- 重要な情報
- はじめに
- Datadog
- Datadog サイト
- DevSecOps
- AWS Lambda のサーバーレス
- エージェント
- インテグレーション
- コンテナ
- ダッシュボード
- アラート設定
- ログ管理
- トレーシング
- プロファイラー
- タグ
- API
- Service Catalog
- Session Replay
- Continuous Testing
- Synthetic モニタリング
- Incident Management
- Database Monitoring
- Cloud Security Management
- Cloud SIEM
- Application Security Management
- Workflow Automation
- CI Visibility
- Test Visibility
- Intelligent Test Runner
- Code Analysis
- Learning Center
- Support
- 用語集
- Standard Attributes
- ガイド
- インテグレーション
- エージェント
- OpenTelemetry
- 開発者
- 認可
- DogStatsD
- カスタムチェック
- インテグレーション
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Recommended Monitor
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- サービスのチェック
- IDE インテグレーション
- コミュニティ
- ガイド
- API
- モバイルアプリケーション
- CoScreen
- Cloudcraft
- アプリ内
- Service Management
- インフラストラクチャー
- アプリケーションパフォーマンス
- APM
- Continuous Profiler
- データベース モニタリング
- Data Streams Monitoring
- Data Jobs Monitoring
- Digital Experience
- Software Delivery
- CI Visibility (CI/CDの可視化)
- CD Visibility
- Test Visibility
- Intelligent Test Runner
- Code Analysis
- Quality Gates
- DORA Metrics
- セキュリティ
- セキュリティの概要
- Cloud SIEM
- クラウド セキュリティ マネジメント
- Application Security Management
- AI Observability
- ログ管理
- Observability Pipelines(観測データの制御)
- ログ管理
- 管理
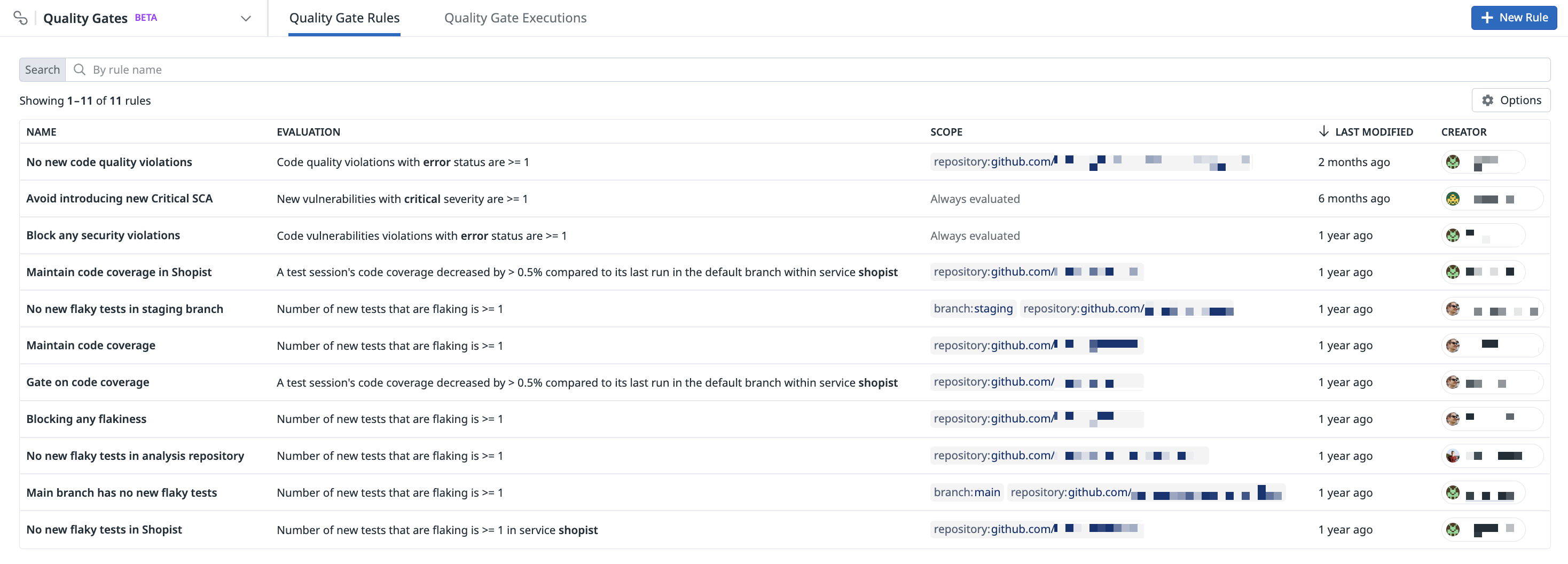
Set up Quality Gate Rules
このページは日本語には対応しておりません。随時翻訳に取り組んでいます。翻訳に関してご質問やご意見ございましたら、お気軽にご連絡ください。
Quality Gates is not available in the selected site () at this time.
Overview
To use Datadog Quality Gates, you can define one or more rules on the Quality Gate Rules page and integrate them in your CI pipeline with the datadog-ci gate evaluate command.
Quality Gates ensures that only the code that meets your quality standards is deployed, automating your quality assurance processes and enhancing software reliability.
Create a rule
To create a Quality Gates rule in Datadog:
Navigate to Software Delivery > Quality Gates > Quality Gate Rules and click + New Rule.
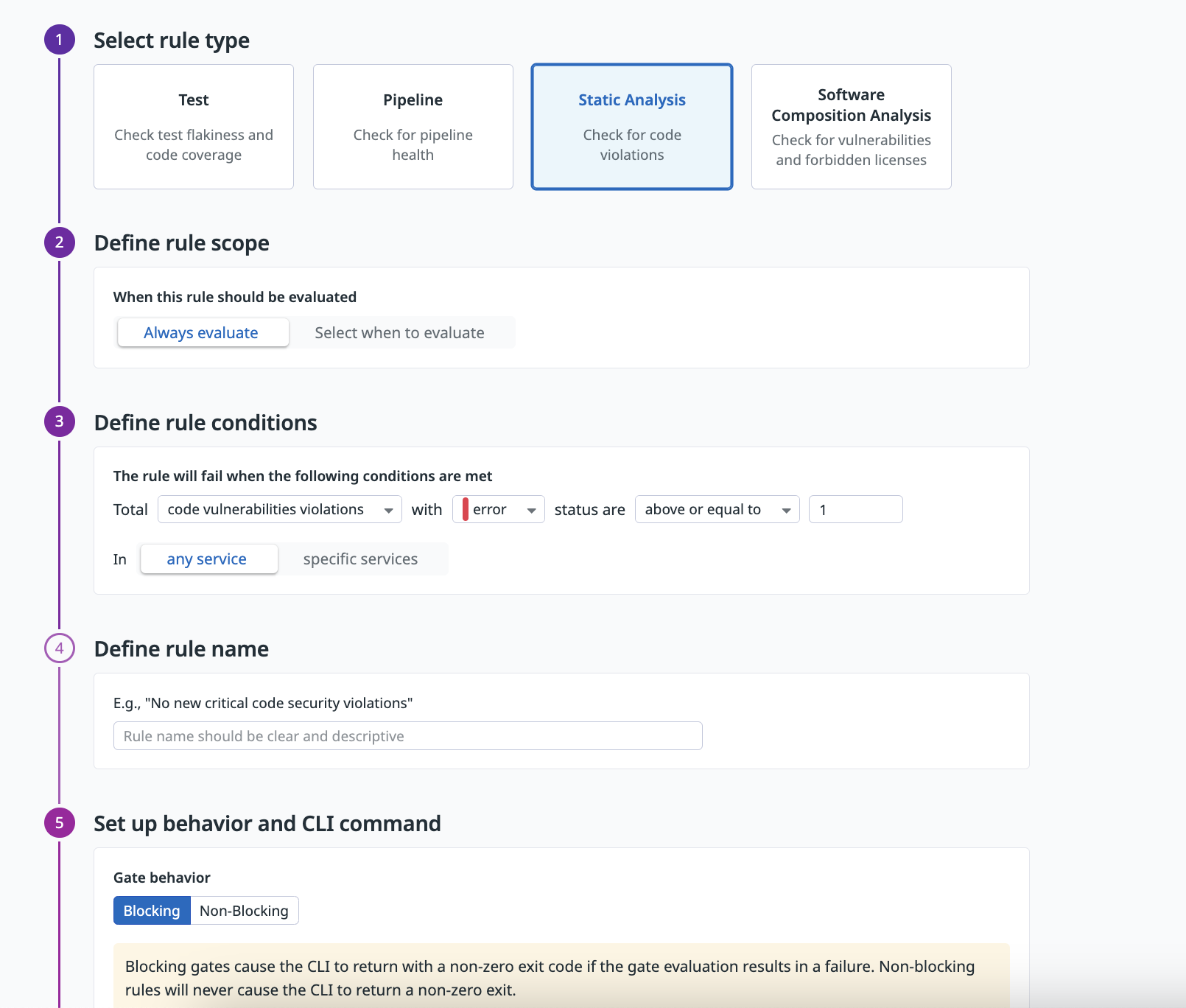
Select a type of rule:
Test,Pipeline,Static Analysis, orSoftware Composition Analysis.Set the rule scope, which defines when the rule should be evaluated, by selecting
Always evaluateorSelect when to evaluate. You can add branches or repositories to include or exclude from the rule scope, or add a custom scope.You can create a rule that is evaluated only on specific repositories and branches. To customize the rule scope, click
Select when to evaluateand specify the branch or repository that should be included or excluded.To add a custom scope (such as a team name), click + Add Filter and select Custom scope. Enter a tag name without spaces (such as
documentationorteam-documentation) and click Add Custom Scope. Enter values that should be included or excluded.When adding a custom scope to a rule, custom scopes must be passed to the
datadog-ci gate evaluatecommand using the--scopeoption. For more information, see Understanding Rule Scopes.Define the rule conditions. The rule condition states in which scenario the rule fails, failing the related pipeline (if the rule is blocking). You can select one of the existing rule conditions for the rule type you have selected. If the rule scope is set to
always evaluate, the rule is evaluated on all repositories and branches.The following example demonstrates how to create a Static Analysis rule that fails when one or more Static Analysis code vulnerability violations with
errorstatus are introduced in a specific commit.Select Static Analysis for the rule type and click
Always evaluatefor the rule scope.In the Define rule conditions section, click New and select
code vulnerabilities violationsfrom the dropdown menu. Then, select theerrorstatus type, selectabove or equal to, and enter the value of1.Specify a rule name that describes the rule that you are creating.
Select whether the rule should block the pipeline when it fails. Non-blocking rules are helpful when you roll out a new rule and want to verify its behavior before making it blocking.
Integrate the Quality Gate rule into your build configuration by including the
datadog-ci gate evaluatecommand.Enable a GitHub status check for your Quality Gate rule by setting the appropriate permissions (such as
Checks: Write) in your GitHub apps. To set this check as blocking in your pull requests, you must click the Required checkbox in your GitHub app’s Protected Branches settings.Click Create Rule.
Integrate Quality Gates in your CI/CD pipeline
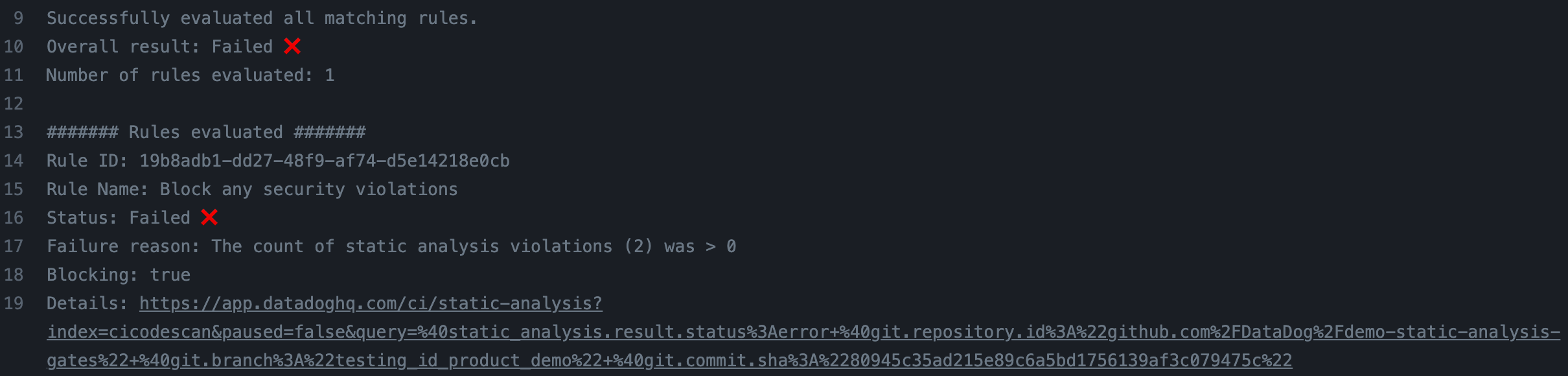
Invoke the Quality Gates evaluation by calling the datadog-ci gate evaluate command. Quality Gates requires datadog-ci version 2.27.0 or later.
For the command to work properly, ensure that events (tests, pipelines, static analysis, and software composition analysis violations) are sent to Datadog before the
datadog-ci gate evaluate command executes. Otherwise, the rules may demonstrate incorrect behavior due to the absence of these events.This command:
- Retrieves all the rules that have rule scopes and custom scopes that match the current pipeline context (the repository, branch, or custom scope(s) passed in the command).
- Evaluates all the matching rules.
- Fails if one or more blocking rules fail, blocking the pipeline.
| Environment Variables | Description |
|---|---|
DD_API_KEY | Point to your Datadog API key. |
DD_APP_KEY | Point to your Datadog application key. The application key must have the Quality Gates Evaluations permission enabled. |
DD_SITE | (Optional) Point to a specific Datadog site (default value is DATADOG_SITE is not supported. |
For example:
DD_SITE= DD_API_KEY=API_KEY DD_APP_KEY=APP_KEY datadog-ci gate evaluate
Configure the behavior of the datadog-ci gate evaluate command using the following flags:
--fail-on-empty- The command fails if no matching rules are found based on the current pipeline context. By default, the command succeeds.
--fail-if-unavailable- The command fails if one or more rules cannot be evaluated because of an internal issue. By default, the command succeeds.
--timeout- The command stops its execution after the specified timeout in seconds. The default timeout is 10 minutes. The command typically completes within a few minutes, but it could take longer.
--no-wait- Skips the default time that the command waits for the events (for example, tests, static analysis violations) to arrive to Datadog. The default wait time makes sure that the events are queryable in Datadog before the rules are executed, avoiding incorrect evaluations. If, in your pipeline, the job containing the
datadog-ci gate evaluatecommand is called several minutes after the related events are sent to Datadog, you can opt to skip this waiting time by specifying the--no-waitflag. However, if used incorrectly, this flag may result in inaccurate rule evaluations.
Add custom scopes to the command by using the --scope option one or more times:
datadog-ci gate evaluate --scope team:backend --scope team:frontend
Check the command logs to see the overall gate evaluation status and information about the rules that were evaluated.
Enable GitHub check creation
You can automatically create a GitHub check for each rule evaluated. The check contains additional information about the rule evaluation, such as the failure reason and the matching events in Datadog. When this feature is enabled, the evaluation results appear directly in GitHub.
To enable GitHub Checks:
- Navigate to the GitHub integration tile. If you do not have this integration set up, or you don’t have a GitHub app within the integration, follow the GitHub integration documentation to set one up.
- Grant
Checks: Writeaccess to the GitHub application.
After the permission is granted, you can see the checks in GitHub.
Note: Re-running a check does not re-run the corresponding Quality Gates rule.
Manage rules
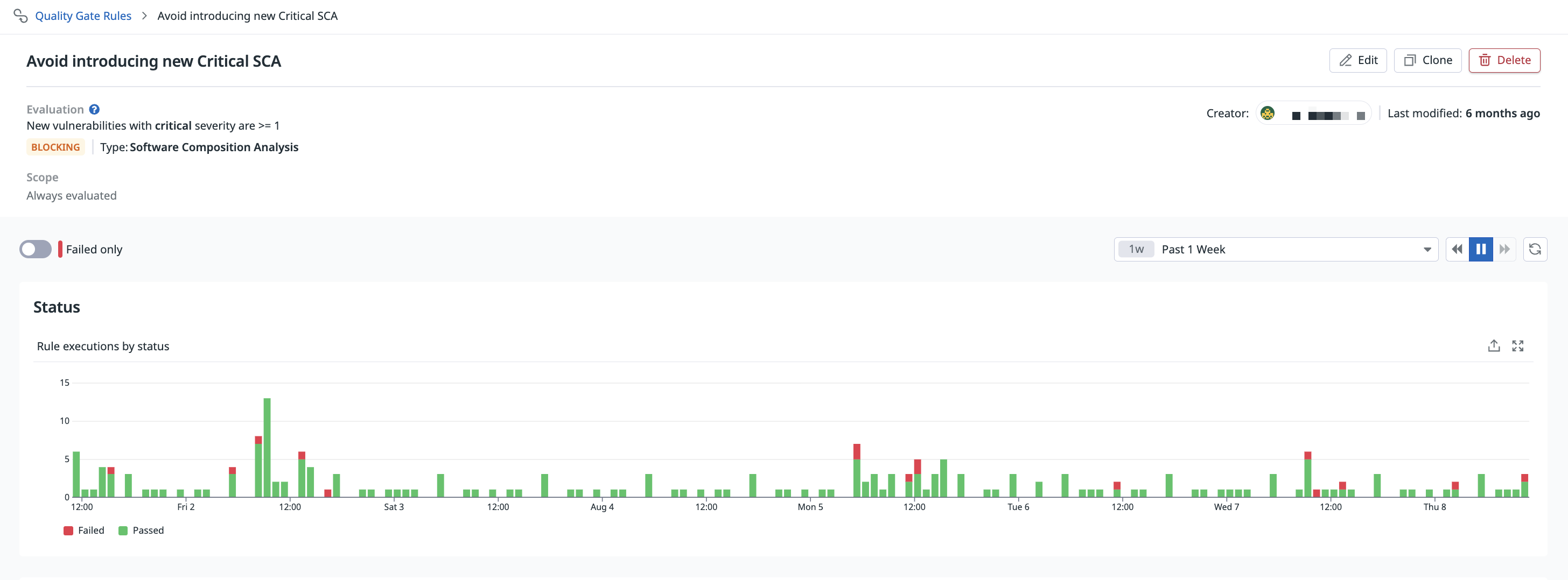
You can edit and delete Quality Gates rules by hovering over a rule on the Quality Gates Rules page.
Alternatively, click on a rule from the list and click the Edit, Clone, or Delete icons.
Permissions
Only users with the quality_gate_rules_write permission can create and edit Quality Gate rules. Users with the quality_gate_rules_read permission can view Quality Gate rules.
For more information, see the RBAC Permissions documentation.
Further reading
お役に立つドキュメント、リンクや記事: