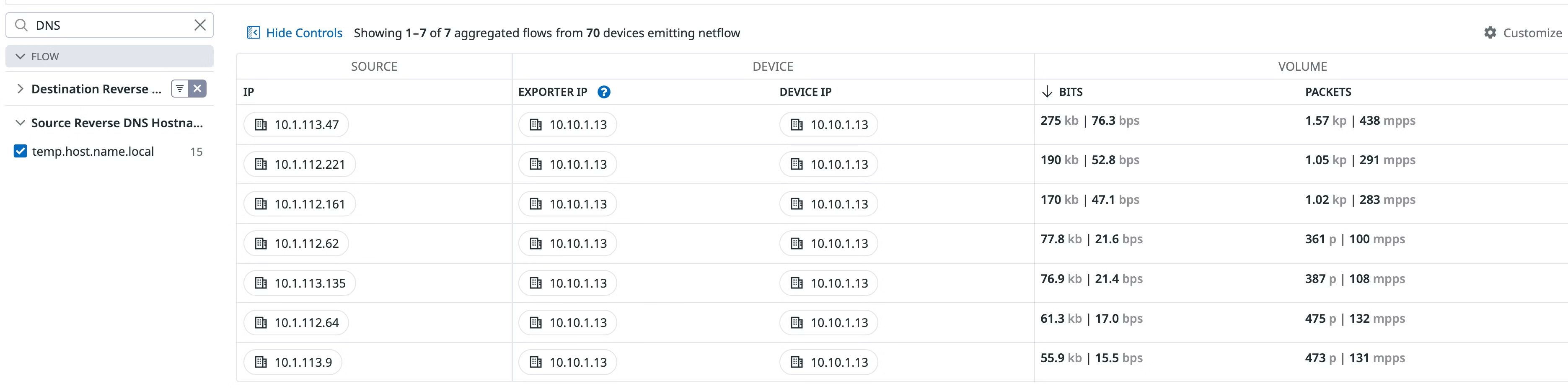
Search for DNS in the Flow grouping of the facets section to locate flows associated with Reverse DNS IP enrichment:
Note: Reverse DNS entries are cached and subject to rate limiting to minimize DNS queries and reduce the load on DNS servers. For more configuration options, including modifying default caching and rate limiting, see the full configuration file.
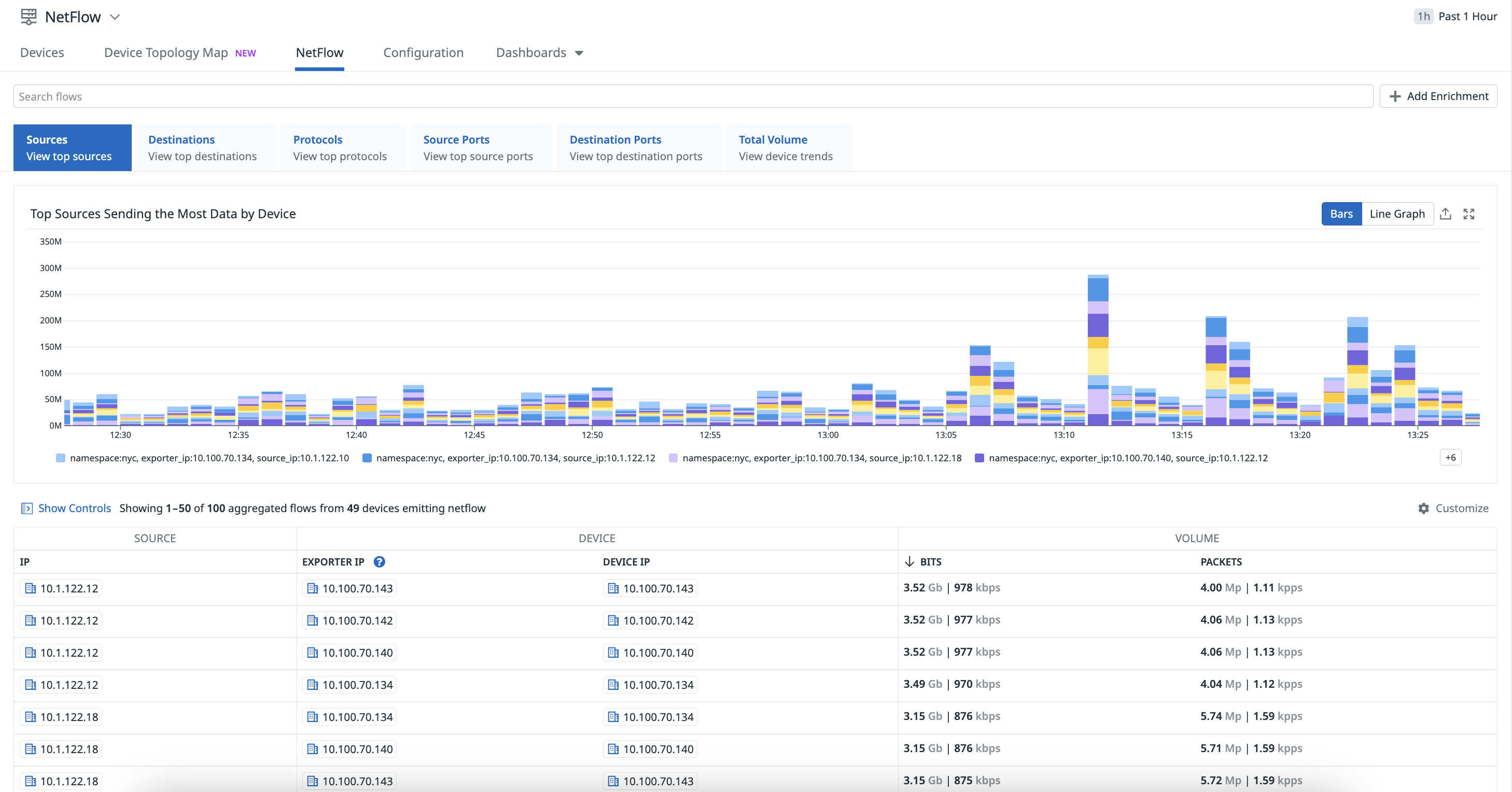
Visualization
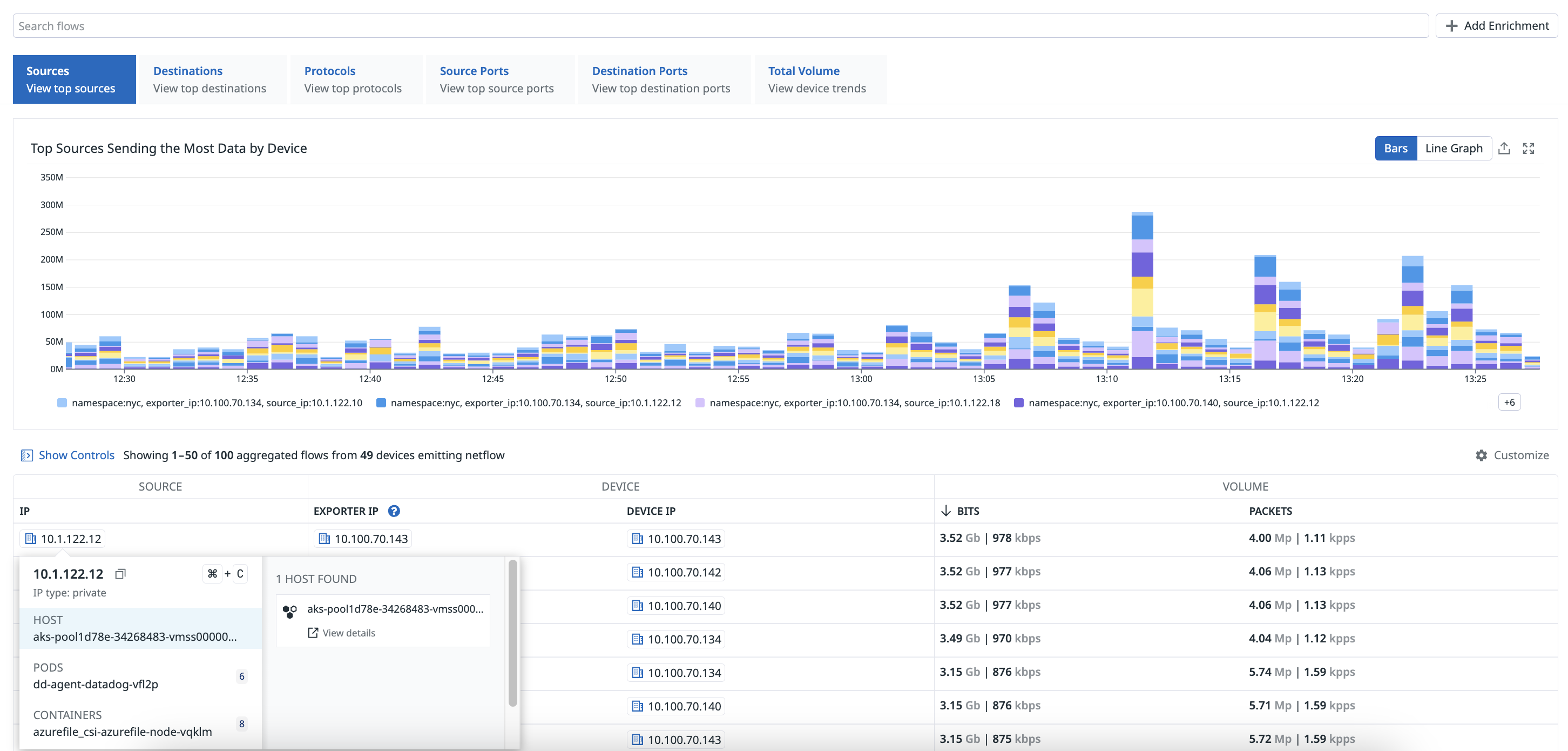
You can access the data collected by NetFlow Monitoring on the NetFlow page. Hover over a flow from the list for additional information about hosts, pods, and containers, and access related network connections.
When creating a NetFlow monitor, you should consider the following fields with respect to the source IP or destination IP from the perspective of the device. These fields provide insights into network traffic patterns and help with optimizing performance and security.
Interface information
The following fields represent details about the ingress and egress interfaces.
| Field Name | Field Description |
|---|---|
| Egress Interface Alias | Alias of the egress interface. |
| Egress Interface Index | Index of the egress interface. |
| Egress Interface Name | Name of the egress interface. |
| Ingress Interface Alias | Alias of the ingress interface. |
| Ingress Interface Index | Index of the ingress interface. |
| Ingress Interface Name | Name of the ingress interface. |
Device information
The following fields represent details related to the device generating NetFlow records.
| Field Name | Field Description |
|---|---|
| Device IP | IP address used to map to a device in NDM for enrichment purposes. |
| Exporter IP | IP address from which NetFlow packets originate. |
| Device Model | Model of the device. |
| Device Name | Name of the device. |
| Device Namespace | Namespace of the device. |
| Device Vendor | Vendor of the device. |
Flow details
The following fields represent characteristics of the network flow.
| Field Name | Field Description |
|---|---|
| Direction | Indicates whether the flow is inbound or outbound. |
| Start Time | Timestamp of the first network packet between the source and destination IP addresses. |
| End Time | Timestamp of the last network packet between the source and destination IP addresses. |
| Ether Type | Type of Ethernet frame encapsulation (IPv4 or IPv6). |
| Flow Type | Type of NetFlow data format (IPFIX, sFlow5, NetFlow5, NetFlow9, or Unknown). |
| IP Protocol | Protocol used for communication (such as ICMP, TCP, or UDP). |
| Next Hop IP | IP address of the next hop in the network path. |
| TCP Flag | Union of all TCP flags observed over the life of the flow. |
| Bytes | Total number of bytes transferred. |
| Packets | Total number of packets transferred. |
In addition to fields, you can also use out-of-the-box facets to start analyzing traffic patterns based on NetFlow destination and source IP addresses.
NetFlow Destination IP facets
| Facet Name | Facet Description |
|---|---|
| Destination AS Domain | The domain associated with the Autonomous System (AS) to which the destination IP belongs. |
| Destination AS Name | The name of the Autonomous System (AS) to which the destination IP belongs. |
| Destination AS Number | The number assigned to the Autonomous System (AS) to which the destination IP belongs. |
| Destination AS Route | The route information associated with the Autonomous System (AS) to which the destination IP belongs. |
| Destination AS Type | The type of Autonomous System (AS) to which the destination IP belongs (such as transit, customer, peer). |
| Destination Application Name | The name of the application associated with the destination IP. |
| Destination City Name | The name of the city associated with the destination IP. |
| Destination Cloud Provider Name | The name of the cloud provider associated with the destination IP. |
| Destination Cloud Provider Region | The region of the cloud provider associated with the destination IP. |
| Destination Cloud Provider Service | The service provided by the cloud provider associated with the destination IP. |
| Destination Continent Code | The code representing the continent associated with the destination IP. |
| Destination Continent Name | The name of the continent associated with the destination IP. |
| Destination Country ISO Code | The ISO code representing the country associated with the destination IP. |
| Destination Country Name | The name of the country associated with the destination IP. |
| Destination IP | The destination IP address. |
| Destination Latitude | The latitude coordinate associated with the destination IP. |
| Destination Longitude | The longitude coordinate associated with the destination IP. |
| Destination MAC | The Media Access Control (MAC) address associated with the destination IP. |
| Destination Mask | The subnet mask associated with the destination IP. |
| Destination Port | The destination port number. |
| Destination Reverse DNS Hostname | The DNS hostname associated with the destination IP. |
| Destination Subdivision ISO Code | The ISO code representing the subdivision (such as state or province) associated with the destination IP. |
| Destination Subdivision Name | The name of the subdivision (such as state or province) associated with the destination IP. |
| Destination Timezone | The timezone associated with the destination IP. |
NetFlow Source IP facets
| Facet Name | Facet Description |
|---|---|
| Source AS Domain | The domain associated with the Autonomous System (AS) to which the source IP belongs. |
| Source AS Name | The name of the Autonomous System (AS) to which the source IP belongs. |
| Source AS Number | The number assigned to the Autonomous System (AS) to which the source IP belongs. |
| Source AS Route | The route information associated with the Autonomous System (AS) to which the source IP belongs. |
| Source AS Type | The type of Autonomous System (AS) to which the source IP belongs (such as transit, customer, peer). |
| Source Application Name | The name of the application associated with the source IP. |
| Source City Name | The name of the city associated with the source IP. |
| Source Cloud Provider Name | The name of the cloud provider associated with the source IP. |
| Source Cloud Provider Region | The region of the cloud provider associated with the source IP. |
| Source Cloud Provider Service | The service provided by the cloud provider associated with the source IP. |
| Source Continent Code | The code representing the continent associated with the source IP. |
| Source Continent Name | The name of the continent associated with the source IP. |
| Source Country ISO Code | The ISO code representing the country associated with the source IP. |
| Source Country Name | The name of the country associated with the source IP. |
| Source IP | The source IP address. |
| Source Latitude | The latitude coordinate associated with the source IP. |
| Source Longitude | The longitude coordinate associated with the source IP. |
| Source MAC | The Media Access Control (MAC) address associated with the source IP. |
| Source Mask | The subnet mask associated with the source IP. |
| Source Port | The source port number. |
| Source Reverse DNS Hostname | The DNS hostname associated with the source IP. |
| Source Subdivision ISO Code | The ISO code representing the subdivision (such as state or province) associated with the source IP. |
| Source Subdivision Name | The name of the subdivision (such as state or province) associated with the source IP. |
| Source Timezone | The timezone associated with the source IP. |
By monitoring these key fields and using facets to analyze NetFlow events, organizations can gain visibility into their network infrastructure, optimize performance, and improve security posture.
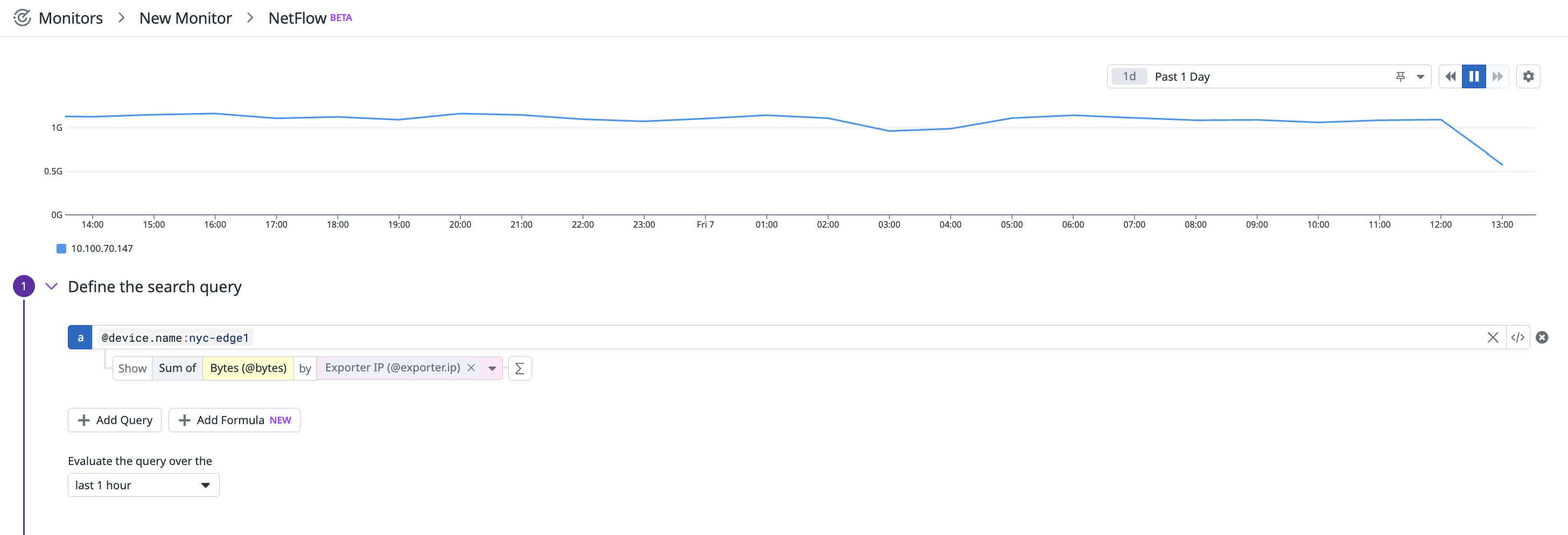
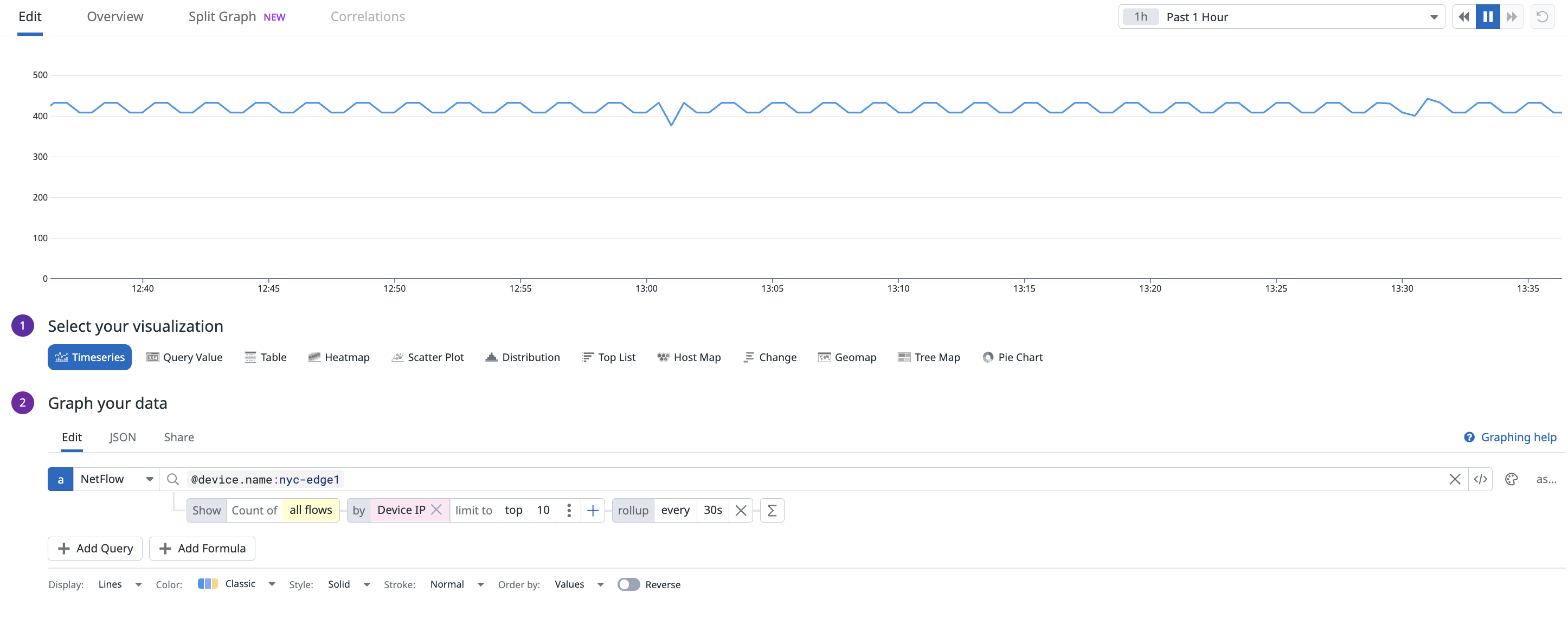
This data is also available in dashboards and notebooks, enabling precise queries and correlation with other data sources. When creating a dashboard with NetFlow data, select NetFlow as the source in the Graph your data section.
Sampling rate
NetFlow’s sampling rate is taken into account in the computation of bytes and packets by default. The displayed values for bytes and packets are computed with the sampling rate applied. Additionally, you can query for Bytes (Adjusted) (@adjusted_bytes) and Packets (Adjusted) (@adjusted_packets) in dashboards and notebooks to visualize them.
To visualize the raw bytes/packets (sampled) sent by your devices, you can query for Bytes (Sampled) (@bytes) and Packets (Sampled) (@packets) in dashboards and notebooks.
Retention
NetFlow data is retained for 30 days by default, with options for 15, 30, 60, and 90 day retention.
To retain NetFlow data for longer periods of time, contact your account representative.
Troubleshooting
NetFlow packet drops
NetFlow packet drops can occur when there are a high number of NetFlow packets per second, typically greater than 50,000. The following steps can help identify and mitigate NetFlow packet drops:
Identifying packet drops
Use the netstat -s command to see if there are any dropped UDP packets:
netstat -s
Mitigation steps
- Increase the Number of NetFlow Listeners
Increase the number of NetFlow listeners by using a configuration similar to the following: Datadog recommends setting the number of workers to match the number of CPU cores in your system:
netflow:
enabled: true
listeners:
- flow_type: netflow9
port: 2055
workers: 4 # 4 CPUs
- Increase UDP Queue Length (Linux only)
Adjusting your system’s UDP queue length can help accommodate the higher volume of NetFlow packets. Increase the UDP receive buffer size to 25MB by executing the following commands:
sudo sysctl -w net.core.rmem_max=26214400
sudo sysctl -w net.core.rmem_default=26214400
- Persisting the configuration (Linux only)
To make these changes permanent, add the following lines to your /etc/sysctl.conf file:
net.core.rmem_max=26214400
net.core.rmem_default=26214400
Further Reading
Documentation, liens et articles supplémentaires utiles: