- Essentials
- Getting Started
- Datadog
- Datadog Site
- DevSecOps
- Serverless for AWS Lambda
- Agent
- Integrations
- Containers
- Dashboards
- Monitors
- Logs
- APM Tracing
- Profiler
- Tags
- API
- Service Catalog
- Session Replay
- Continuous Testing
- Synthetic Monitoring
- Incident Management
- Database Monitoring
- Cloud Security Management
- Cloud SIEM
- Application Security Management
- Workflow Automation
- CI Visibility
- Test Visibility
- Intelligent Test Runner
- Code Analysis
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- OpenTelemetry
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Recommended Monitor
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- Service Checks
- IDE Plugins
- Community
- Guides
- API
- Datadog Mobile App
- CoScreen
- Cloudcraft
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Sheets
- Monitors and Alerting
- Infrastructure
- Metrics
- Watchdog
- Bits AI
- Service Catalog
- API Catalog
- Error Tracking
- Service Management
- Infrastructure
- Application Performance
- APM
- Continuous Profiler
- Database Monitoring
- Data Streams Monitoring
- Data Jobs Monitoring
- Digital Experience
- Real User Monitoring
- Product Analytics
- Synthetic Testing and Monitoring
- Continuous Testing
- Software Delivery
- CI Visibility
- CD Visibility
- Test Visibility
- Intelligent Test Runner
- Code Analysis
- Quality Gates
- DORA Metrics
- Security
- Security Overview
- Cloud SIEM
- Cloud Security Management
- Application Security Management
- AI Observability
- Log Management
- Observability Pipelines
- Log Management
- Administration
Setting file permissions for rotating logs (Linux)
The Datadog Agent runs under the dd-agent user and dd-agent group. This prevents the Datadog Agent from accessing the logs in /var/log as they are only accessible by root (or a sudo admin).
Setting permissions using ACLs
In order to allow read-only access for datadog-agent only, create ACLs and modify logrotate to persist the permissions changes.
Verifying ACLs are enabled on your system
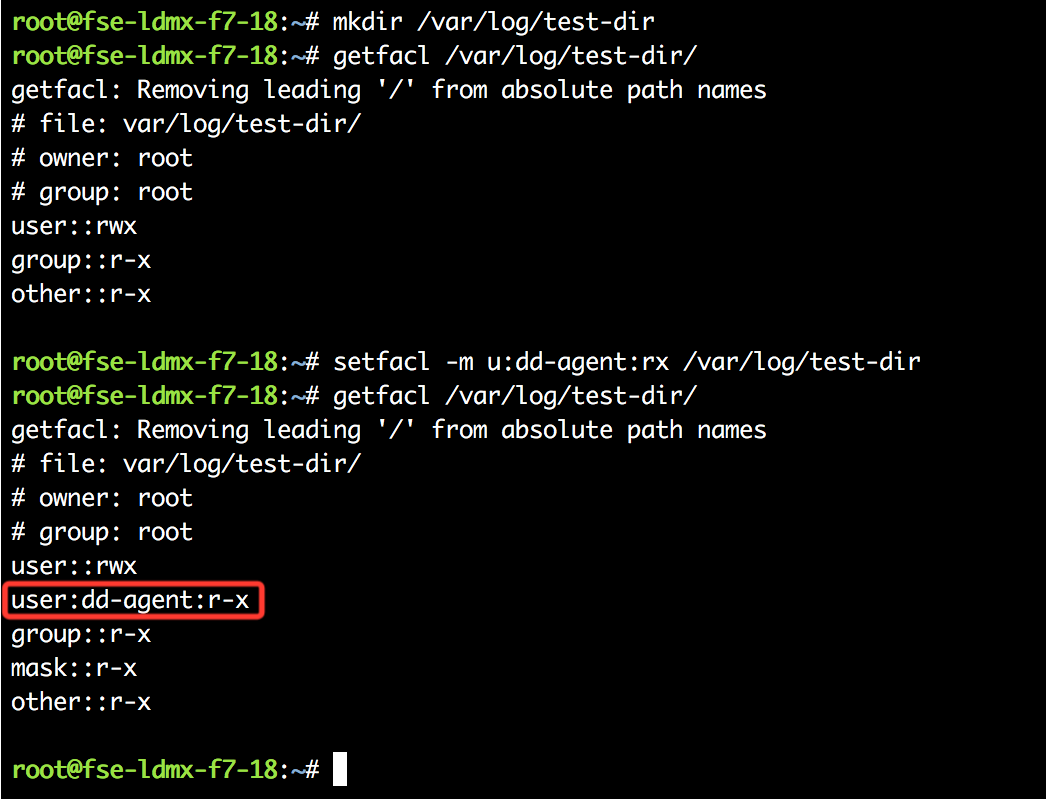
ACLs needs to be enabled on your file system to set permissions using the methods outlined in this article. Verify ACLs are enabled by using thegetfacl and setfacl commands to set permissions for the datadog-agent user on a test directory, for example:
mkdir /var/log/test-dir
getfacl /var/log/test-dir/
setfacl -m u:dd-agent:rx /var/log/test-dir
getfacl /var/log/test-dir/
The permissions set for datadog-agent appears in the output of getfacl if ACLs are enabled.
Granting dd-agent read and execute permissions on log directories
Once you have verified ACLs are enabled, grant read and execute permissions for the datadog-agent user on the appropriate directories for log collection. For example, to grant access to /var/log/apache , run:
setfacl -m u:dd-agent:rx /var/log/apache
Learn more about how to configure ACLs on linux
Setting permissions for log file rotation
Setting the permissions once will not persist for rotating logs, as logrotate does not re-apply the ACL setting. For a more permanent solution add a rule to logrotate to reset the ACL in a new file:
sudo touch /etc/logrotate.d/dd-agent_ACLs
Example file:
/var/log/apache/*.log {
postrotate
/usr/bin/setfacl -m g:dd-agent:rx /var/log/apache/access.log
/usr/bin/setfacl -m g:dd-agent:rx /var/log/apache/error.log
endscript
}
Check the ACL status of a file with:
getfacl /var/log/apache/access.log
Note: For PostgreSQL v10 and older, set the permission to 0700. For PostgreSQL v11, set either 0700 or 0750. Trying to start a server with a base data folder that has permissions different from 0700 or 0750 will result in a failure of the postmater process.
Note: The PostgreSQL logging directory cannot be located in the same directory as the base PostgreSQL installation.
Setting permissions when ACLs are not present
When ACLs are not present in a system, set your permissions based on group access.
For instance, if your MySQL service is logging to the following locations:
/var/log/mysql/mysql_error.log
/var/log/mysql/mysql-slow.log
Their permissions are associated with user ‘mysql’ and the group ‘mysql’ by default. This logging scheme denies access to the log file to any user not in the ‘mysql’ group. Typically you may see something like this:
$ ls -l /var/log | grep -i mysql
drwxr-x--- 2 mysql mysql 4096 Feb 20 06:25 mysql
The easiest path here is to give everyone read access to the file in the logrotate configuration:
/var/log/mysql/mysql_error.log /var/log/mysql/mysql-slow.log {
daily
rotate 7
missingok
create 644 mysql adm
compress
}
Each common off-the-shelf application will follow a similar nomenclature. The advantage is that you avoid providing privileged access to an individual account and use a standardized practice. This keeps your audit rules in check.
Further Reading
Additional helpful documentation, links, and articles: