- Essentials
- Getting Started
- Datadog
- Datadog Site
- DevSecOps
- Serverless for AWS Lambda
- Agent
- Integrations
- Containers
- Dashboards
- Monitors
- Logs
- APM Tracing
- Profiler
- Tags
- API
- Service Catalog
- Session Replay
- Continuous Testing
- Synthetic Monitoring
- Incident Management
- Database Monitoring
- Cloud Security Management
- Cloud SIEM
- Application Security Management
- Workflow Automation
- CI Visibility
- Test Visibility
- Test Impact Analysis
- Code Analysis
- Learning Center
- Support
- Glossary
- Standard Attributes
- Guides
- Agent
- Integrations
- OpenTelemetry
- Developers
- Authorization
- DogStatsD
- Custom Checks
- Integrations
- Create an Agent-based Integration
- Create an API Integration
- Create a Log Pipeline
- Integration Assets Reference
- Build a Marketplace Offering
- Create a Tile
- Create an Integration Dashboard
- Create a Recommended Monitor
- Create a Cloud SIEM Detection Rule
- OAuth for Integrations
- Install Agent Integration Developer Tool
- Service Checks
- IDE Plugins
- Community
- Guides
- Administrator's Guide
- API
- Datadog Mobile App
- CoScreen
- Cloudcraft
- In The App
- Dashboards
- Notebooks
- DDSQL Editor
- Sheets
- Monitors and Alerting
- Infrastructure
- Metrics
- Watchdog
- Bits AI
- Service Catalog
- API Catalog
- Error Tracking
- Service Management
- Infrastructure
- Application Performance
- APM
- Continuous Profiler
- Database Monitoring
- Data Streams Monitoring
- Data Jobs Monitoring
- Digital Experience
- Real User Monitoring
- Product Analytics
- Synthetic Testing and Monitoring
- Continuous Testing
- Software Delivery
- CI Visibility
- CD Visibility
- Test Optimization
- Code Analysis
- Quality Gates
- DORA Metrics
- Security
- Security Overview
- Cloud SIEM
- Cloud Security Management
- Application Security Management
- AI Observability
- Log Management
- Observability Pipelines
- Log Management
- Administration
AWS CloudTrail
Overview
See AWS Configuration for Cloud SIEM if you are setting up AWS CloudTrail for Cloud SIEM.
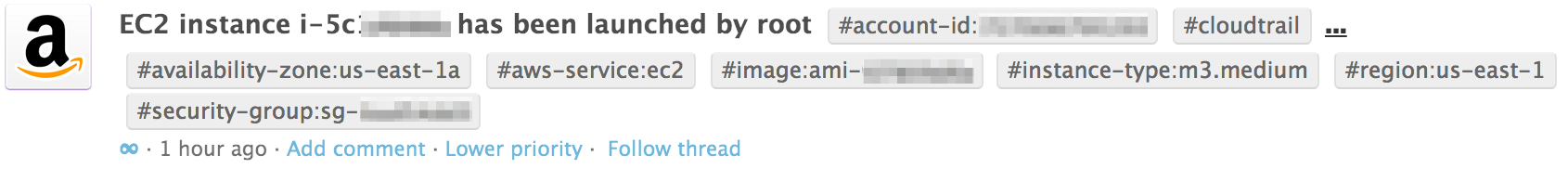
AWS CloudTrail provides an audit trail for your AWS account. Datadog reads this audit trail and creates events. Search your Datadog events explorer for these events or use them for correlation on your dashboards. Here is an example of a CloudTrail event:
For information on other AWS services, see the Amazon Web Services integration page
Setup
Installation
If you haven’t already, set up the Amazon Web Services integration first.
Event collection
Note: The Datadog CloudTrail integration requires events to be collected in a CloudTrail bucket.
Add the following permissions to your Datadog IAM policy to collect AWS CloudTrail events. For more information on CloudTrail policies, see the AWS CloudTrail API Reference. CloudTrail also requires some S3 permissions to access the trails. These are required on the CloudTrail bucket only. For more information on Amazon S3 policies, see the Amazon S3 API Reference.
AWS Permission Description cloudtrail:DescribeTrailsLists trails and the s3 bucket the trails are stored in. cloudtrail:GetTrailStatusSkips inactive trails. s3:ListBucketLists objects in the CloudTrail bucket to get available trails. s3:GetBucketLocationObtains the bucket’s region to download trails. s3:GetObjectFetches available trails. organizations:DescribeOrganizationReturns information about an account’s organization (required for org trails). Add this policy to your existing main Datadog IAM policy:
{ "Sid": "AWSDatadogPermissionsForCloudtrail", "Effect": "Allow", "Principal": { "AWS": "<ARN_FROM_MAIN_AWS_INTEGRATION_SETUP>" }, "Action": ["s3:ListBucket", "s3:GetBucketLocation", "s3:GetObject"], "Resource": [ "arn:aws:s3:::<YOUR_S3_CLOUDTRAIL_BUCKET_NAME>", "arn:aws:s3:::<YOUR_S3_CLOUDTRAIL_BUCKET_NAME>/*" ] }Note: The principal ARN is the one listed during the installation process for the main AWS integration. See the Resources section of How AWS CloudTrail works with IAM for more information on CloudTrail resource ARNs. If you are updating your policy (as opposed to adding a new one), you don’t need the
SIDor thePrincipal.Install the Datadog - AWS CloudTrail integration: On the integration page, choose the types of events to show as normal priority (the default filter) in the Datadog events explorer. The accounts you configured in the Amazon Web Services page are also shown here. If you would like to see other events that are not mentioned here, contact Datadog support.
Log collection
Enable logging
In AWS CloudTrail, create a Trail and select an S3 bucket to write the logs in.
Send logs to Datadog
- If you haven’t already, set up the Datadog Forwarder Lambda function in your AWS account.
- Once set up, go to the Datadog Forwarder Lambda function. In the Function Overview section, click Add Trigger.
- Select the S3 trigger for the Trigger Configuration.
- Select the S3 bucket that contains your CloudTrail logs.
- Leave the event type as
All object create events. - Click Add to add the trigger to your Lambda.
Go to the Log Explorer to start exploring your logs.
For more information on collecting AWS Services logs, see Send AWS Services Logs with the Datadog Lambda Function.
Data Collected
Metrics
The AWS CloudTrail integration does not include any metrics.
Events
The AWS CloudTrail integration creates many different events based on the AWS CloudTrail audit trail. All events are tagged with #cloudtrail in your Datadog events explorer. You can set their priority in the integration configuration.
CloudTrail events that can be set to a normal priority (they appear in the Event Explorer under the default filter):
- apigateway
- autoscaling
- cloudformation
- cloudfront
- cloudsearch
- cloudtrail
- codedeploy
- codepipeline
- config
- datapipeline
- ds
- ec2
- ecs
- elasticache
- elasticbeanstalk
- elasticfilesystem
- elasticloadbalancing
- elasticmapreduce
- iam
- kinesis
- lambda
- monitoring
- opsworks
- rds
- redshift
- route53
- s3
- ses
- signin
- ssm
Service Checks
The AWS CloudTrail integration does not include any service checks.
Troubleshooting
The CloudTrail tile is missing or there are no accounts listed
You need to first configure the Amazon Web Services integration. Then the CloudTrail tile can be configured.