- Esenciales
- Empezando
- Datadog
- Sitio web de Datadog
- DevSecOps
- Serverless para Lambda AWS
- Agent
- Integraciones
- Contenedores
- Dashboards
- Monitores
- Logs
- Rastreo de APM
- Generador de perfiles
- Etiquetas (tags)
- API
- Catálogo de servicios
- Session Replay
- Continuous Testing
- Monitorización Synthetic
- Gestión de incidencias
- Monitorización de bases de datos
- Cloud Security Management
- Cloud SIEM
- Application Security Management
- Workflow Automation
- CI Visibility
- Test Visibility
- Intelligent Test Runner
- Análisis de código
- Centro de aprendizaje
- Compatibilidad
- Glosario
- Atributos estándar
- Guías
- Agent
- Uso básico del Agent
- Arquitectura
- IoT
- Plataformas compatibles
- Recopilación de logs
- Configuración
- Configuración remota
- Automatización de flotas
- Actualizar el Agent
- Solucionar problemas
- Detección de nombres de host en contenedores
- Modo de depuración
- Flare del Agent
- Estado del check del Agent
- Problemas de NTP
- Problemas de permisos
- Problemas de integraciones
- Problemas del sitio
- Problemas de Autodiscovery
- Problemas de contenedores de Windows
- Configuración del tiempo de ejecución del Agent
- Consumo elevado de memoria o CPU
- Guías
- Seguridad de datos
- Integraciones
- OpenTelemetry
- Desarrolladores
- Autorización
- DogStatsD
- Checks personalizados
- Integraciones
- Crear una integración basada en el Agent
- Crear una integración API
- Crear un pipeline de logs
- Referencia de activos de integración
- Crear una oferta de mercado
- Crear un cuadro
- Crear un dashboard de integración
- Crear un monitor recomendado
- Crear una regla de detección Cloud SIEM
- OAuth para integraciones
- Instalar la herramienta de desarrollo de integraciones del Agente
- Checks de servicio
- Complementos de IDE
- Comunidad
- Guías
- API
- Aplicación móvil de Datadog
- CoScreen
- Cloudcraft
- En la aplicación
- Dashboards
- Notebooks
- Editor DDSQL
- Hojas
- Monitores y alertas
- Infraestructura
- Métricas
- Watchdog
- Bits AI
- Catálogo de servicios
- Catálogo de APIs
- Error Tracking
- Gestión de servicios
- Objetivos de nivel de servicio (SLOs)
- Gestión de incidentes
- De guardia
- Gestión de eventos
- Gestión de casos
- Workflow Automation
- App Builder
- Infraestructura
- Universal Service Monitoring
- Contenedores
- Serverless
- Monitorización de red
- Coste de la nube
- Rendimiento de las aplicaciones
- APM
- Términos y conceptos de APM
- Instrumentación de aplicación
- Recopilación de métricas de APM
- Configuración de pipelines de trazas
- Correlacionar trazas (traces) y otros datos de telemetría
- Trace Explorer
- Observabilidad del servicio
- Instrumentación dinámica
- Error Tracking
- Seguridad de los datos
- Guías
- Solucionar problemas
- Continuous Profiler
- Database Monitoring
- Gastos generales de integración del Agent
- Arquitecturas de configuración
- Configuración de Postgres
- Configuración de MySQL
- Configuración de SQL Server
- Configuración de Oracle
- Configuración de MongoDB
- Conexión de DBM y trazas
- Datos recopilados
- Explorar hosts de bases de datos
- Explorar métricas de consultas
- Explorar ejemplos de consulta
- Solucionar problemas
- Guías
- Data Streams Monitoring
- Data Jobs Monitoring
- Experiencia digital
- Real User Monitoring
- Monitorización del navegador
- Configuración
- Configuración avanzada
- Datos recopilados
- Monitorización del rendimiento de páginas
- Monitorización de signos vitales de rendimiento
- Monitorización del rendimiento de recursos
- Recopilación de errores del navegador
- Rastrear las acciones de los usuarios
- Señales de frustración
- Error Tracking
- Solucionar problemas
- Monitorización de móviles y TV
- Plataforma
- Session Replay
- Exploración de datos de RUM
- Feature Flag Tracking
- Error Tracking
- Guías
- Seguridad de los datos
- Monitorización del navegador
- Análisis de productos
- Pruebas y monitorización de Synthetics
- Continuous Testing
- Entrega de software
- CI Visibility
- CD Visibility
- Test Visibility
- Configuración
- Tests en contenedores
- Búsqueda y gestión
- Explorador
- Monitores
- Flujos de trabajo de desarrolladores
- Cobertura de código
- Instrumentar tests de navegador con RUM
- Instrumentar tests de Swift con RUM
- Detección temprana de defectos
- Reintentos automáticos de tests
- Correlacionar logs y tests
- Guías
- Solucionar problemas
- Intelligent Test Runner
- Code Analysis
- Quality Gates
- Métricas de DORA
- Seguridad
- Información general de seguridad
- Cloud SIEM
- Cloud Security Management
- Application Security Management
- Observabilidad de la IA
- Log Management
- Observability Pipelines
- Gestión de logs
- Administración
- Gestión de cuentas
- Seguridad de los datos
- Sensitive Data Scanner
- Ayuda
Connect your AWS Account to Cloudcraft
This page is not yet available in Spanish. We are working on its translation.
If you have any questions or feedback about our current translation project, feel free to reach out to us!
If you have any questions or feedback about our current translation project, feel free to reach out to us!
Connecting your AWS accounts to Cloudcraft allows you to visualize your infrastructure by reverse-engineering the live environment’s service relationships into a system architecture diagram. In addition to automatically generating diagrams, a budget model will also be created, and your imported components will display live status data directly in your diagrams. There is no limit on the number of AWS accounts you can connect to Cloudcraft.
Note: For AWS organizations, you must manually add the Cloudcraft role to each individual account in the organization.
This article walks you through connecting your AWS account to Cloudcraft.
Datadog users can bypass this process by connecting their Datadog account to Cloudcraft. For more information, see Datadog Integration.
Requirements
- A Cloudcraft user with the Owner or Administrator role.
- An active Cloudcraft Pro subscription.
- An AWS account with permission to create IAM roles.
How the live AWS sync works
Cloudcraft uses a cross-account role to securely access your AWS environment. As a result, you need to create a Cloudcraft-specific, read-only role in your AWS account. This role can be revoked at any time.
If having a read-only role with access to all components isn’t permissible or violates your company’s policies, you also have the option to attach a stricter minimal access policy, only giving read-only access to the resources you want to use with Cloudcraft, further minimizing the amount of data the role can access.
Cloudcraft doesn’t keep any of the live data from your AWS environment. Instead, it stores ARNs, which are unique identifiers for resources in AWS. This allows the application to link live data to components at runtime.
The data from your AWS environment is streamed in real-time to your browser via Cloudcraft’s own AWS environment via role-based access, and is only stored client-side while you are using the application. When you close the application, the live data is deleted.
While not having write access to your account prevents Cloudcraft from offering certain features—like deleting an EC2 instance on both the diagram and your account—it’s simply a more secure approach.
Cloudcraft implements rigorous security processes and controls for the SOC2 compliance program. You can read more about Cloudcraft’s security program and controls on the security page.
Manage AWS accounts
Add account
- In Cloudcraft, navigate to User > AWS accounts.
- At the bottom of the modal, click Add AWS Account.
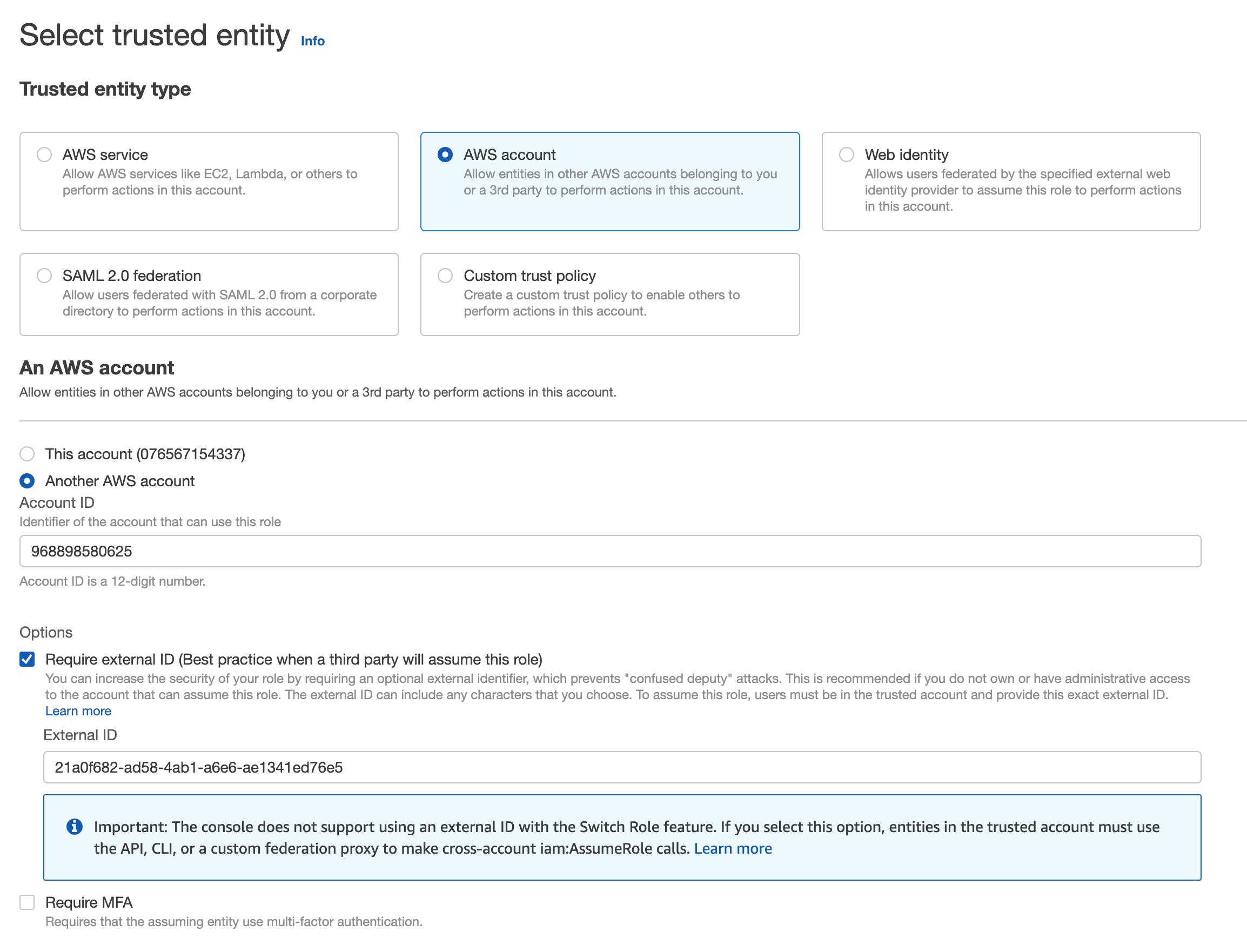
- The next page provides step-by-step instructions. Click Open the AWS IAM Console to the Create Role page to configures the read-only IAM role in AWS.
If you can't access the Create Role page, you may lack AdministrativeAccess or sufficient IAM permissions to create a new IAM role. If this is the case, contact your AWS account's administrator and have them complete the following steps.
- On the Create role page in AWS, leave Require MFA unchecked, and click Next.
Require MFA must be disabled as it's not applicable for system-to-system access where there is no human involved. Access is instead protected by being limited to access from the Cloucraft AWS account.
- Next, add permissions policies to your role. Type ReadOnlyAccess in the search box and press Enter to filter policies by name.
- Select the ReadOnlyAccess policy that provides read-only access to AWS services and resources, then click Next.
- Enter a name and description for the IAM role. You can also add tags to organize, track, or control access for the role. Tagging your role is optional. For tagging best practices, see Best Practices for Tagging AWS Resources.
- Click Create role.
- Select the
cloudcraftrole from the list of roles. On the Summary page, copy the Role ARN.
- In Cloudcraft, paste the ARN in the Role ARN field, and enter a name for your account.
- Optionally, configure team access by clicking the blue button beneath Team access and selecting the teams you want to share access to the AWS account with.
- Click Save Account.
Edit account
To edit an account, click the gray pencil icon to the left of the account you want to edit. You can change details of the account, such as the name, ARN, and team access.
When you are done, click Save Account.
Remove account
To remove an account, click the trash can icon to the right of the account you want to remove, then click Remove.