- Principales informations
- Getting Started
- Datadog
- Site Datadog
- DevSecOps
- Serverless for AWS Lambda
- Agent
- Intégrations
- Conteneurs
- Dashboards
- Monitors
- Logs
- Tracing
- Profileur
- Tags
- API
- Service Catalog
- Session Replay
- Continuous Testing
- Surveillance Synthetic
- Incident Management
- Database Monitoring
- Cloud Security Management
- Cloud SIEM
- Application Security Management
- Workflow Automation
- CI Visibility
- Test Visibility
- Intelligent Test Runner
- Code Analysis
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Intégrations
- OpenTelemetry
- Développeurs
- Authorization
- DogStatsD
- Checks custom
- Intégrations
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Recommended Monitor
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- Checks de service
- IDE Plugins
- Communauté
- Guides
- API
- Application mobile
- CoScreen
- Cloudcraft
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Alertes
- Infrastructure
- Métriques
- Watchdog
- Bits AI
- Service Catalog
- API Catalog
- Error Tracking
- Service Management
- Infrastructure
- Universal Service Monitoring
- Conteneurs
- Sans serveur
- Surveillance réseau
- Cloud Cost
- Application Performance
- APM
- Profileur en continu
- Database Monitoring
- Agent Integration Overhead
- Setup Architectures
- Configuration de Postgres
- Configuration de MySQL
- Configuration de SQL Server
- Setting Up Oracle
- Setting Up MongoDB
- Connecting DBM and Traces
- Données collectées
- Exploring Database Hosts
- Explorer les métriques de requête
- Explorer des échantillons de requêtes
- Dépannage
- Guides
- Data Streams Monitoring
- Data Jobs Monitoring
- Digital Experience
- RUM et Session Replay
- Product Analytics
- Surveillance Synthetic
- Continuous Testing
- Software Delivery
- CI Visibility
- CD Visibility
- Test Visibility
- Exécuteur de tests intelligent
- Code Analysis
- Quality Gates
- DORA Metrics
- Securité
- Security Overview
- Cloud SIEM
- Cloud Security Management
- Application Security Management
- AI Observability
- Log Management
- Pipelines d'observabilité
- Log Management
- Administration
Advanced Search
Cette page n'est pas encore disponible en français, sa traduction est en cours.
Si vous avez des questions ou des retours sur notre projet de traduction actuel, n'hésitez pas à nous contacter.
Si vous avez des questions ou des retours sur notre projet de traduction actuel, n'hésitez pas à nous contacter.
Overview
When you need to further refine the results of a log search, use subqueries to compare your results against a secondary group of logs, or filter your logs using data from your Reference Tables.
Filter logs with subqueries
Filtering logs with subqueries is in beta.
Use subqueries when you want to filter the results of a query based on the results of a secondary query. See subquery examples for two example scenarios.
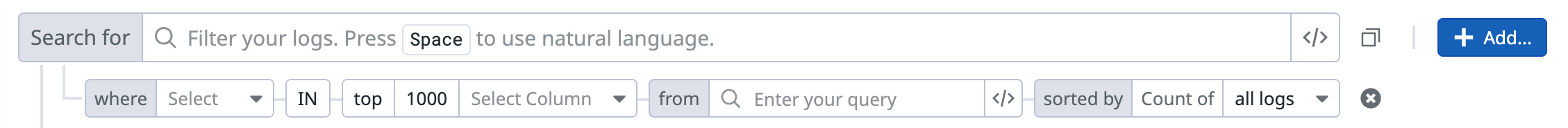
To add a subquery filter:
- Navigate to Log Explorer.
- Enter a query in the search bar to filter your logs. This is the main query.
- Click + Add.
- Under the Add Query Filter section, select Logs.
This introduces new elements to the query editor:
- In the where field, use the dropdown menu to select the attribute you want to correlate on. The available attributes are from the logs returned by your main query.
- Define your subquery filter in the from field.
- In the Select Column dropdown menu that precedes the subquery filter, select the attribute you want to group and sort your subquery results by.
- Select whether you want to use the IN or NOT IN operator:
- The results from the IN operator only include logs where the attribute value is also found in the subquery results. For example, if you only want to see logs generated by
service:aand is associated to a user who is also one of the top users ofservice:b. - The results from the NOT IN operator exclude logs where the attribute value is found in the subquery results. For example, if you only want to see
status:errorlogs, but also want to filter outstatus:errorlogs where users associated with those logs eventually end up with astatus:successlog. See Filter outdated or superseded logs for a detailed example.
- The results from the IN operator only include logs where the attribute value is also found in the subquery results. For example, if you only want to see logs generated by
- Optionally, reduce the number of subquery attribute values to match against. The default value and maximum value is
1000. Choose between top (highest frequency values) or bottom (lowest frequency values).
Subquery examples
The following are scenarios where you need to use subqueries to get the information you need from your logs.
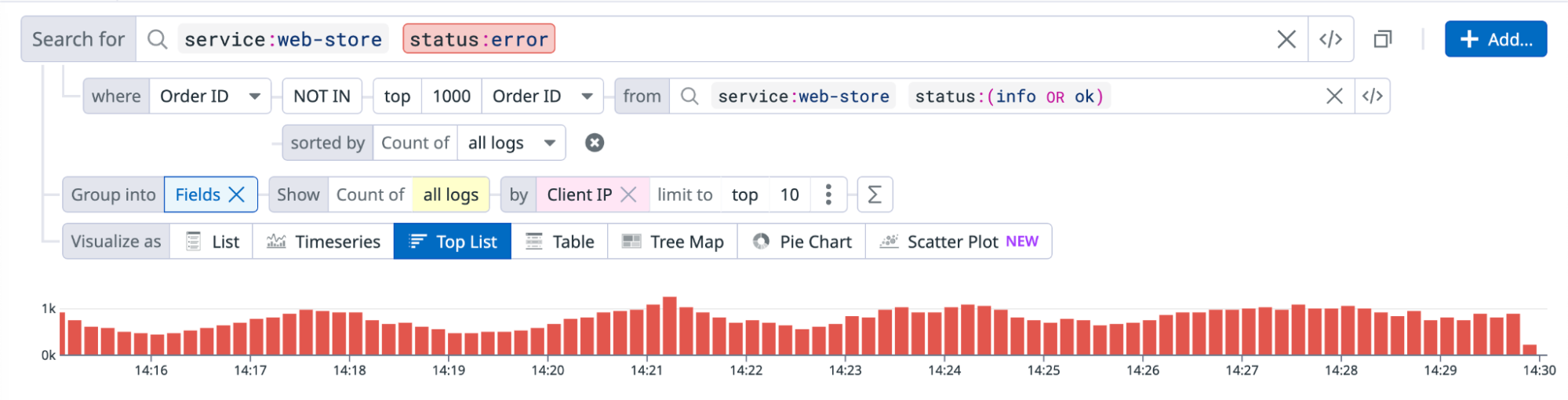
Filter outdated or superseded logs
Assume you operate an e-commerce platform. A log is generated each time one of your customers tries to place an order. You want to analyze your logs to understand the total value of potential purchases lost due to an ongoing issue with your website.
You realize, however, that an order can fail multiple times before successfully completing: meaning for that particular order ID, there are log entries in the search results for both status:error logs and status:success logs. If you extracted lists of unique order IDs from the two queries, this order ID would appear in both. With subqueries, you can obtain a mutually exclusive list.
In this example, you are only interested in logs for orders that did not eventually succeed. To exclude orders that eventually succeeded using the subquery feature:
- Define a subquery for
status:successlogs. - Select the NOT IN operator to exclude orders from the subquery result set.
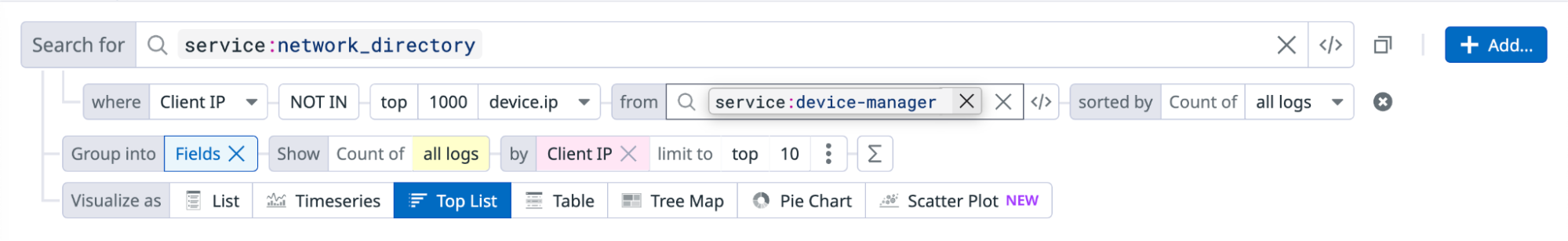
Correlate across different log sources
Assume you have a service named network_directory that monitors all internal network resources and access to those resources within your organization. Log events generated by this service include standard attributes (like host, service, source) and custom attributes like the client’s IP address.
Additionally, you have another device-manager service that tracks all internal assets (infrastructure, employee devices, and so on.)
You are investigating an ongoing attack and observe there is a significant increase in API requests across almost all of your endpoints. You want to first identify IP addresses associated with anomalous request volumes so that you can block them at the firewall level. However, your internal services are some of the largest consumers of these endpoints and you need to exclude them from your query results to avoid mistakenly blocking them.
In this example, use service:network_directory as your main query, and then define a subquery filter for your device-manager service to filter out results from recognized devices.
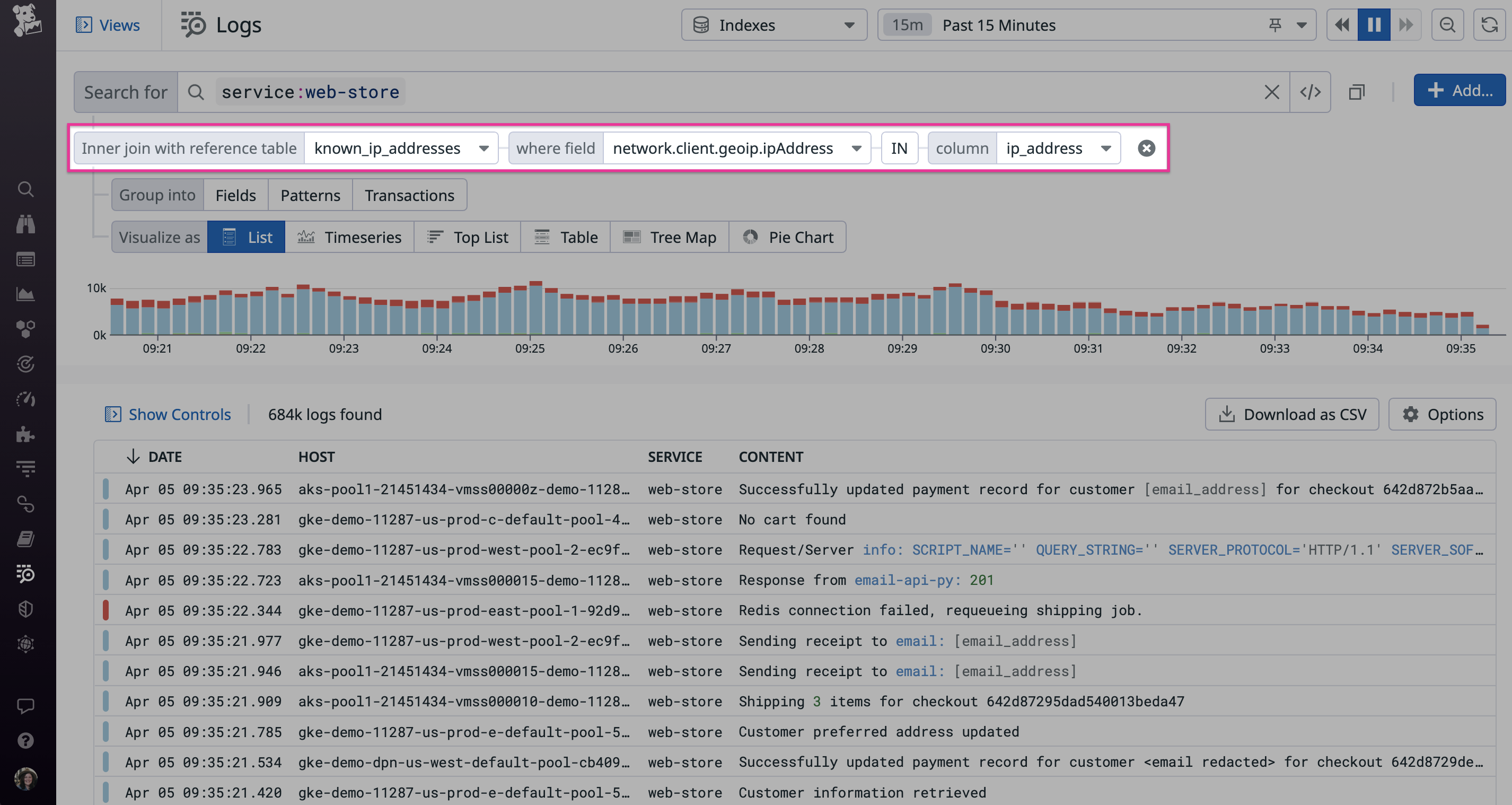
Filter logs based on Reference Tables
Reference Tables are in beta. Reference Tables containing over 40,000 rows cannot be used to filter logs. See Add Custom Metadata with Reference Tables for more information on how to create and manage Reference Tables.
Reference Tables allow you to combine metadata with logs, providing more information to resolve application issues. Add a query filter based on a Reference Table to perform lookup queries. For more information on creating and managing this feature, see the Reference Tables guide.
To apply a query filter with Reference Tables:
- Click the Add button next to the query editor, and then select Join with Reference Table.
- Select your reference table in the dropdown menu.
- Select the log field you want to look for in the reference table.
- Select the IN or NOT IN operator depending on whether you want to find the field value in the specific column.
In the following example, the Reference Table query filter is used to search all recent logs that include a malicious IP address from a threat intel reference table:
Further reading
Documentation, liens et articles supplémentaires utiles: